APT Attack Cases Using Dora RAT Against Korean Companies
Overview
The AhnLab Security Intelligence Center (ASEC) found that the Andariel APT group recently attacked Korean companies, including those in education and manufacturing. The attackers used malware like Nestdoor, a backdoor, and Dora RAT, a simpler backdoor made with Go, to take control of infected systems, steal data, and stay hidden.
They took advantage of weak Apache Tomcat servers and a flaw in VMware Horizon called Log4Shell to spread the malware. The attacks also involved keyloggers, proxy tools, and clipboard loggers, which are often used to gather sensitive information. Andariel, which is connected to the Lazarus group, has changed from targeting national security to focusing on financial gains, usually using spear-phishing and exploiting unpatched software vulnerabilities.
we will focus on understanding their functionality and identifying suspicious behaviors. This will involve examining how each sample operates, what actions they perform once executed, and any unusual or malicious activities, such as network connections, file modifications, or process manipulation.

c419f17b54d….exe
First Look
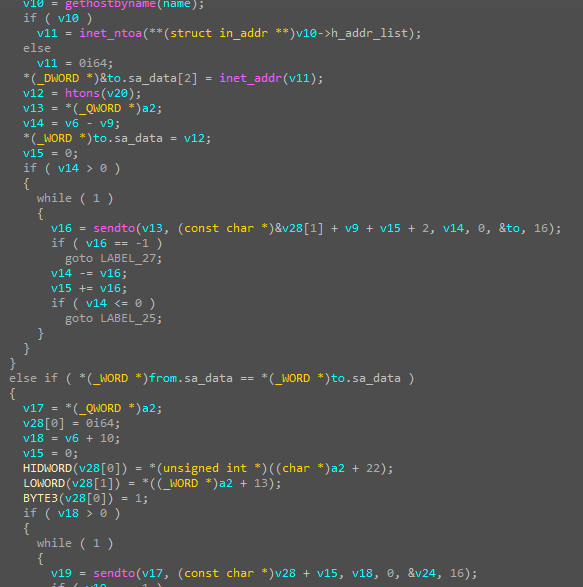
begin with the first one, malware is a PE32+ executable (GUI) x86-64, for MS Windows. This 64-bit executable targets the Windows operating system and likely operates through a graphical user interface (GUI).
By analyzing the imports of malware using PEstdio.exe, several notable functions suggest what the malware might do:
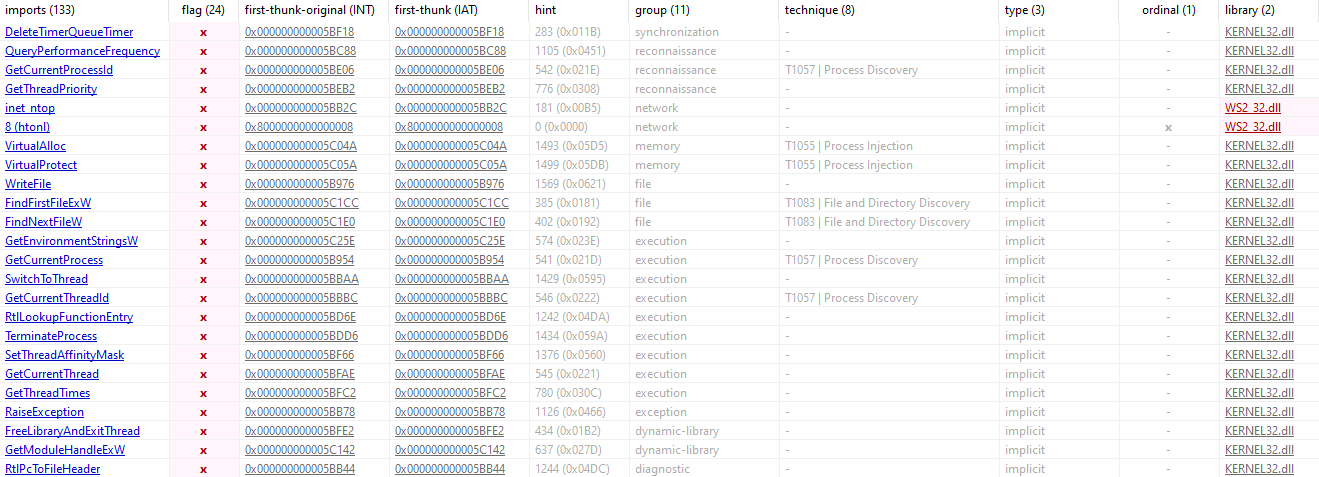
DeleteTimerQueueTimer and QueryPerformanceFrequency suggest the malware could use timers for accurate timing or to avoid detection in sandbox environments by using performance counters.
GetCurrentProcessId, GetCurrentProcess, and GetCurrentThreadId indicate the malware is tracking or changing its own process and thread details, possibly for injecting into other processes or managing multiple threads.
inet_ntop and htonl suggest network activities, possibly for converting IP addresses or connecting to a remote command-and-control (C2) server.
VirtualAlloc and VirtualProtect shows the malware might be allocating and changing memory, possibly for injecting code or unpacking itself.
WriteFile suggests the malware could write data to the disk, maybe to log stolen information or save its payload.
FindFirstFileExW and FindNextFileW are used for searching through files on the victim’s computer, likely to find specific files.
GetEnvironmentStringsW suggests the malware is looking at environment variables, possibly to learn about the system or check its running conditions.
SwitchToThread and SetThreadAffinityMask involve managing threads, which could help the malware run more efficiently on certain CPU cores.
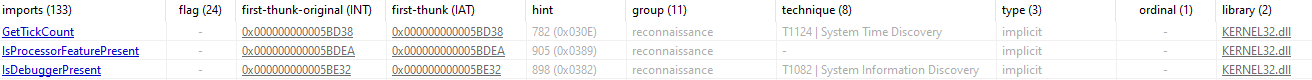
IsDebuggerPresent and GetTickCount are tools for anti-debugging, as the malware tries to avoid being analyzed by a debugger.
LoadLibraryExW, LoadLibraryW, and GetProcAddress are used for loading libraries dynamically, possibly to add extra features while running or to avoid being detected by static analysis.

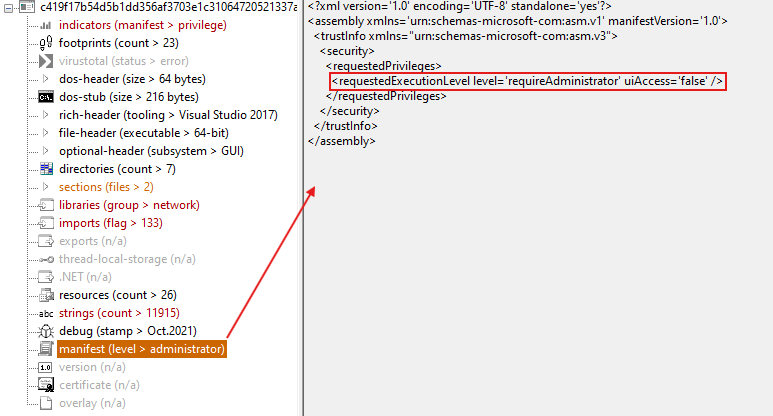
The XML code given is a setup guide for a Windows program. This guide says that the program needs special permission from an administrator to start, shown by the requestedExecutionLevel part with level=’requireAdministrator’. The uiAccess=’false’ part means the program doesn’t need extra access to the user’s screen. This guide is made to work well with Microsoft’s system, so the program gets theright permissions when it runs.
BEHAVIOR ANALYSIS
After executing the malware we got that window, seems like OpenVPN and wants me to enter a username and password.
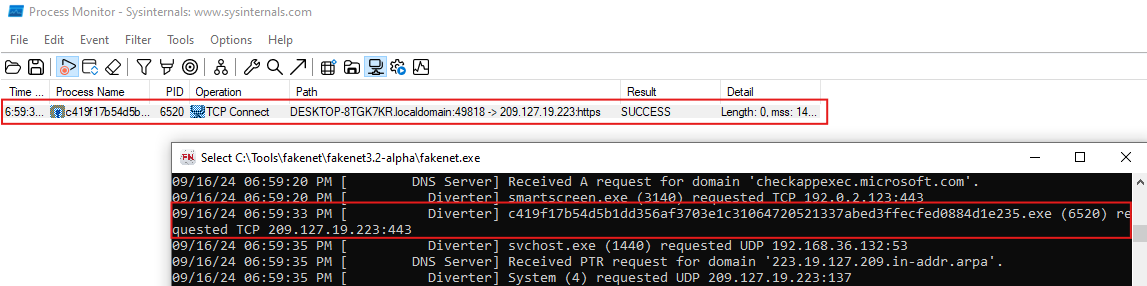
The network activity observed with procmon.exe shows a connection from a local machine, identified as DESKTOP-8TGK7KR.localdomain, using source port 49818, to a remote server at IP address 209.127.19.223 over HTTPS. This indicates that your system is attempting to establish a secure, encrypted connection with this remote server.
The IP address 209.127.19.223 is located in Montreal, Quebec, Canada. It is associated with B2 Net Solutions Inc, a company also known as ServerMania. This ISP and organization provide hosting and server solutions. The geographical coordinates for this IP are approximately 45.46° latitude and -73.55° longitude, placing it in the Montreal area.

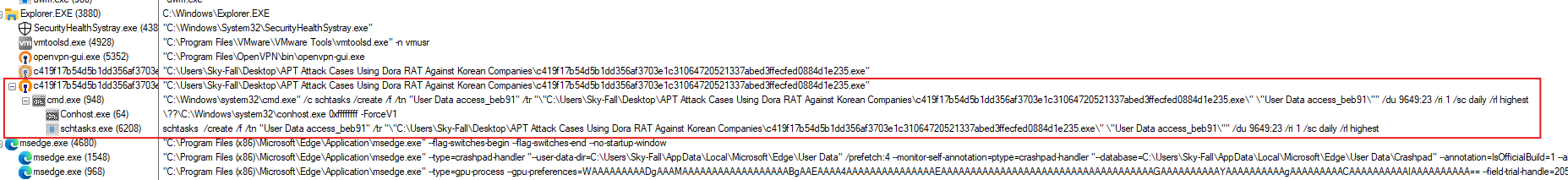
Using Procmon, it was discovered that the malware sets up a scheduled task through a series of processes. The process cmd.exe (PID 948) runs the schtasks command, which creates a task called “User Data access_beb91”. This task is designed to repeatedly run a suspicious file located at: C:\Users\Sky-Fall\Desktop\APT Attack Cases Using Dora RAT Against Korean Companies\c419f17b54d5b1dd356af3703e1c31064720521337abed3ffecfed0884d1e235.exe
The task is scheduled to run every day, at a 1-minute interval, and it will do so with the highest level of permissions. The timestamp indicates that this process began on 9/17/2024 at 2:22:10 AM, just before schtasks.exe (PID 6208) was used to complete the task setup.
ADVANCED ANALYSIS
Using x64dbg.exe we can dive into the functionality of the malware.
The code demonstrates how to resolve several API functions using the GetProcAddress and GetModuleHandleW functions.
The code starts by getting the address of kernel32.dll using the GetModuleHandleW function. It then repeatedly uses GetProcAddress to get the addresses of various Windows API functions.
The functions being resolved include FlsAlloc, FlsFree, InitializeCriticalSectionEx, CreateEventExW, CreateSemaphoreW, SetThreadpoolTimer, and FlsGetValue, FlsSetValue, GetTickCount64 and others.
Each function’s address is stored in a specific memory location, as shown by the mov instructions that save the rax register (which holds the result from GetProcAddress) into memory.
The use of functions like FlsAlloc and InitializeCriticalSectionEx indicates that the code is handling fiber-local storage (FLS) and thread synchronization, which is common in multi-threaded programs.
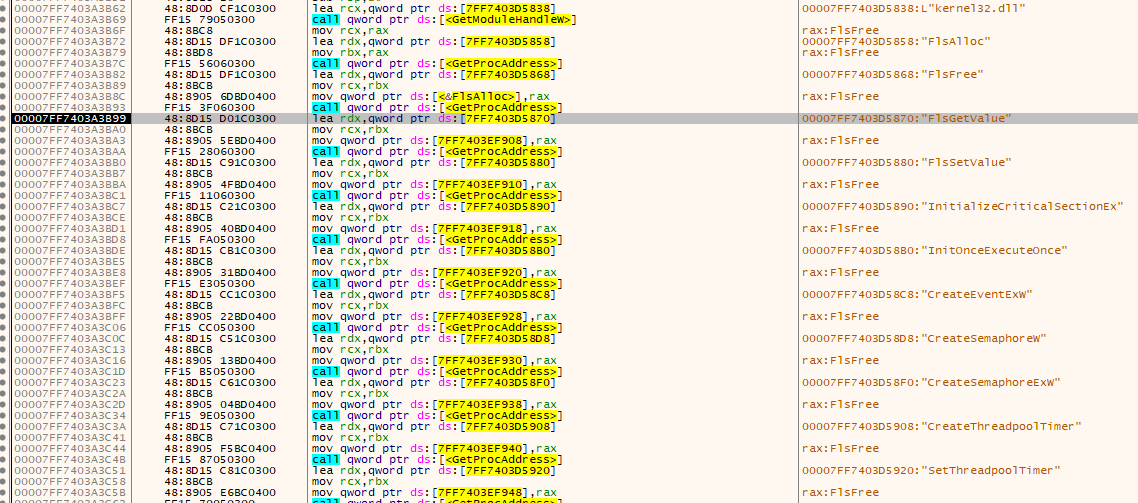
And go to the loop that resolves other functions that will be used in the malware like CreateFile, ReadFile, GetFileSizeEX
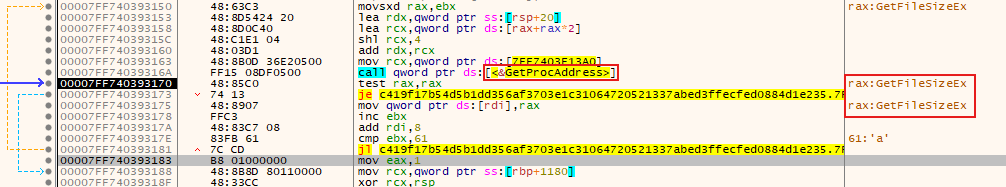
Then the malware uses OpenProcessToken and other imports that resolved to reach all files and processes like:
L"C:\\Users\\Sky-Fall\\AppData\\Local\\Microsoft\\Windows\\INetCache" refers to the path where cached files are stored by Internet Explorer or Edge on Windows systems. possibly indicating that the malware interacts with browser cache files, either to extract information or to store something.
the malware is reading or writing to this cache directory, as it may be attempting to extract sensitive data from cached files
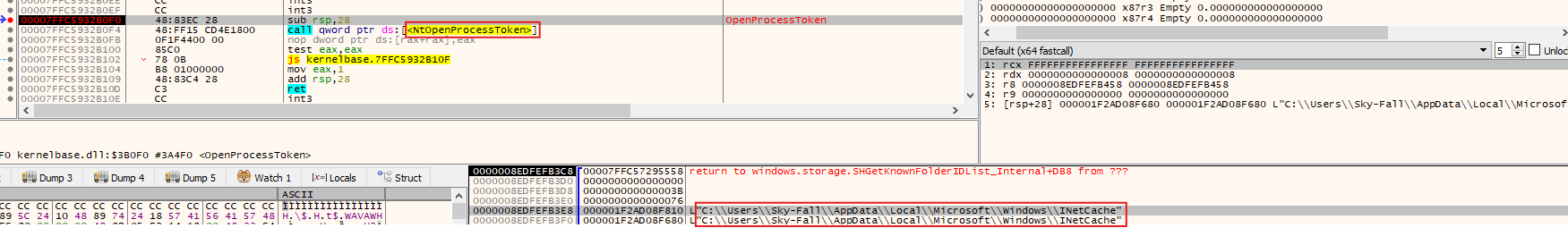
The malware executes the tasks we talked about previously:
"\\Sky-Fall\\AppData\\Roaming\\Microsoft\\Windows\\Start Menu\\Programs\\Startup" This path points to the Startup folder, where programs listed will automatically launch when Windows starts. Malware often copies itself or creates a shortcut in this directory to ensure persistence, meaning it will execute every time the system reboots.
"C:\\Users\\Sky-Fall\\AppData\\Local\\Microsoft\\Windows\\Caches" This is a common location where cached data is stored for Windows applications. Malware might leverage this directory to either cache malicious data for later use or potentially manipulate cached files to influence legitimate applications.
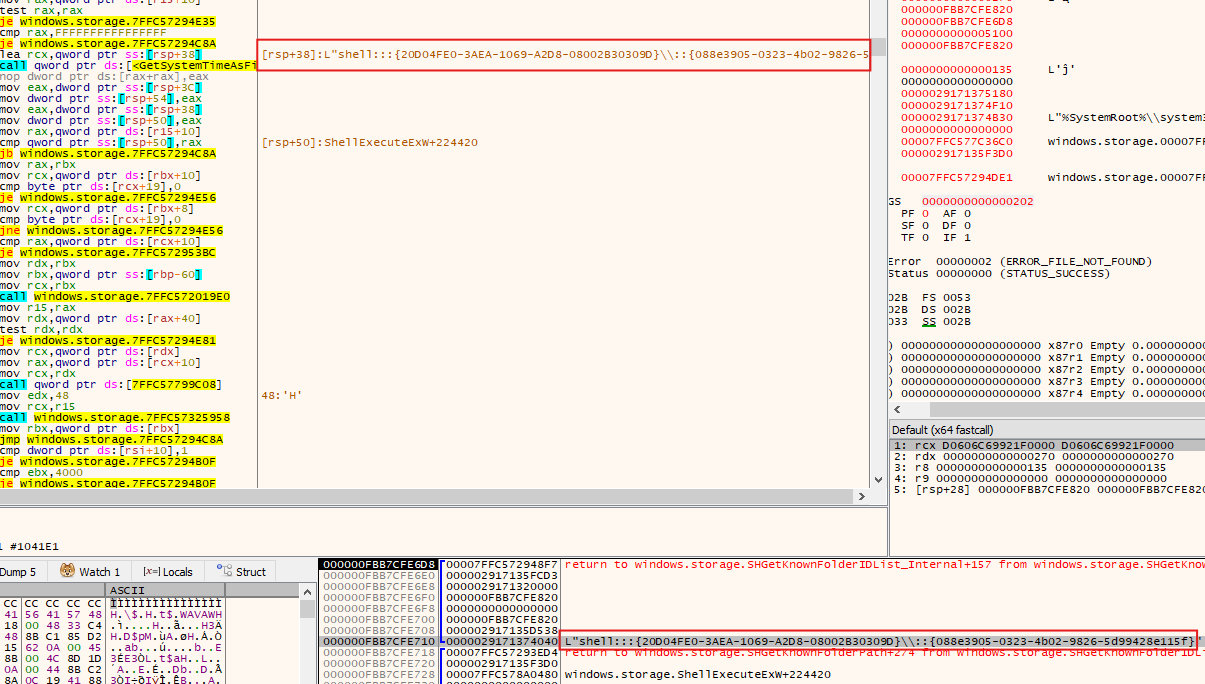
L"shell:::{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\::{088e3905-0323-4b02-9826-5d99428e115f}" represents a shell namespace identifier (CLSID) used by Windows to reference specific system objects or locations.
• 20D04FE0-3AEA-1069-A2D8-08002B30309D corresponds to the “This PC” (formerly known as “My Computer”).
• 088e3905-0323-4b02-9826-5d99428e115f is associated with storage-related items, often referencing removable storage devices or network locations.
These paths could be used for navigating to specific system locations without directly referencing them by name, which may obscure the malware’s intentions or actions. This could be part of an attempt to access or monitor external or removable storage devices for data exfiltration or infection.
After the malware locks files on the victim’s computer, including different files and cache data, it tries to connect to a Command and Control (C2) server at the IP address 209.127.19.223. This C2 server probably receives the stolen data. By sending the locked files, the malware makes sure that important information goes to a server controlled by the attacker, where it can be looked at or used in other ways.
This action is common for data-stealing malware and usually happens at the end of the infection process before any cleanup or staying-on measures are taken.

3ec2292dc5be…exe
First Look
file is a PE32+ executable (GUI) for x86-64 Windows, it indicates that the malware is designed for 64-bit Windows systems with a graphical user interface.
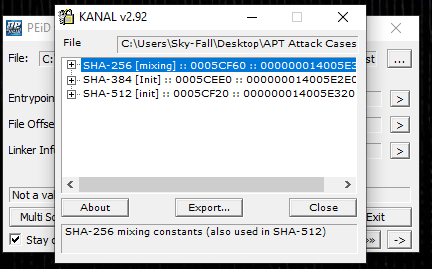
 The malware uses SHA-256, SHA-384, and SHA-512 cryptographic hashing algorithms, The SHA-256 method is used in the mixing process, whereas SHA-384 and SHA-512 are responsible for setting up the initial steps. These methods indicate that the malware could be using cryptographic hashing for encryption, ensuring data accuracy, or creating keys. The use of SHA-256’s mixing constants in SHA-512 shows a common cryptographic basis, which is typical in malware that aims to protect data or hide sensitive information before sending it to the command-and-control server.
The malware uses SHA-256, SHA-384, and SHA-512 cryptographic hashing algorithms, The SHA-256 method is used in the mixing process, whereas SHA-384 and SHA-512 are responsible for setting up the initial steps. These methods indicate that the malware could be using cryptographic hashing for encryption, ensuring data accuracy, or creating keys. The use of SHA-256’s mixing constants in SHA-512 shows a common cryptographic basis, which is typical in malware that aims to protect data or hide sensitive information before sending it to the command-and-control server.
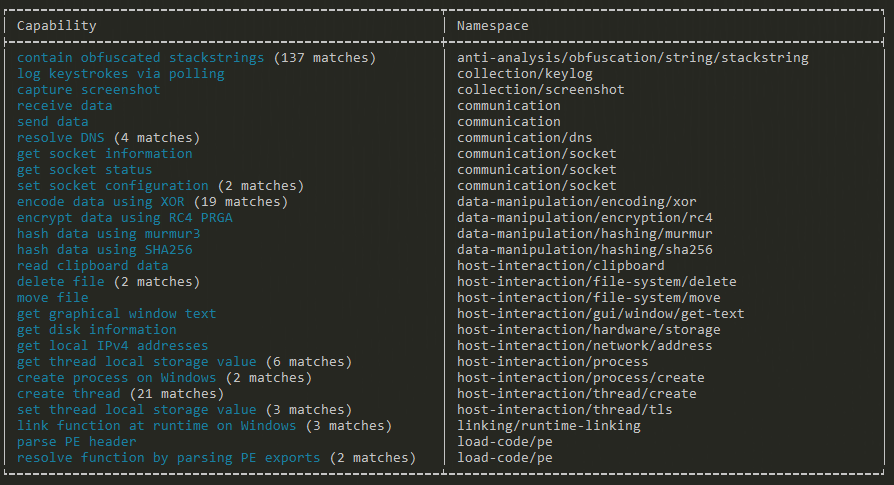
The malware has several capabilities identified through the CAPA tool. It contains obfuscated stackstrings, which makes it harder for people to understand.
It includes features for logging keystrokes and capturing screenshots, indicating its data collection capabilities.
The malware can communicate by sending and receiving data, resolving DNS, and managing sockets. It uses XOR for encoding data and employs RC4 for encryption, as well as hashing with murmur3 and SHA256, demonstrating cryptographic operations. Host interaction includes reading clipboard data, deleting and moving files, and interacting with graphical windows.
It also gathers system information, such as disk data and local IP addresses. The malware creates processes and threads on Windows and interacts with thread local storage. It dynamically links functions at runtime and parses PE headers, revealing its behavior in loading and executing code. All these features show that the malware is very complex and can do many things.
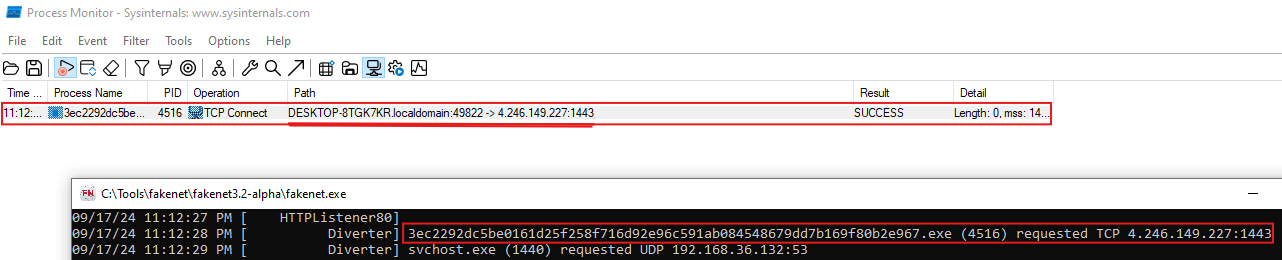
With Procmon, we found a network connection from DESKTOP-8TGK7KR.localdomain:49822 to 4.246.149.227:1443. This shows that the malware is connecting to a remote server using port 1443. This connection might be to a Command and Control (C2) server since the traffic is going from the infected computer to an outside IP address.
Advanced Analysis
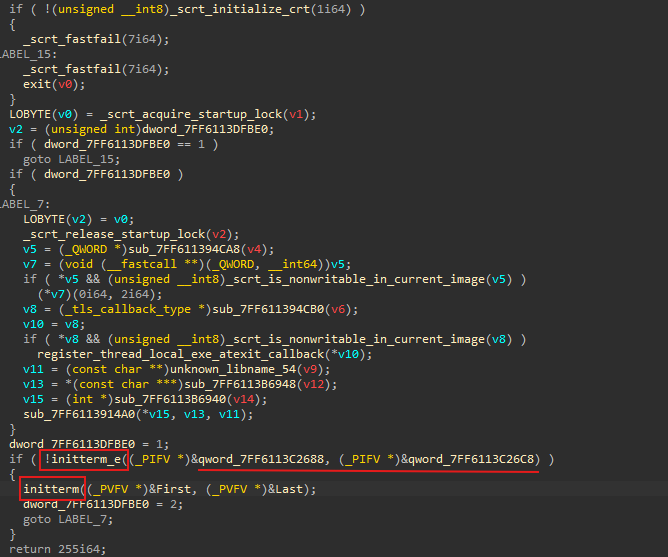
When I began analyzing the malware, I noticed that some code was executing before the main function. At first, I suspected this might be a TLS callback or a similar mechanism. But after more investigation, I found out that the malware was using a method called _initterm.
This technique is commonly used to run initialization routines before executing the main() function. The _initterm function goes through a list of function pointers for things like setting up global parts of the program or other initial tasks. which allows the malware to execute specific functionality early in the execution flow, such as anti-analysis or preparation of its environment.
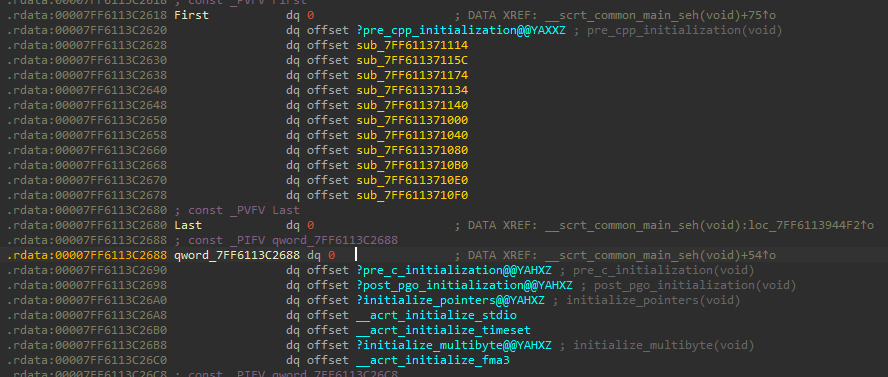
The malware executes its functionality through the _initterm mechanism, starting with pointers to various initialization functions. These functions are found in the .rdata section, which stores read-only data such as constants, and helps set up the environment before main() is executed.
The flow of execution indicates that the malware carefully sets up its environment early in the process,
The malware begins with resolving some functions that may be used in the next sections.
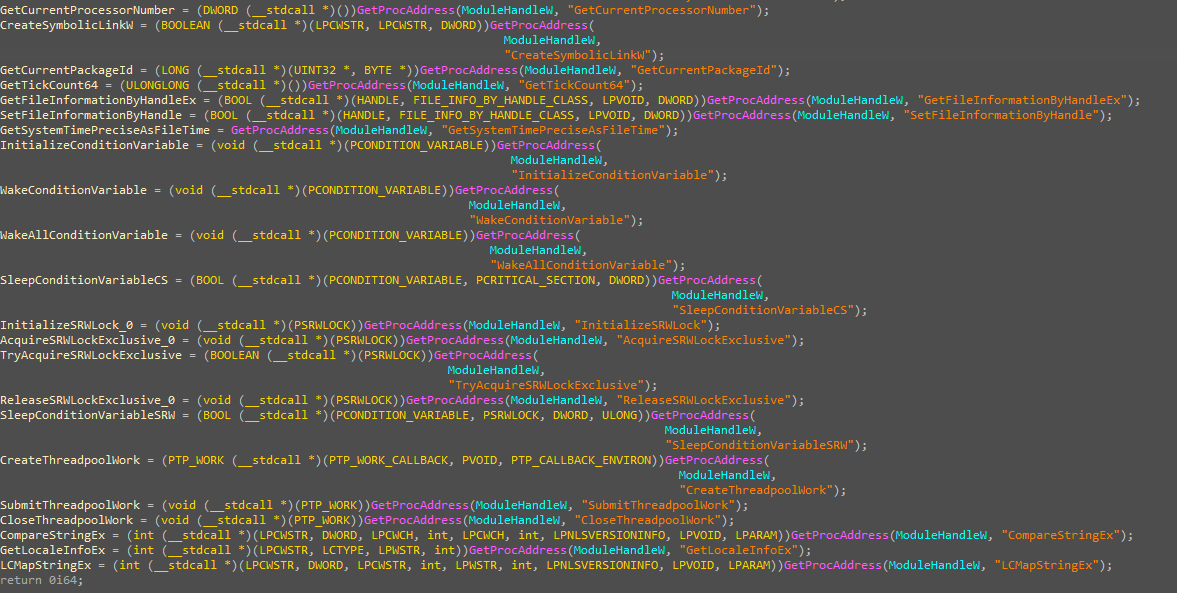
This indicates that the malware is gathering information about the system’s graphical display environment, including windows and monitors, which could be used for spying (such as capturing screenshots) or modifying display behavior.
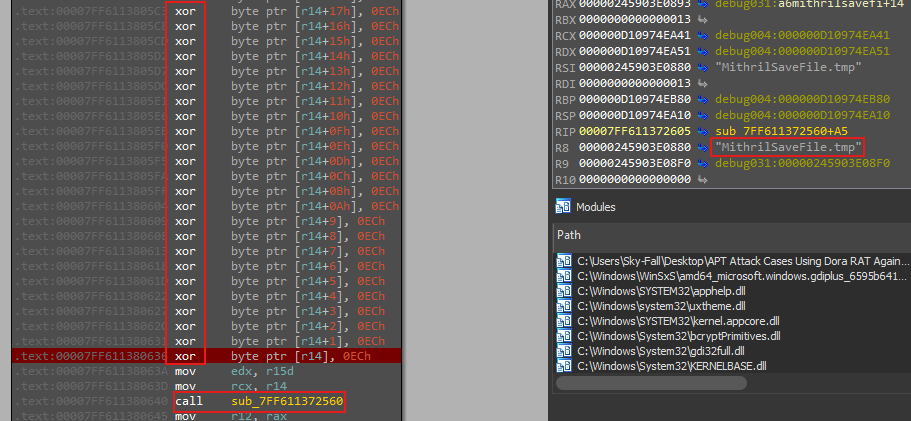
The malware begins its operations by decoding the string for the temporary file name using an XOR operation. This string, “MithrilSaveFile.tmp”, is likely obfuscated within the malware’s binary to avoid detection.
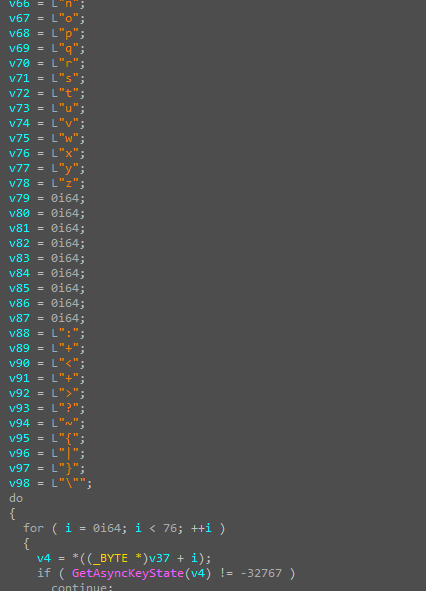
The code captures keystrokes in a loop using GetAsyncKeyState. It processes keypresses based on certain conditions, such as when modifier keys like Ctrl, Shift, or Alt are held. If Ctrl + V is detected, it retrieves data from the clipboard and stores it in memory.
The OpenClipboard function is called to access the clipboard. If successful, the code then calls GetClipboardData to retrieve data from the clipboard in a specific format, indicated by the value 0Dh (possibly Unicode text). If no data is returned, the code jumps to a section for error handling or cleanup. This sequence suggests that the code is involved in clipboard manipulation, likely for reading or extracting clipboard contents.

The malware first establishes a connection to its command and control (C2) server by creating and configuring a network socket. It then retrieves data from the temporary files created earlier, which contain sensitive or stolen information. The malware proceeds to send this data to the C2 server using appropriate network protocols.