Mac-os malware-analysis guide
OverView
-
macOS is built on the XNU kernel, which is a hybrid kernel combining elements of the Mach kernel and components from FreeBSD, rather than the Linux kernel. This means that while there are similarities in Unix-like behavior and some shared concepts with Linux, there are also significant differences, particularly in kernel APIs and system architecture.
-
To analyze macOS malware, start by setting up a virtual machine for a safe environment and installing essential tools like strings, otool, lldb, and hex editors. Begin static analysis by examining the file type and properties, extracting readable strings, and analyzing the binary’s segments and symbols. Disassemble the binary to understand its logic.
-
For dynamic analysis, run the malware in a controlled environment, monitoring its behavior with tools like fs_usage and Activity Monitor, and use lldb for debugging. Identify persistence mechanisms by checking for malicious plist files in
~/Library/LaunchAgents/and/Library/LaunchDaemons/, cron jobs, login items, and any installed kernel or browser extensions. -
Analyze network activity using tools like Wireshark or tcpdump to detect communication with remote servers, which may indicate command and control activity. Observe behavioral changes such as file system modifications and system call with strace or dtruss. Finally, document your findings, including persistence methods and network activities, and list Indicators of Compromise (IOCs) like file hashes, IP addresses, and domain names for effective detection and prevention.
MAC Software Security Protections
-
macOS incorporates System Integrity Protection (SIP) to prevent the root user from modifying system files and directories. Gatekeeper verifies and allows only trusted software to run. XProtect is the built-in anti-malware system that blocks known harmful software. Notarization ensures apps are checked by Apple for malware before distribution.
-
The App Sandbox limits app capabilities by isolating them from the system and other apps. FileVault provides full-disk encryption to protect data. Secure Boot ensures only a legitimate macOS operating system loads during startup. Privacy protections require user consent for app access to sensitive data.
-
Runtime protections like ASLR and DEP prevent malicious code exploitation. System Extensions and DriverKit replace kernel extensions with safer, user-space system extensions. Keychain and iCloud Keychain provide secure password storage and cross-device password management.
-
These security features collectively ensure comprehensive protection for macOS, maintaining system performance and usability while defending against various threats.
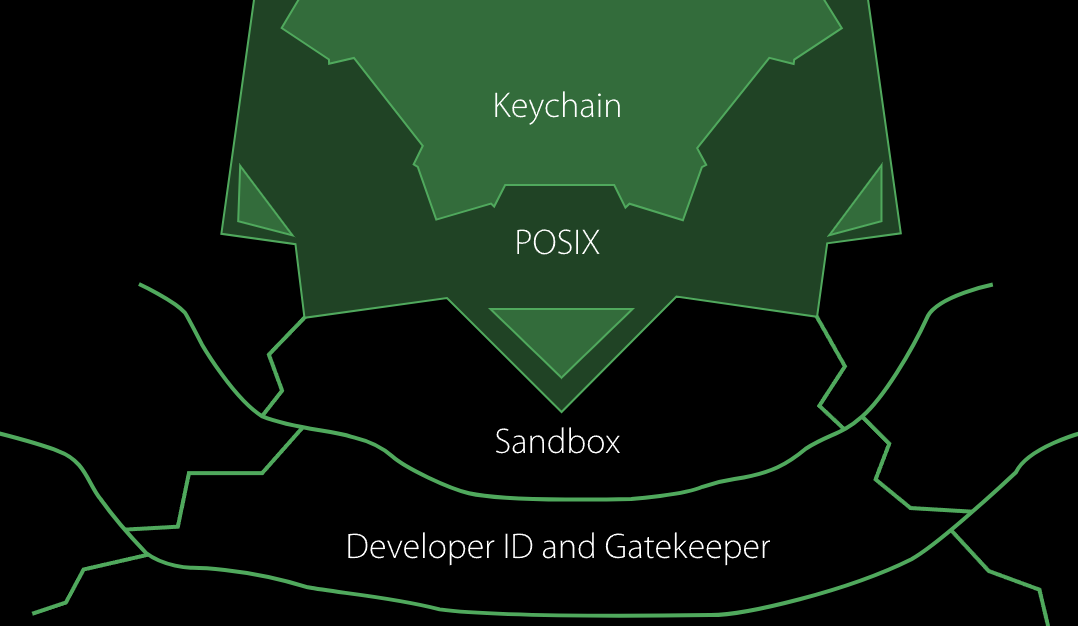
Figure(1): MAC Software Security Protections
Persistence
- Persistence is a primary goal for most malware after execution, ensuring it remains active across reboots and user sessions. In macOS, malware can achieve persistence through various techniques. Although macOS is built on the XNU kernel, not the Linux kernel, many persistence techniques are conceptually similar to those in Linux. Here are common persistence locations and methods for macOS:
Launch Agents and Daemons:
- Launch Agents: Located in
~/Library/LaunchAgents/, these are used to run processes when a user logs in. - Launch Daemons: Located in
/Library/LaunchDaemons/, these run system-wide processes at startup.
Login Items:
- Malware can add itself to the list of applications that start automatically when a user logs in. This can be managed through System Preferences or modified via plist files.
Cron Jobs:
- Similar to Linux, macOS supports cron jobs. Malware can schedule tasks to run at specified intervals by creating entries in the crontab.
Kernel Extensions:
- Though less common and more complex, some malware installs kernel extensions (kexts) to achieve deep system-level persistence.
Browser Extensions:
- Malware may install malicious browser extensions that execute whenever the browser is opened.
Launch Scripts:
- Malware can modify or add scripts in directories like /etc/rc.common or /Library/StartupItems/ to execute at system startup.
Application Bundles:
- Malware can embed itself in application bundles or disguise itself as legitimate applications to ensure persistence.
User and System-Level Daemons:
- Daemons and services configured to start at boot or login can be targeted to ensure malware execution.
Persistent Files:
- Malware may place files in user directories like ~/Library/Application Support/ or other locations to ensure they are reloaded.
Plist Files:
-
Malicious plist files can be placed in various directories to control startup behavior or run custom scripts.
-
for a comprehensive list of persistence techniques used in Mac OS, you can visit MITRE ATT&CK
General malware analysis
-
I won’t go into detailed analysis of the malware itself, but I will demonstrate how the malware analysis process works for Mac malware. This indicates that mac-dummy is a 64-bit executable file formatted as Mach-O and is intended for the x86_64 architecture.
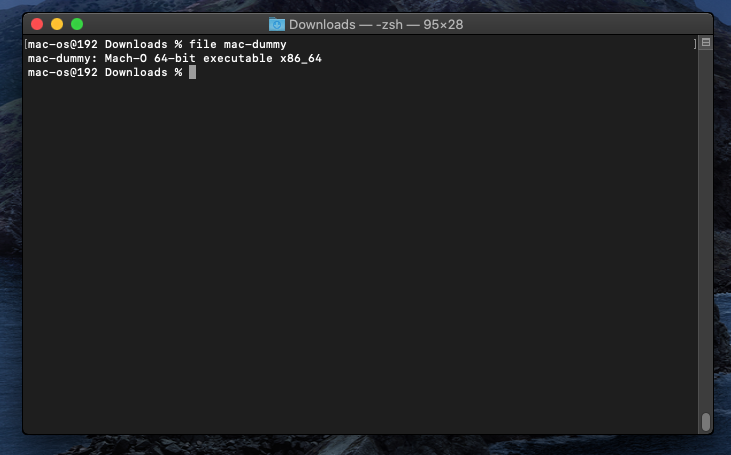
Figure(3): file info -
The command otool -L mac-dummy shows the dynamic libraries linked by the mac-dummy executable, this output indicates that mac-dummy links against the CoreFoundation framework, libSystem.B, and libc++. Each library has its compatibility and current version listed.
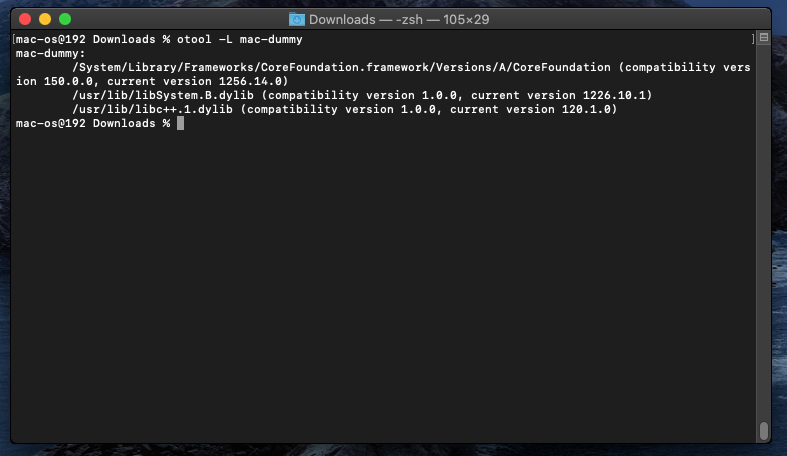
Figure(4): otool -
The strings command extracts readable text from a binary file. To find potentially useful strings in the mac-dummy executable, you would use: strings mac-dummy strings can help in understanding the purpose of the executable, locating configuration or resource paths, and identifying potential areas of interest for further analysis.
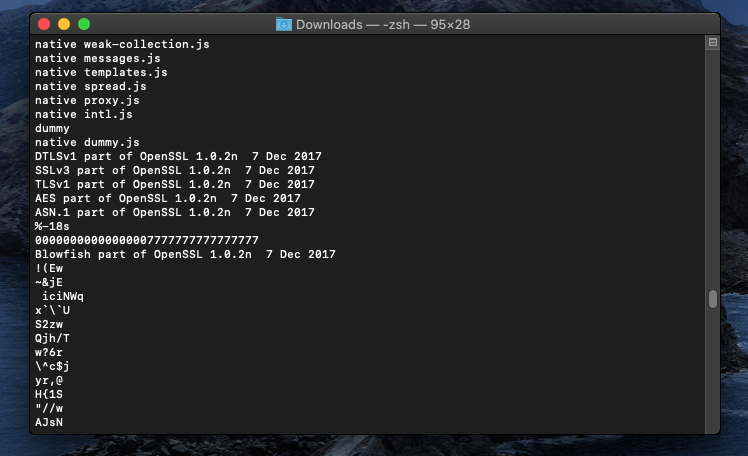
Figure(5): strings -
another tool which will be worth running is nm tool which resolves the symbols in the file which may give you more understanding of the file functionality.
-
Another useful tool to run is nm, which resolves and lists the symbols in the file. This can provide valuable insight into the functionality of the executable by revealing function names, variable names, and other symbols. To use nm on the mac-dummy file, you would run:
nm -m mac-dummy -
This command will output a list of symbols along with their addresses and types, helping you understand the structure and functionality of the file.
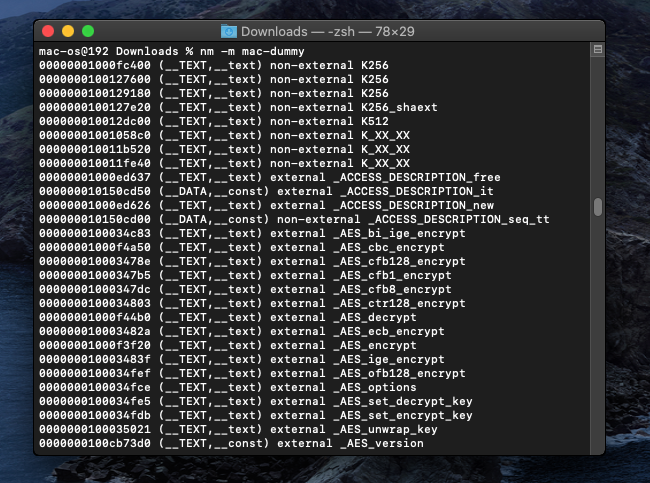
Figure(6): nm_tool -
for debugging and code analysis, you can use IDA and Remote debug feature