practical malware Analysis
Lab01-1
1. Upload the files to http://www.VirusTotal.com/ and view the reports. Does either file match any existing antivirus signatures?
- lab01-01.exe: has a 54/71 detection rate
- lab01-01.dll: has a 45/71 detection rate
2. When were these files compiled?
using pestido.exe I can see compiler-stamp for
- lab01-01.exe: Sun Dec 19 16:16:19 2010
- lab01-01.dll: Sun Dec 19 16:16:38 2010
3. Are there any indications that either of these files is packed or obfuscated? If so, what are these indicators?
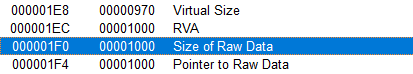
the file has an entropy = 1.954, and I didn’t see any function or imports tell me it’s packed. Using PEview we can see the virtual size is close to the raw size of the files.
4. Do any imports hint at what this malware does? If so, which imports are they?
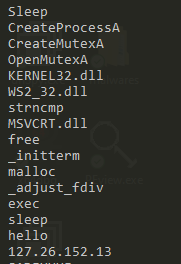
After analysis of Lab01-10.exe and Lab01-01.dll I got some interesting functions imported:
lab01-01.dll
kerne132.dll
- CreateMutexA()
- CreateProcessA()
- Sleep()
MSVCRT.dll
- strncmp()
WS2_32.dll
Based on this we can infer that the dll would likely spawn a new process and sleep (pause execution) at some stage.
lab01-01.exe
kerne132.dll
- CopyFile
- FindFirstFile
- FindNextFile
Based on that I guess the malware author wants to search for a specific file from file system and copy it.
5. Are there any other files or host-based indicators that you could look for on infected systems?
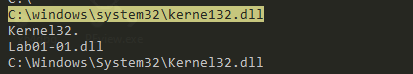
here we can see the file “C:\windows\system32\kerne132.dll” is close to kernel32.dll he uses ‘1’ instead of ‘l’ it is likely malicious.
6. What network-based indicators could be used to find this malware onvinfected machines?
by analyzing strings in lab01-01.dll I found that the IP address can be a network-based indicator 127.26.152.13.
7. What would you guess is the purpose of these files?
I guess that the executable is used to run the DLL which acts as a backdoor. Based on the imports it’s possible the executable searches to see if C:\windows\system32\kerne132.dll exists, and if it doesn’t it may attempt to copy the malicious DLL to C:\windows\system32\kerne132.dll, it likely contacts a C2 server at
127.26.152.13.
Lab01-2
1.Upload the Lab01-02.exe file to http://www.VirusTotal.com/. Does it match any existing antivirus definitions?
55/71 detection rate
2. Are there any indications that this file is packed or obfuscated? If so, what are these indicators? If the file is packed, unpack it if possible.
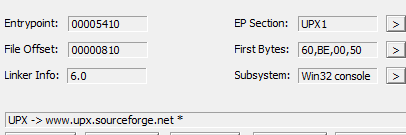
there are some indicators like the PEIDshow me the file packed by UPX encryption in section .text like DIE tell me and there are some functions that indicate the packed like:
Was able to unpack using the UPX command line utility:
upx -d -o Lab01-02_unpacked.exe Lab01-02.exe
Ultimate Packer for eXecutables
Copyright (C) 1996 - 2013
UPX 3.09w Markus Oberhumer, Laszlo Molnar & John Reiser Feb 18th 2013
File size Ratio Format Name
-------------------- ------ ----------- -----------
16384 <- 3072 18.75% win32/pe Lab01-02_unpacked.exe
Unpacked 1 file.
3. Do any imports hint at this program’s functionality? If so, which imports are they and what do they tell you?
By using Dependency Walker I found some DLLs that import some functions like
KERNEL32.DLL
- SystemTimeToFileTime
- GetModuleFileNameA
- CreateMutexA
- CreateThread
- SetWaitableTimer
ADVAPI32.DLL
- CreateServiceA
- StartServiceCtrlDispatcherA
- OpenSCManagerA
WININET.DLL
- InternetOpenUrlA
- InternetOpenA
Based on that the malware creates a thread, service, and communicates over the network.
4. What host- or network-based indicators could be used to identify this malware on infected machines?
Looking at the strings of this file shows 2 interesting strings malservice and http://w
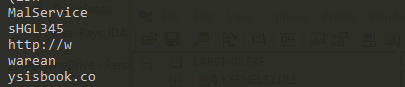
based on that I guess the malware is searching hosts for a scheduled service called malsevice and looking for hosts connected to http://www.malwareanalysisbook.com.
Lab01-3
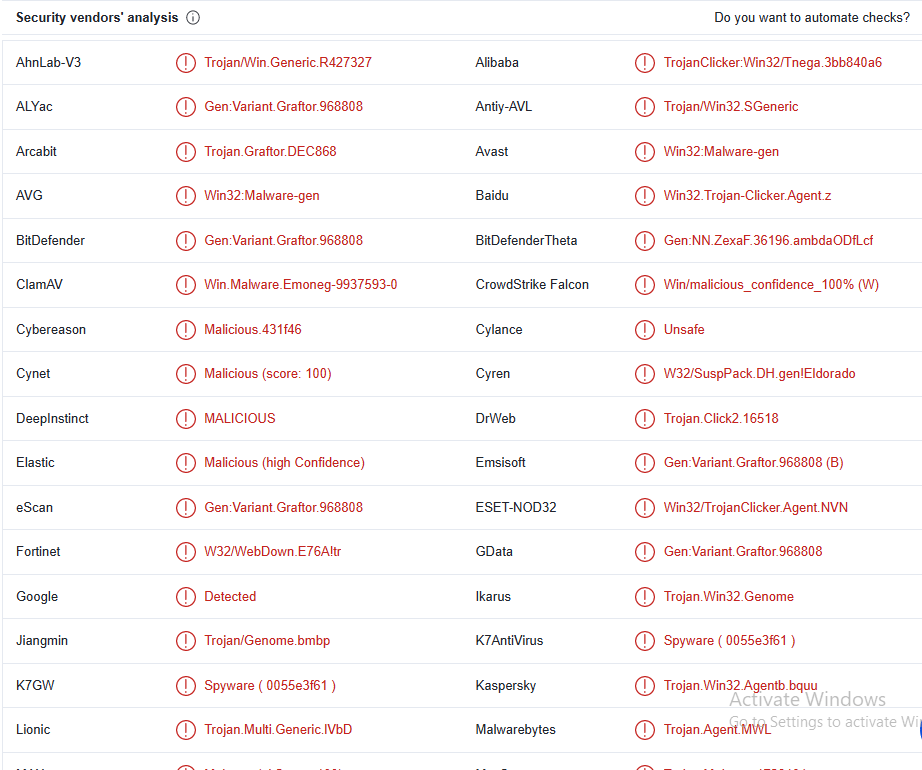
1.Upload the Lab01-03.exe file to http://www.VirusTotal.com/. Does it match any existing antivirus definitions?
there are 60/71 detection rates.
2. Are there any indications that this file is packed or obfuscated? If so, what are these indicators? If the file is packed, unpack it if possible.
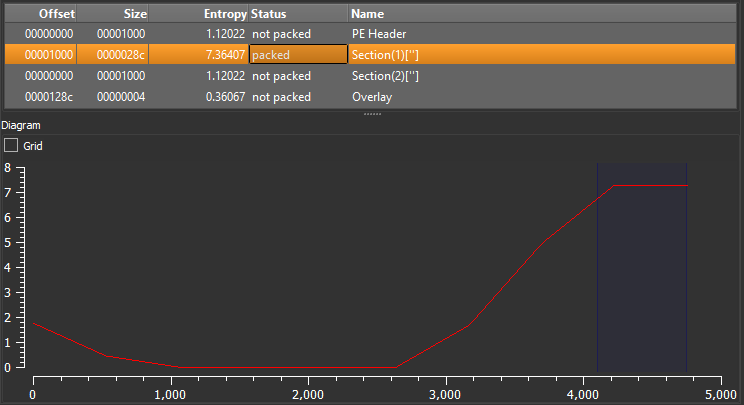
By using DIE.EXE we found ‘section(1)’ packed with high entropy = 7.36407,
if we look at Dependency Walker we see kernel.dll that calls functions that are a good indicator to tell us it’s packed:
And by using PIED.EXE we can find the technique that was used to pack the file ‘FSG technique’.
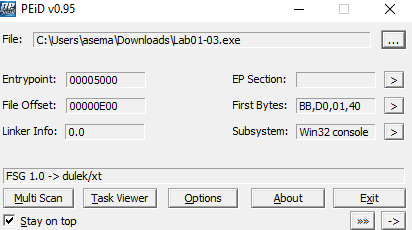
To unpack it follow me step by step: we unpacked it by using ollydpg.
Let’s try to find the OEP with options > debugging options > SFX > Stop at entry of self-extractor: after running the program the entry point is 00401090.
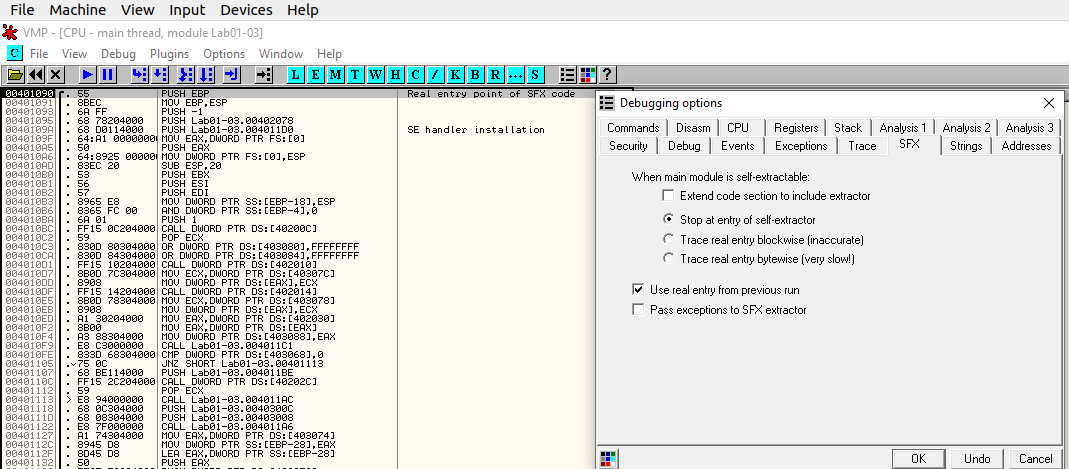
It seems to be the beginning of a function, which confirms that we are likely to have found the OEP. Let’s dump the process (Plugins > OllyDumpEX > Dump process):
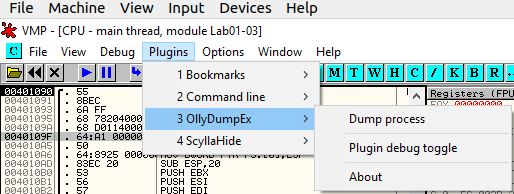
Accept the default values and click on the Dump button. We’re done.
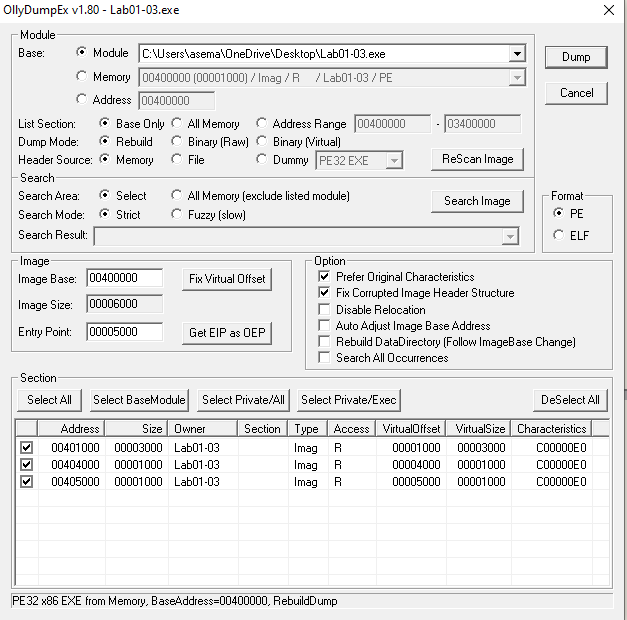
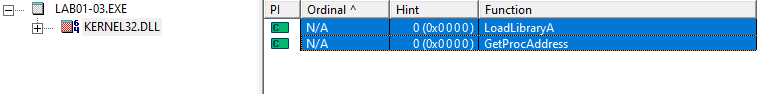
3. Do any imports hint at this program’s functionality? If so, which imports are they and what do they tell you?
The only visible imports are used for unpacking.
KERNEL32.DLL
- LoadLibraryA
- GetProcAddress
4. What host- or network-based indicators could be used to identify this malware on infected machines?
After unpacking I found some strings and URLs that can a good indicator could identify this malware on infected machines:
- http://www.malwareanalysisbook.com/ad.html
- LoadLibrary
- GetProcAddress
- !Windows Program
- OLEAUT32.dll
Lab01-4
1.Upload the Lab01-04.exe file to http://www.VirusTotal.com/. Does it match any existing antivirus definitions?
there are 59/71 detection rates.
2. Are there any indications that this file is packed or obfuscated? If so, what are these indicators? If the file is packed, unpack it if possible.
There are no indications this file is packed or obfuscated.
3. When was this program compiled?
By using pestido.exe I can see compiler-stamp for lab01-04.exe is compiler-stamp, Fri Aug 30 22:26:59 2019.
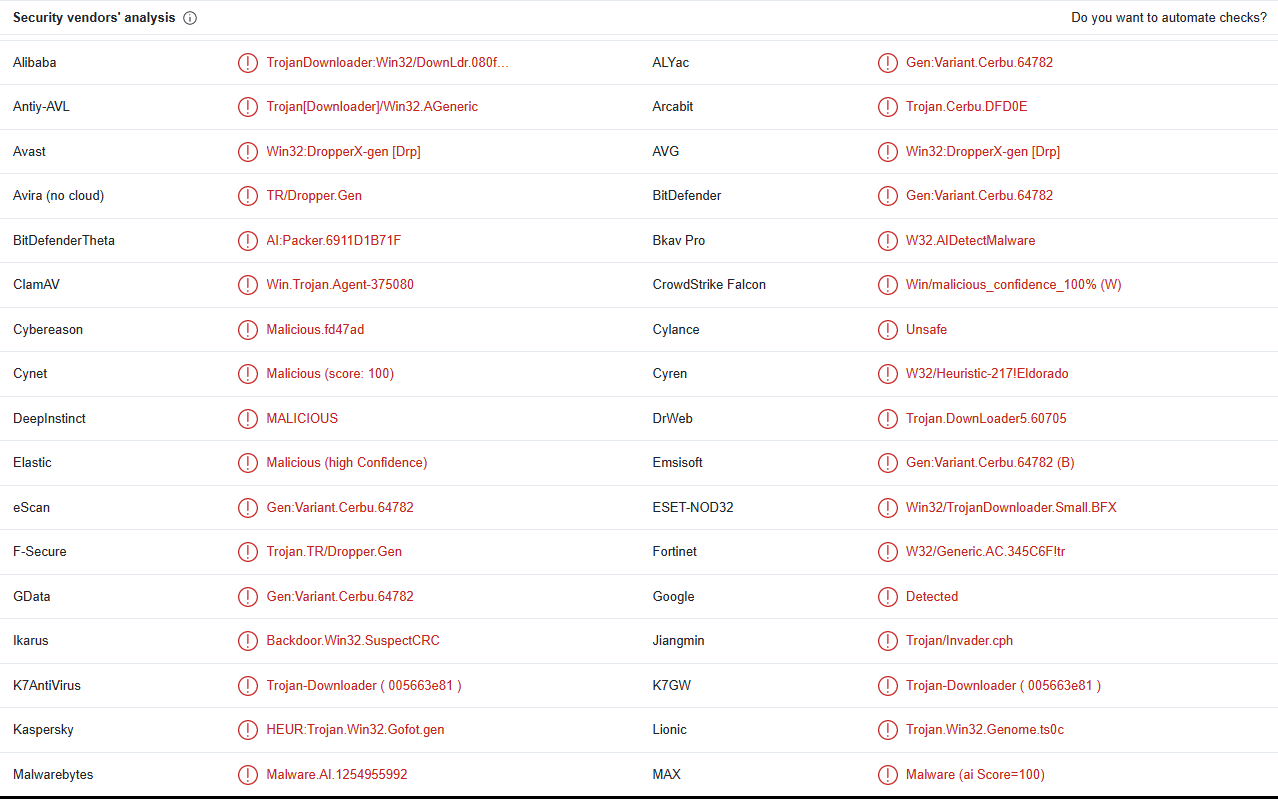
4. Do any imports hint at this program’s functionality? If so, which imports are they and what do they tell you?
Based on the imports from Kernel32 we can see that this will load resources from the file’s resource section and write files to disk. Based on the GetWindowsDirectory function we can assume this will write files to the system directory, and will then execute them due to the WinExec function.
5. What host- or network-based indicators could be used to identify this malware on infected machines?
there are some functions and URLs that can be good indicators like:
- URLDownloadToFileA
- http://www.practicalmalwareanalysis.com/updater.exe
The strings also indicate the below network-based URL which may be where a malware updater or second-stage payload is pulled from:
- \system32\wupdmgrd.exe
- \winup.exe
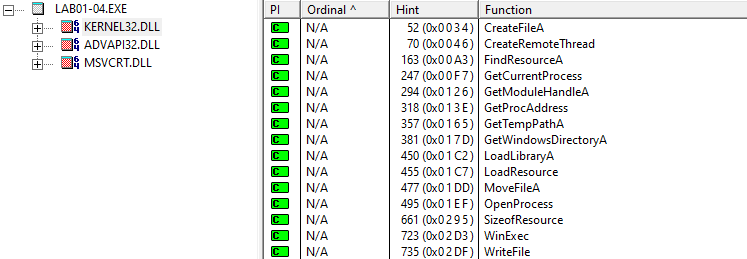
6. This file has one resource in the resource section. Use Resource Hacker to examine that resource, and then use it to extract the resource. What can you learn from the resource?
Looking at this resource through Resource Hacker, we can see that it has a header that indicates it is executable.
Lab03_1
1. What are this malware’s imports and strings?
imports:
- ExitProcess
strings:
- .text
- .data
- ExitProcess
- kernel32.dll
- advpack
- StubPath
- SOFTWARE\Classes\http\shell\open\commandV
- Software\Microsoft\Active Setup\Installed Components\
- www.practicalmalwareanalysis.com A URL there is possibly used for downloads.
- admin
- VideoDriver
- WinVMX32-
- vmx32to64.exe points to a possible malicious executable.
- SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
- AppData
- advapi32
- CONNECT %s:%i HTTP/1.0
- The CurrentVersion\Run registry key indicates that something new will start with Windows.
2. What are the malware’s host-based indicators?
- Created a registry entry in CurrentVersion\Run for the created file, so it starts at boot.
- File: C:\WINDOWS\System32\vmx32to64.exe
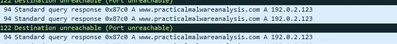
3. Are there any useful network-based signatures for this malware? If so, what are they?
wire shark can find a lot of signatures like the URL=www.practicalmalwareanalysis.com.
Lab03_2
1. How can you get this malware to install itself?
by using PE viewer and PE-bear I found some exports of the dll the malware can use to install itself like:
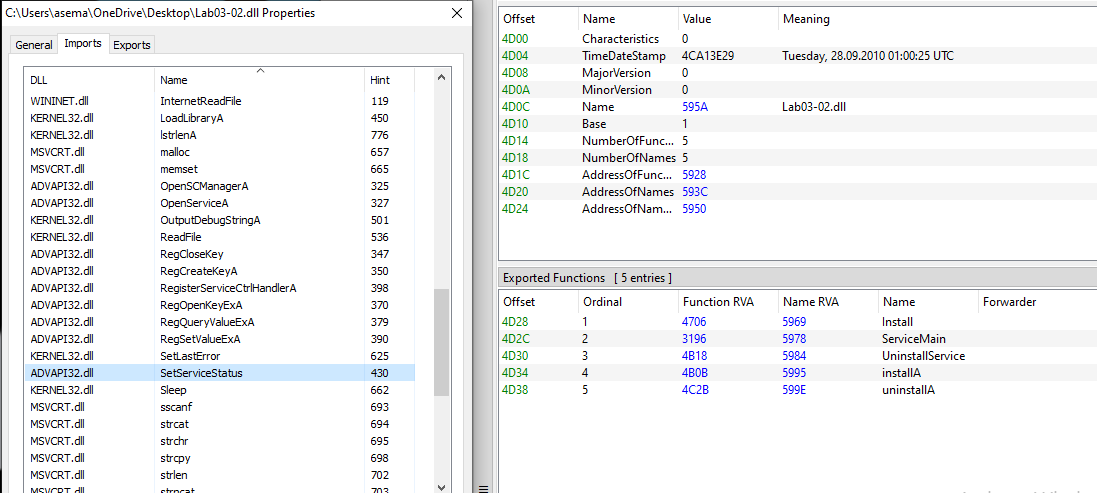
this DLL needs to be installed as a service.
if you need to run dll we are able to use rundll32.exe and the install exported function to execute this dll and install it as a service.
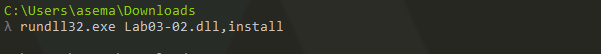
2. How would you get this malware to run after installation?
Started and ended the service with the following command:
- sc start IPRIP
- net start IPRIP
3. How can you find the process under which this malware is running?
Had Process Explorer running when the service started. Searched for the string Lab03-02.dll in Process Explorer, and came up with the process svchost.exe.This instance of svchost.exe is also hosting other services
4. Which filters could you set in order to use procmon to glean information?
we can filter by the Process ID to collect information only on the svchost process responsible for running this malware.
5. What are the malware’s host-based indicators?
- The IPRIP service
- Intranet Network Awareness (INA+) Collects and stores network configuration and location information and notifies applications when this information changes.
- HKLM\SYSTEM\CurrentControlSet\Services\IPRIP\Parameters\/v servicedll
6. Are there any useful network-based signatures for this malware?
- DNS queries for practicalmalwareanalysis.com
- HTTP GET requests to practicalmalwareanalysis.com/serve.html
- HTTP request with a user agent that includes the stringWindows XP 6.11
- Packets to 80/tcp that match the periodic transmissions’ unchanging payload bytes.
The service sends a DNS requests for practicalmalwareanalysis.com, Service sends a single HTTP GET request for /serve.html.
Lab03_3
1. What do you notice when monitoring this malware with Process Explorer?
I notice lab03-03.exe creates a console window host and host process for Windows service that calls conhost.exe and svchost.exe and then terminates itself from the device after creating a new host process that still running in the device:


2. Can you identify any live memory modifications?
Looking at svchost’s properties in Process Explorer allows you to see that malware creates a file called practicalmaleareanalysis.log, [BACKSPACE], and[CAPS LOCK], suggestive of a keylogger from these strings.
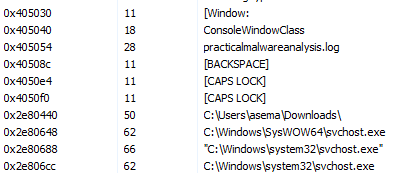
3. What are the malware’s host-based indicators?
We can see both in memory and on disk that the malware creates a file called ‘practicalmalwareanalysis.log’ containing strings that match those found in the malicious svchost.exe.
4. What is the purpose of this program?
From all of this, the malware used as a keylogger gets elevated privileges via process replacement of svchost.exe, Guessing that it uses hooking to capture keystrokes.
Lab03_4
1. What happens when you run this file?
The program did nothing, by using procmon I can see the malware do a lot of events and in the end, it creates a process that can delete itself:
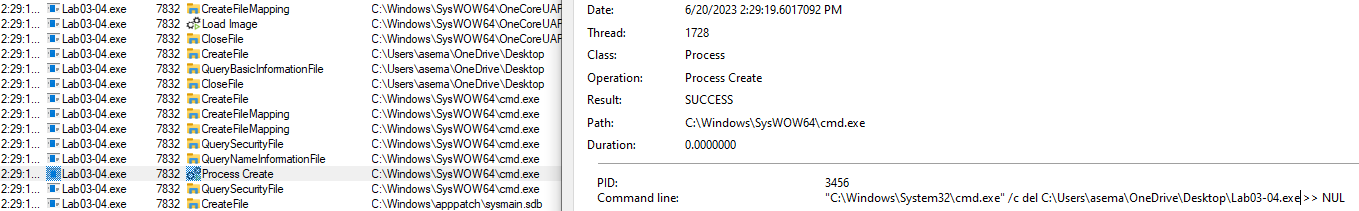
2. What is causing the roadblock in dynamic analysis?
The program deletes itself from the hard drive, I think this is one of the anti-debugging techniques that realize the malware in a virtual machine
3. Are there other ways to run this program?
In a debugger like ida.
Lab05_1
1. What is the address of DllMain?
we can found the function address by open options > General > Line Prefixes, and we get the adress function DllMain 100151B8
2. Use the Imports window to browse to gethostbyname. Where is the import located?
By viewing imports, search about gethostbyname and we found the import located is 100163CC
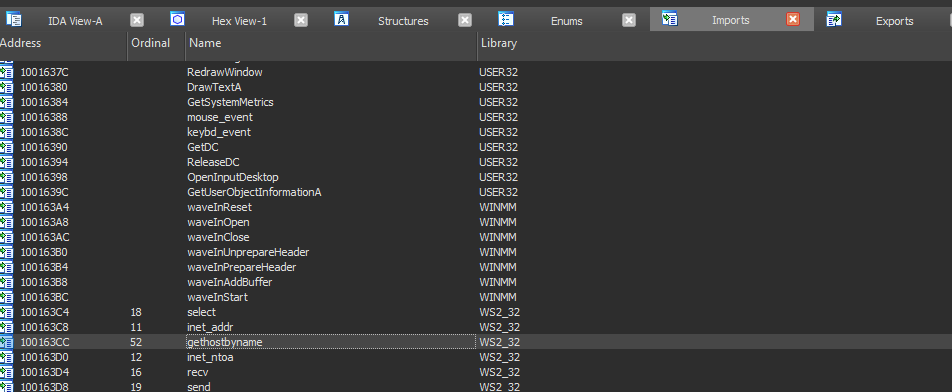
3. How many functions call gethostbyname?
by going to the gethostbyname and clicking right on the mouse and going to jump to xref to operand or just click X
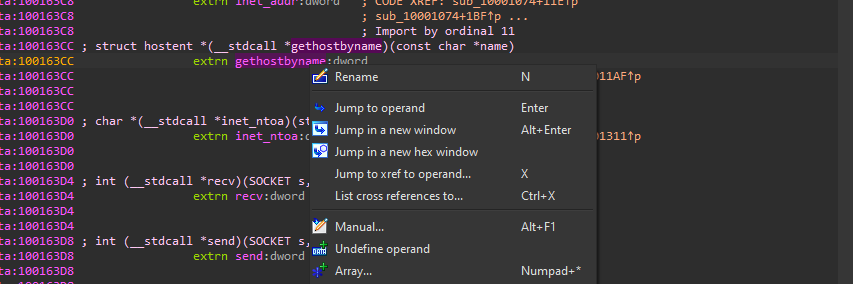
we found some functions call it but it is called nine times…
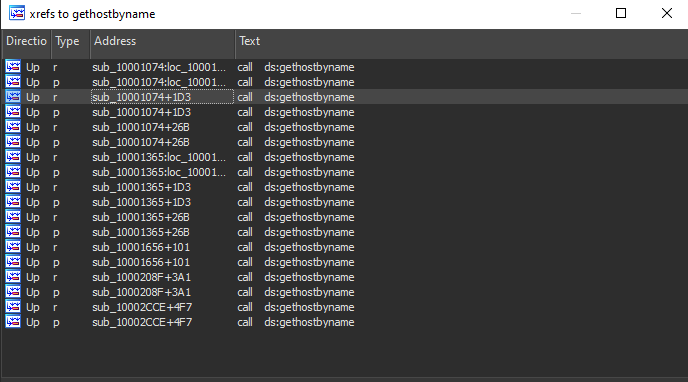
“Some versions of IDA Pro double-count cross-references: p is a reference because it is being called, and r is a reference because it is a “read” reference (since it is called dword ptr […] for an import, the CPU must read the import and then call into it).”
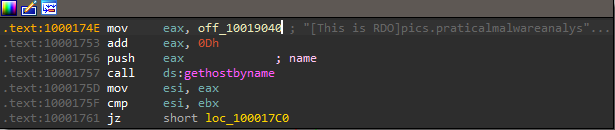
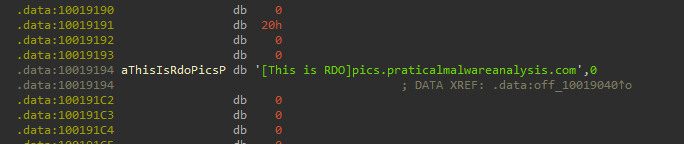
4. Focusing on the call to gethostbyname located at 0x10001757, can you figure out which DNS request will be made?
By using the jump to address function or clicking G we can jump to address 0x10001757 and then go to off_10019040 that contains the DNS request.
5. How many local variables have IDA Pro recognized for the subroutine at 0x10001656?
after jumping to address 0x10001656 we found 23 variable ida can be recognized.
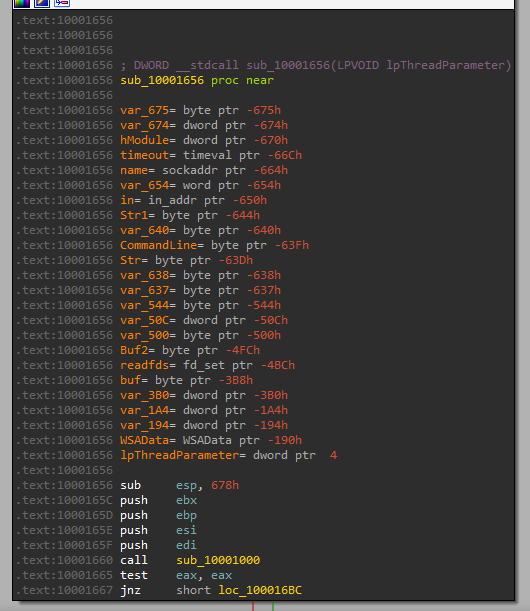
6. How many parameters has IDA Pro recognized for the subroutine at 0x10001656?
by looking at the last screenshot we found one parameter ida can recognize lpThreadParameter.
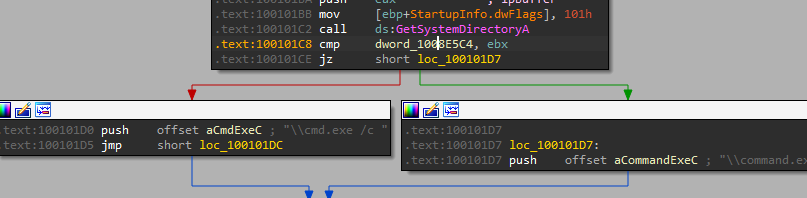
7. Use the Strings window to locate the string \cmd.exe /c in the disassembly. Where is it located?
by going to search > text or ALT+T we can search through the strings window for cmd.exe, and we can find where it is located .text:100101D0
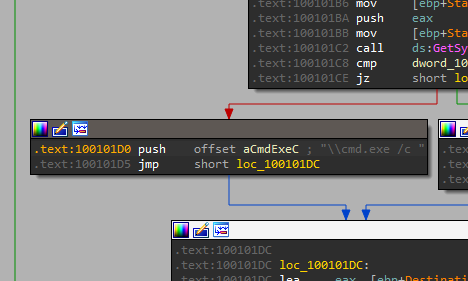
8. What is happening in the area of code that references \cmd.exe /c?
By following the xref to the subroutine which references \cmd.exe /c:
there are many interesting values being pushed to the stack:
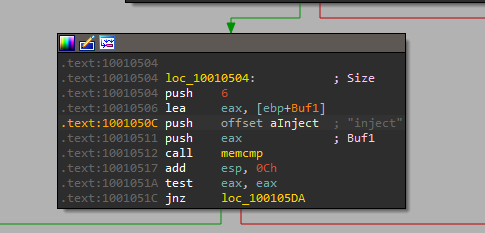
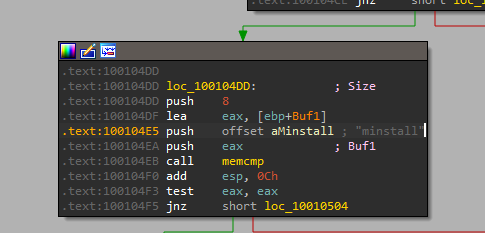
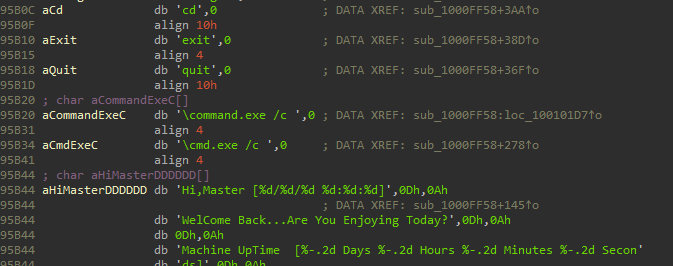
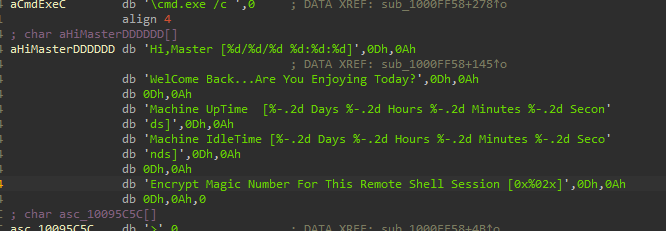
we can find that the char array aHiMasterDDDDDD mentions a ‘Remote Shell Session’
9. In the same area, at 0x100101C8, it looks like dword_1008E5C4 is a global variable that helps decide which path to take. How does the malware set dword_1008E5C4? (Hint: Use dword_1008E5C4’s cross-references.)
by using dword_1008E5C4’s cross-references I found three locations that write in one:
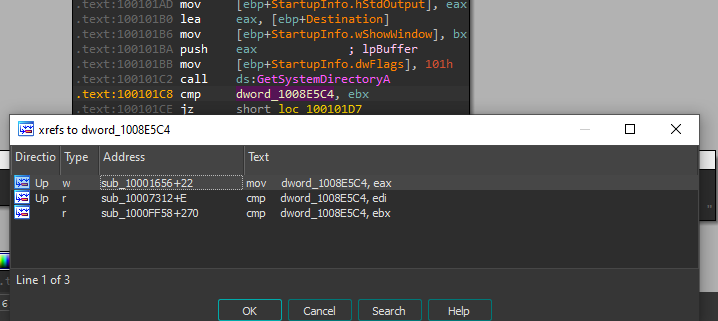
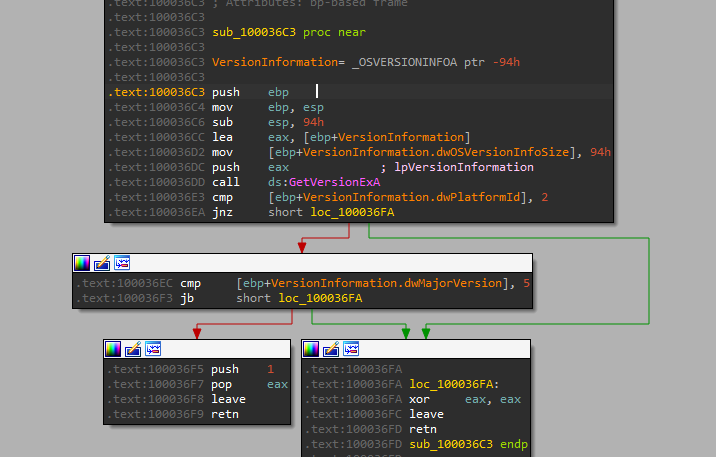
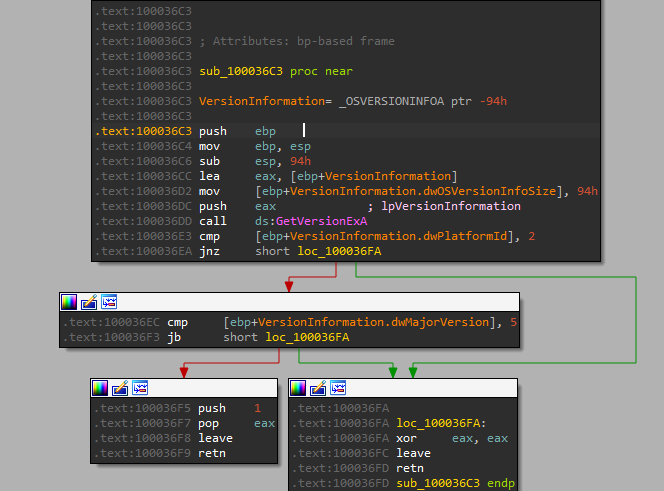
After that call function sub_100036C3 that checks the OS version by using GetVersionExA to decide which function to go into.
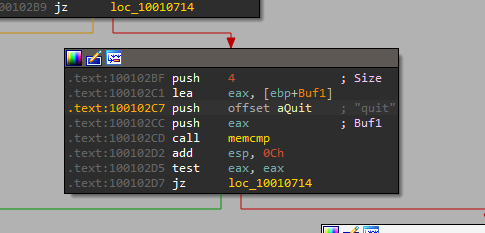
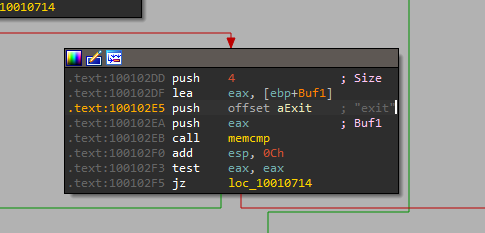
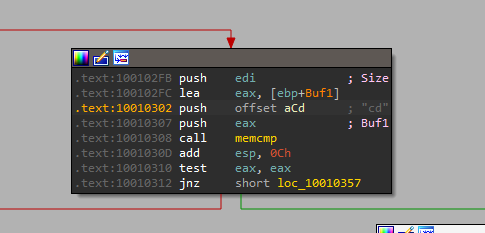
10. A few hundred lines into the subroutine at 0x1000FF58, a series of comparisons uses memcmp to compare strings. What happens if the string comparison to robotwork is successful (when memcmp returns 0)?
by looking into sub_1000FF58+4E0↑j in loc_10010444 location I find an entry comparing robotwork which uses the JNZ branch
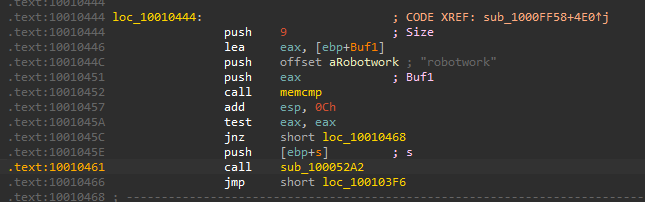
it returns zero so that call sub_100052A2 that tries to open registry key SOFTWARE\Microsoft\Windows\CurrentVersion
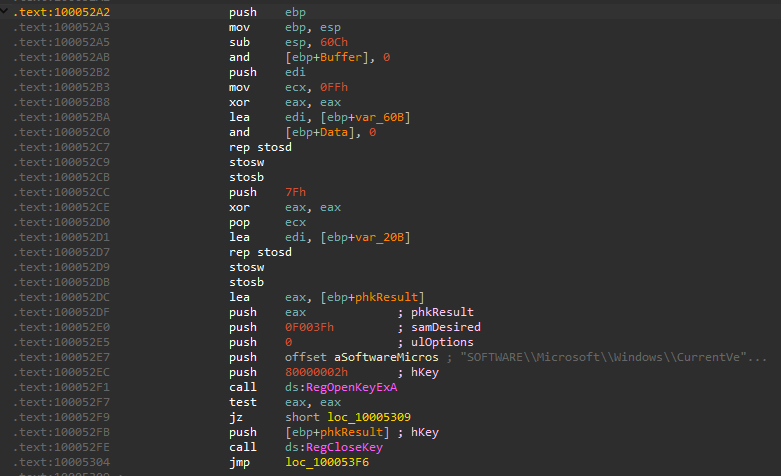
If successful, reads a registry key WorkTimes,” which is a string represented integer.
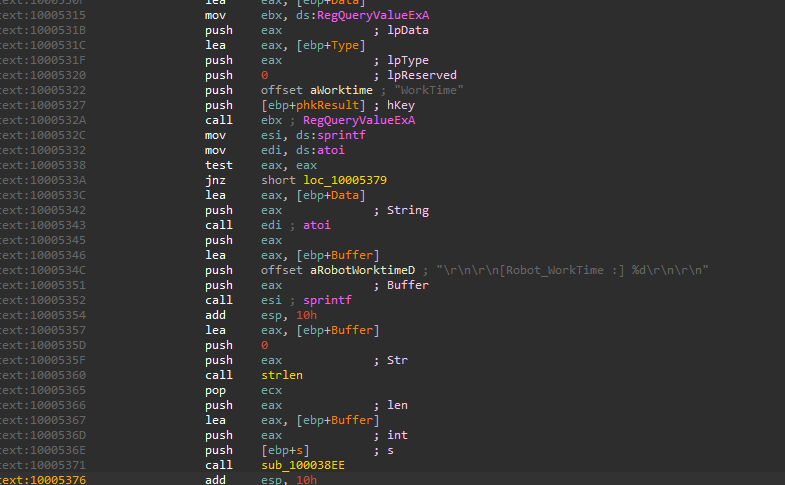
sub_100052A2 returns the constructed string, Execution continues until sub_100038EE is called, which sends the finished string through the socket
11. What does the export PSLIST do?
The first, it gets an OS version:
After that, it jumps to .text:10007046 because the return value is zero and after that call function sub_10006518
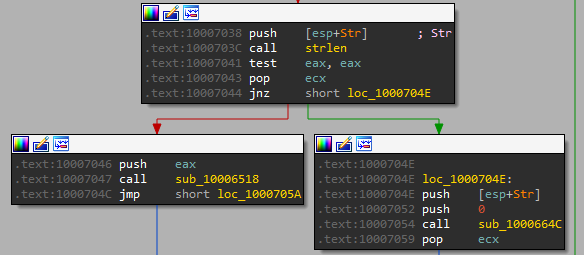
that function called CreateToolhelp32Snapshot Takes a snapshot of the specified processes, as well as the heaps, modules, and threads used by these processes then Sends the name of the process and PID over the socket.
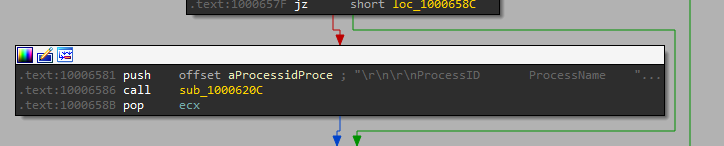
after that call OpenProcess and EnumProcessModules that Retrieve a handle for each module in the specified process.
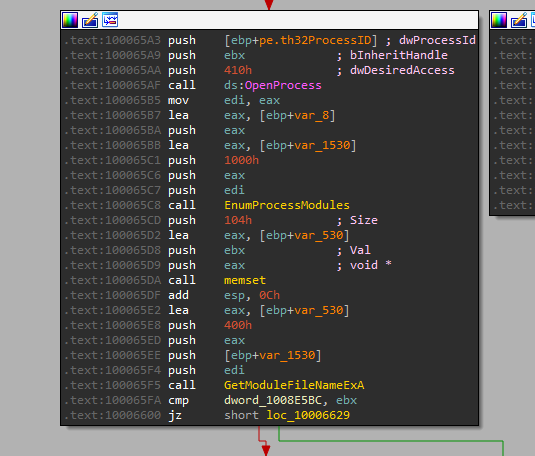
Sends PID, exe path, and thread count over the socket.
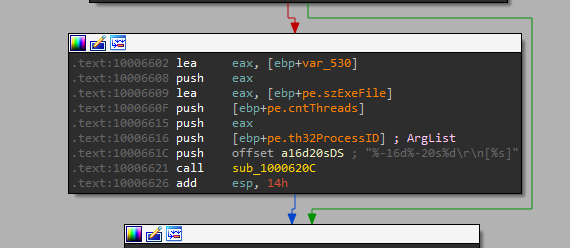
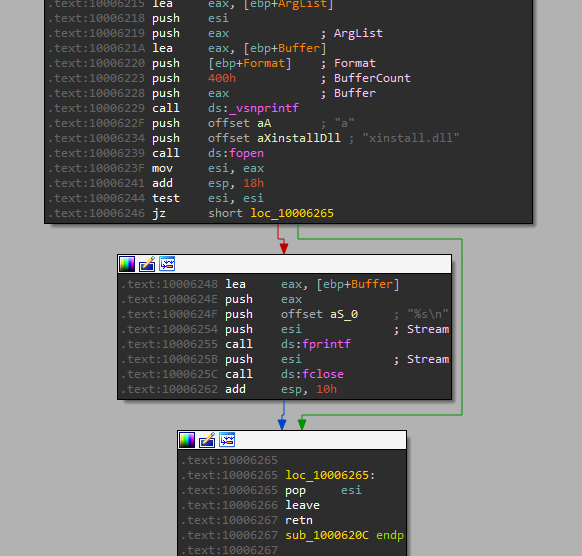
Writes process information to file xinstall.dll
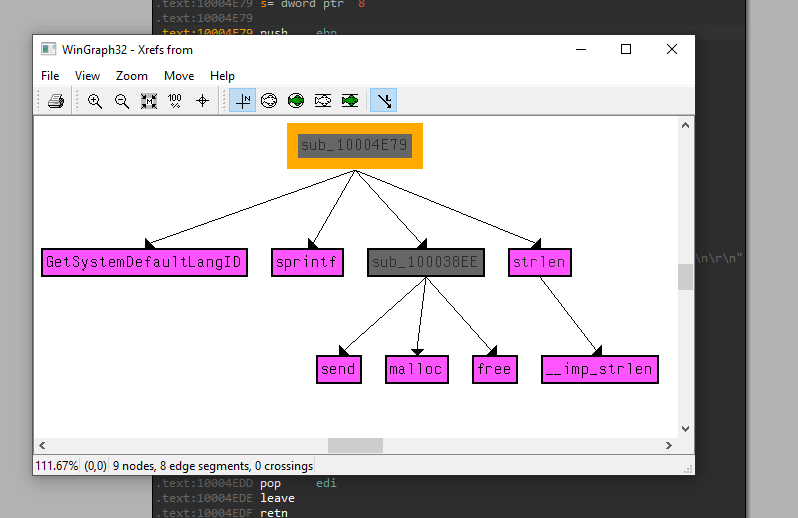
12. Use the graph mode to graph the cross-references from sub_10004E79. Which API functions could be called by entering this function? Based on the API functions alone, what could you rename this function?
By using G to go to the address of interest (in this case sub_10004E79), we can then click View > Graphs > XRefs From to see several API functions within this function.
13. How many Windows API functions does DllMain call directly? How many at a depth of 2?
By clicking View > Graphs > User xrefs chart, and then adjusting the settings to start and end at the function DLLMain with a depth of 2, we’re able to see 8 Windows API Functions.
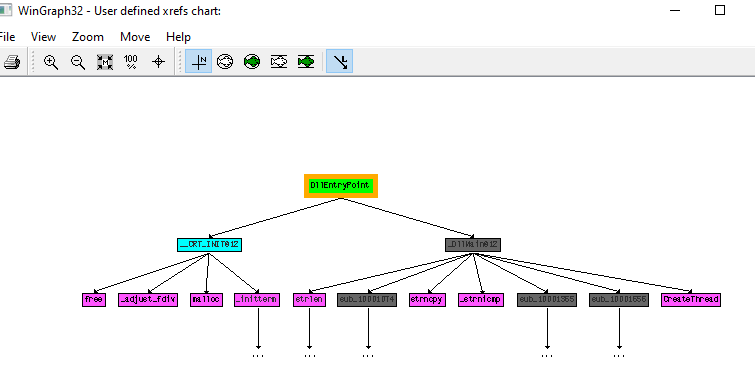
14. At 0x10001358, there is a call to Sleep (an API function that takes one parameter containing the number of milliseconds to sleep). Looking backward through the code, how long will the program sleep if this code executes?
we can see that EAX is multiplied by 1000 before being pushed to the stack and called. This matches the reference to milliseconds, in that there are 1000 milliseconds in a second, Based on the call to atoi this is then converted to a number before being multiplied by 1000, and as such the program will sleep for 30 seconds if this executes.
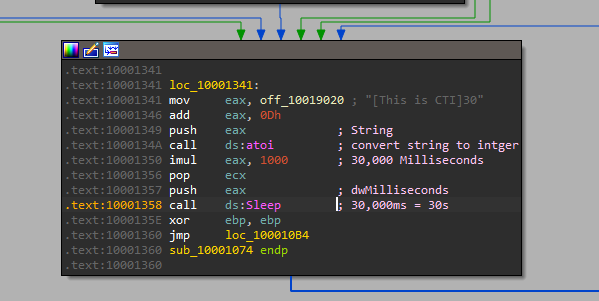
15. At 0x10001701 is a call to the socket. What are the three parameters?
socket function has three parameters af, type, protocol(2,1,6)
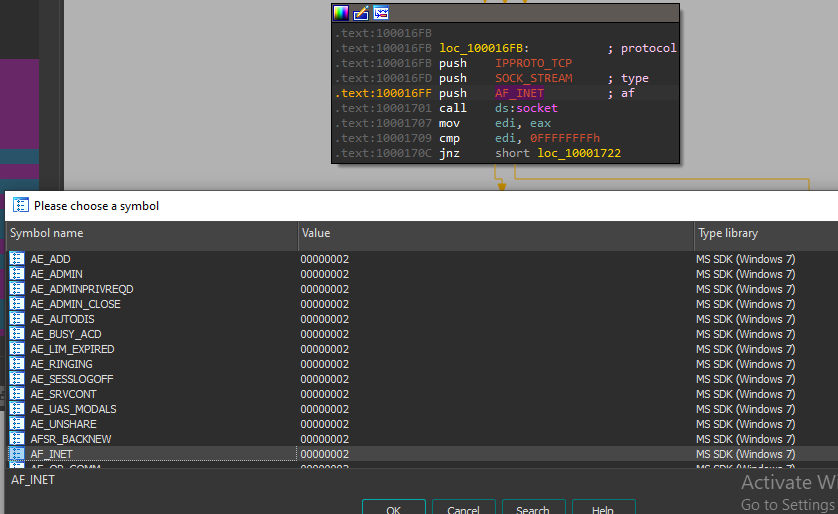
16. Using the MSDN page for socket and the named symbolic constants functionality in IDA Pro, can you make the parameters more meaningful? What are the parameters after you apply changes?
By looking into the MSDN Socket Function we can find what these numbers correlate to.
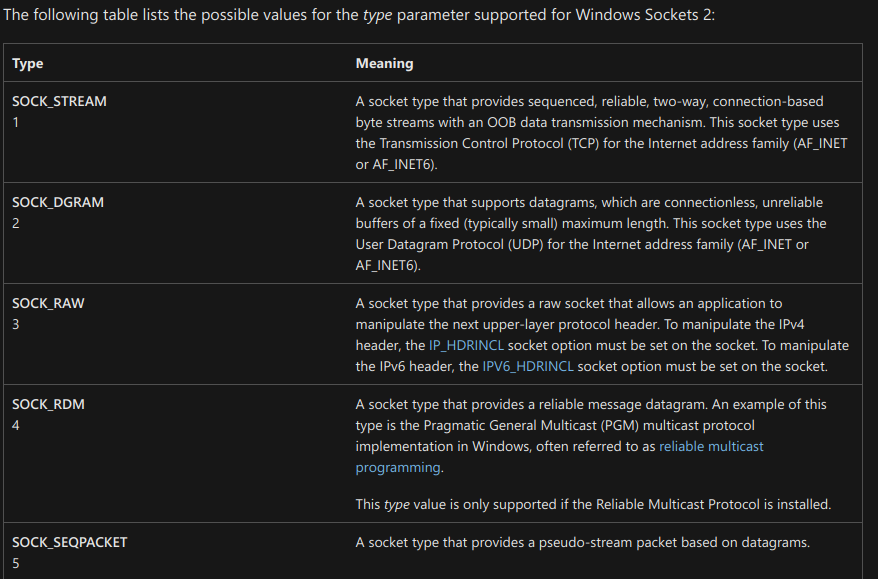
By right-clicking and selecting Symbolic Constant > Use Standard Symbolic Constant we’re able to quickly change these to accurately reflect their assigned values.
17. Search for the usage of the in-instruction (opcode 0xED). This instruction is used with a magic string VMXh to perform VMware detection. Is that in use in this malware? Using the cross-references to the function that executes the in-instruction, is there further evidence of VMware detection?
By searching for ‘ED’ as a sequence of bytes (ALT+B) we can find only one occurrence of the instruction ‘in’.
yes, the in-instruction is present at 100061DB with VX and VMXh strings.
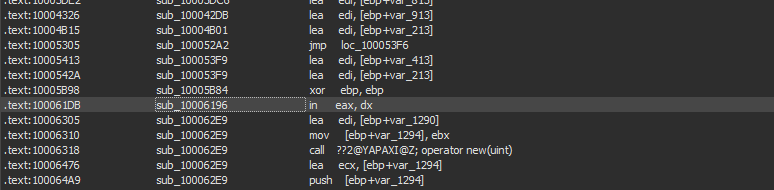
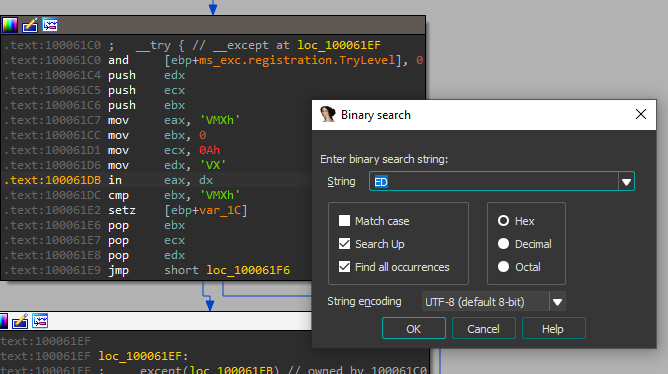
VPCEXT instruction is (anti–virtual machine trick) used to detect the presence of a Virtual PC, and if instruction runs on a virtual machine will return 0 on (EBX) register, (if ebx == 0) –> this means that Virtual PC detected,
If opcode 0F 3F b1 b2 is run outside Virtual PC, an illegal instruction exception is thrown otherwise return value in ebx register is checked. If the value in ebx register is 0 it means Virtual PC detected.
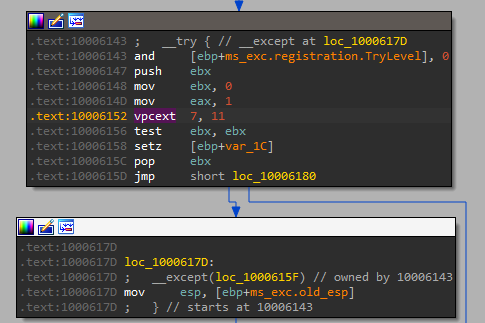
18. Jump your cursor to 0x1001D988. What do you find?
Probably an encoded string:
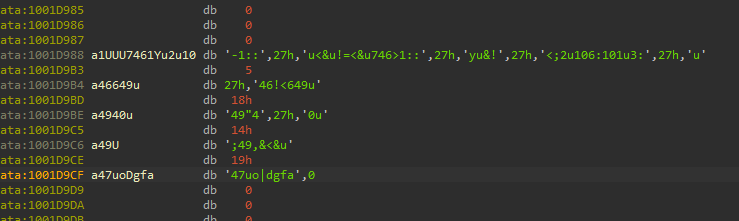
19. If you have the IDA Python plug-in installed (included with the commercial version of IDA Pro), run Lab05-01.py, an IDA Pro Python script provided with the malware for this book. (Make sure the cursor is at 0x1001D988.) What happens after you run the script?
Alt-F7, ran the script. Decoded the string:xdoor is this backdoor, string decoded for Practical Malware Analysis Lab :)1234
20. With the cursor in the same location, how do you turn this data into a single ASCII string?
A to decode as an ASCII string.
21. Open the script with a text editor. How does it work?
XOR encoding with a value of 0x55,
- Starting at the cursor location, loop for 0x50 bytes (80)
- Grab the byte.
- Perform bitwise XOR: b ^ 0x55 (85)
- Patch the resulting byte back.
sea = ScreenEA()
for i in range(0x00,0x50):
b = Byte(sea+i)
decoded_byte = b ^ 0x55
PatchByte(sea+i,decoded_byte)
Lab06_1
1. What is the major code construct found in the only subroutine called by main?
In the first, we can see the main function called the sub_401000.
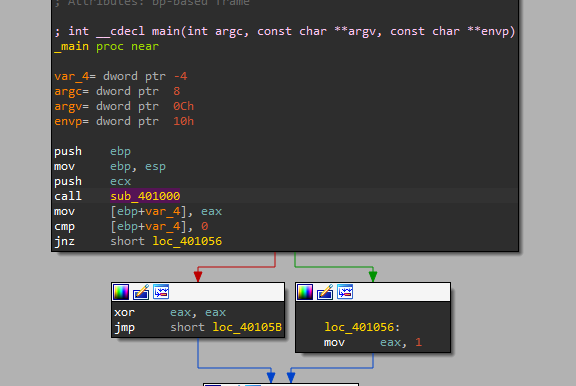
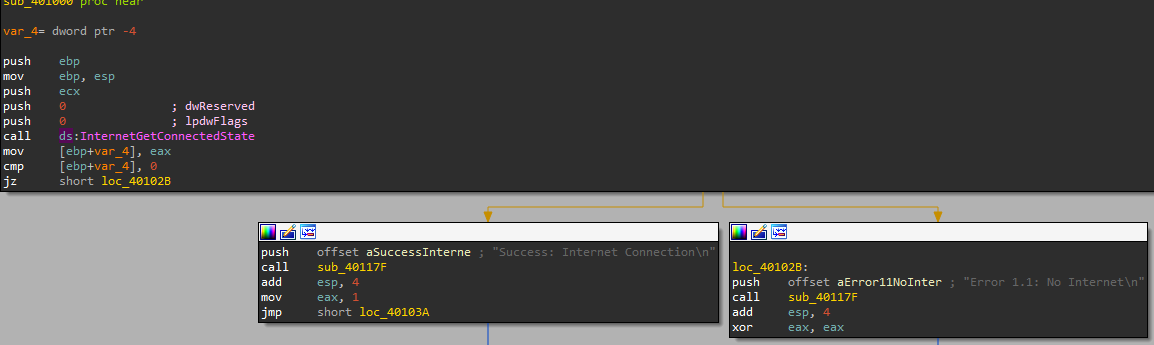
after that sub_401000 calls InternetGetConnectedState which has a condition that returns zero which means the function is not connected to the internet and if returns one that is mean the connection is successful. (if statement)
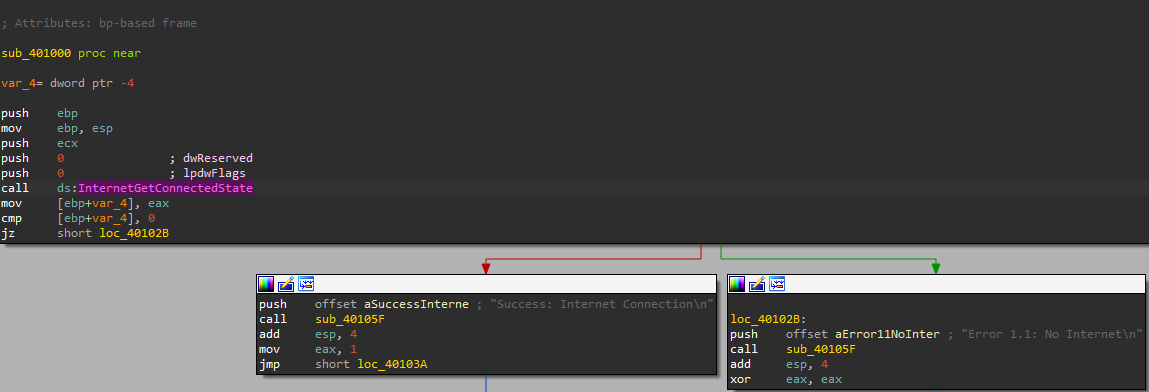
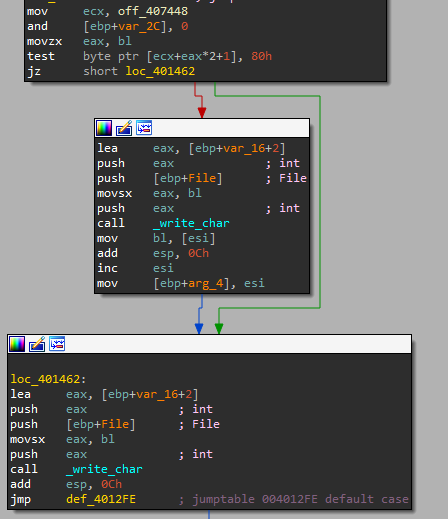
2. What is the subroutine located at 0x40105F?
I found the sub_401282 function that contains a switch cases code.
If we note there are a __stbuf and __ftbuf functions that are functions in C++ that are used to control buffering of input/output operations on streams__stbuf is used to enable buffering on a stream while __ftbuf is used to disable buffering on a stream1.
3. What is the purpose of this program?
- checks internet connection
- open file Hundle
- write characters to a file
# Lab06_2
## 1. What operation does the first subroutine called by the main perform?
checks internet connection
2. What is the subroutine located at 0x40117F?
I found the sub_401282 function that contains a switch cases code.
and if we note there are a __stbuf and __ftbuf functions that are functions in C++ that are used to control buffering of input/output operations on streams__stbuf is used to enable buffering on a stream while __ftbuf is used to disable buffering on a stream1.
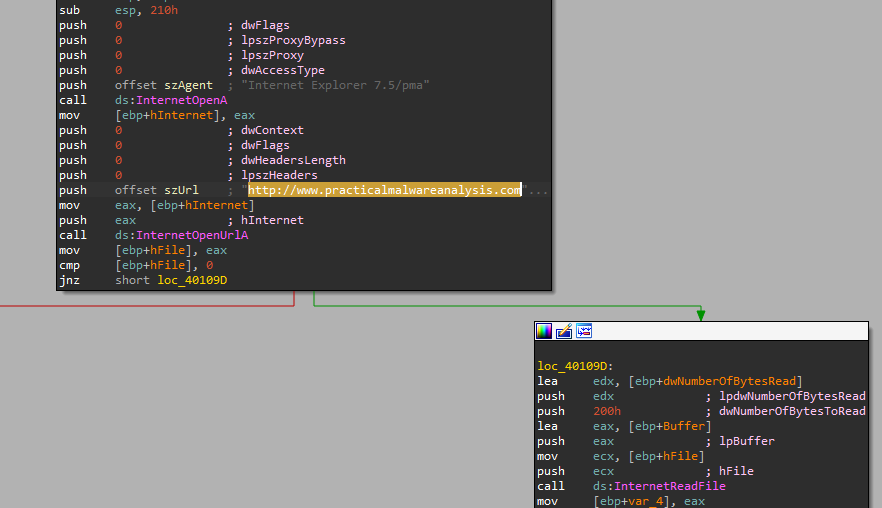
3. What does the second subroutine called by the main do?
checks user agent is Internet Explorer 7.5/pma and calls InternetOpenA,InternetOpenUrlA and InternetReadFile to open http://www.practicalmalwareanalysis.com url and read data from it.
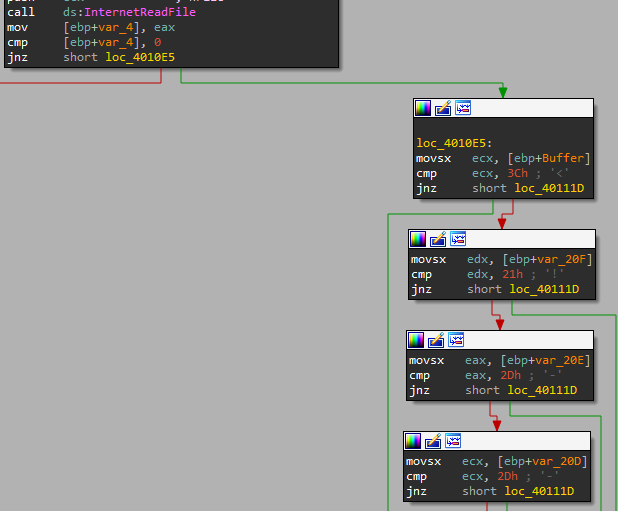
4. What type of code construct is used in this subroutine?
there are a lot of If\Then conditional statements,if we look under internetReadFile we can see multiple compare statements based on 4 characters from the buffer,<!-- that used in HTML code.
5. Are there any network-based indicators for this program?
send a request to http://www.practicalmalwareanalysis.com and before that check user-agentInternet Explorer 7.5/pma.
6. What is the purpose of this malware?
First the malware checks if any active internet connections, then send a Get request to http://www.practicalmalwareanalysis.com and reads 512 byte from it by using user-agent Internet Explorer 7.5/pma.
Lab06_3
1. Compare the calls in main to Lab 6-2’s main method. What is the new function called from the main?
there is a new function called sub_401130
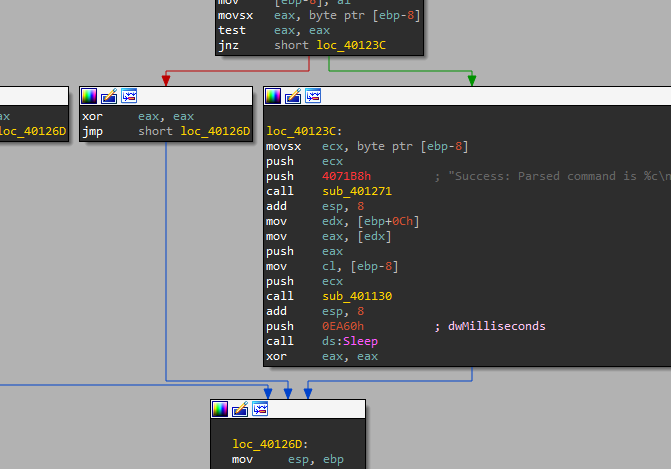
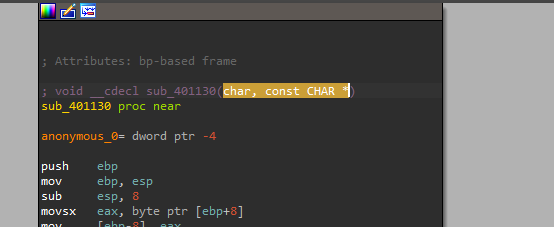
## 2. What parameters does this new function take?
By looking at the function, we can see it takes two parameters a character and a constant string
## 3. What major code construct does this function contain?
Switch with 5 cases that check the command, implemented as a jump table.
4. What can this function do?
there a 5 cases:
CreateDirectoryAthat creates a new directoryC:\TempCopyFileAthat copy a file from DATA “program name” thatC:\Temp\cc.exeto existing file- ` DeleteFileA
delete the file located atC:\Temp\cc.exe` if it exists RegOpenKeyExA, RegSetValueExATries to set reg valueMalware:C:\\Temp\\cc.exein theCurrentVersion\Runregistry key.SleepSleep for 100 seconds.- Default: Print error message.
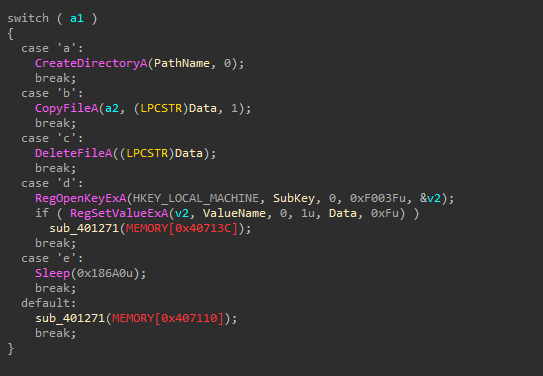
5. Are there any host-based indicators for this malware?
- create a new directory
C:\Temp - set reg value
Malware:C:\\Temp\\cc.exein theCurrentVersion\Runregistry key.
6. What is the purpose of this malware?
First check the internet connection then check user-agent internet explorer 7.5/pma and open the URL http://www.practicalmalwareanalysis.com and read the first 200 bytes into a buffer if that is <!-- print message ‘success’ If not exist print ‘Error 2.3: Fail to get command\n’
After that in the next function:
CreateDirectoryAthat creates a new directoryC:\TempCopyFileAthat copy a file from DATA “program name” thatC:\Temp\cc.exeto existing fileDeleteFileAdelete the file located atC:\Temp\cc.exeif it existsRegOpenKeyExA, RegSetValueExATries to set reg valueMalware:C:\\Temp\\cc.exein theCurrentVersion\Runregistry key.SleepSleep for 100 seconds.- Default: Print error message.
that allow malware to
- Install the malware to run at boot.
- Copy a new version of the malware.
- Delete the malware.
Lab06_4
1. What is the difference between the calls made from the main method in Labs 6-3 and 6-4?
- In 06-04 the User-Agent has changed to
Internet Explorer 7.50/pma%d - Add some function from the main in a loop
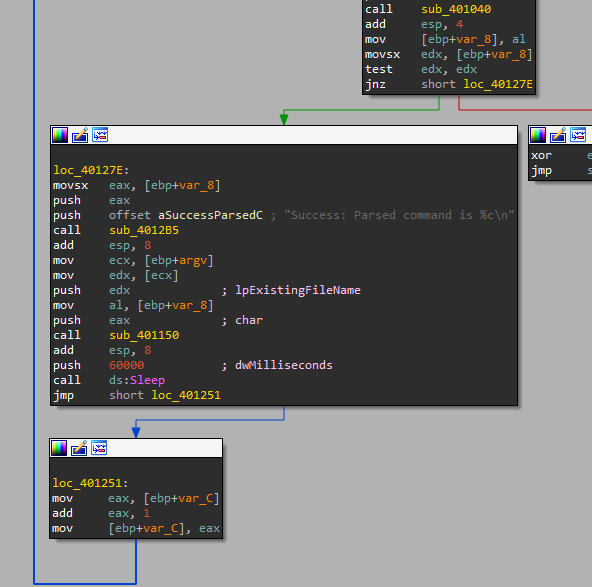
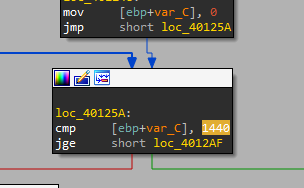
2. What new code construct has been added to the main?
A for loop with 1440 iterations.
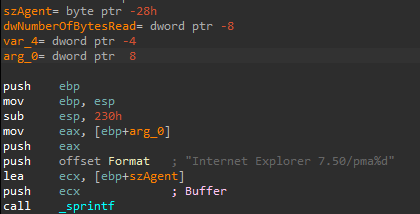
3. What is the difference between this lab’s parse HTML function and those of the previous labs?
the User-Agent has changed to Internet Explorer 7.50/pma%d and added an argument %d that is the duration of the program run.
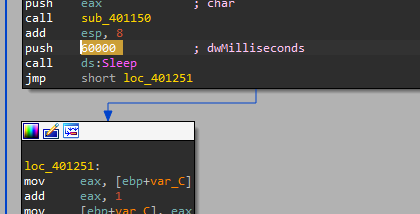
4. How long will this program run? (Assume that it is connected to the Internet.)
(1440 iterations) * (60s sleep) = 1440 minutes = 24 hours = 1 day.
5. Are there any new network-based indicators for this malware?
- User-Agent
Internet Explorer 7.50/pma%d - URL
http://www.practicalmalwareanalysis.com
6. What is the purpose of this malware?
First, check the internet connection then check user-agent internet explorer 7.50/pma%d and open the URL http://www.practicalmalwareanalysis.com and read the first 200 bytes into a buffer if that is <!-- print message ‘success’ if not exist print ‘Error 2.3: Fail to get command\n’
After that in the next function:
CreateDirectoryAthat creates a new directoryC:\TempCopyFileAthat copy a file from DATA “program name” thatC:\Temp\cc.exeto existing file- ` DeleteFileA
delete the file located atC:\Temp\cc.exe ` if it exists RegOpenKeyExA, RegSetValueExATries to set reg valueMalware:C:\\Temp\\cc.exein theCurrentVersion\Runregistry key.SleepSleep for 100 seconds.- Default: Print error message.
Malware identifies itself to the server via the UserAgent string and will run for 24 hours.